Howdy folks!
Today, I am excited to announce a set of fantastic enhancements—based on your feedback—to the public preview of our combined registration experience for Multi-Factor Authentication (MFA) and self-service password reset (SSPR). This new registration experience enables users to register for MFA and SSPR in a single, step-by-step process. When you deploy the preview experience for your organization, users can register in less time and with fewer hassles. In addition, the new My Profile experience provides users with a more streamlined and easier-to-navigate experience for reviewing and updating their profile info.
Keep reading to learn more about these enhancements!
Streamlined registration experience
Since we released the combined registration public preview, we received a lot of great feedback from our customers on how to make this experience even better for their users. One of the most common pieces of feedback we received was that the registration experience needs to be even easier, especially on mobile devices. To address this, we streamlined the experience so that users can simply click through each step to register their security info.
Now when users are required to register while signing in, they’ll see the following experience:
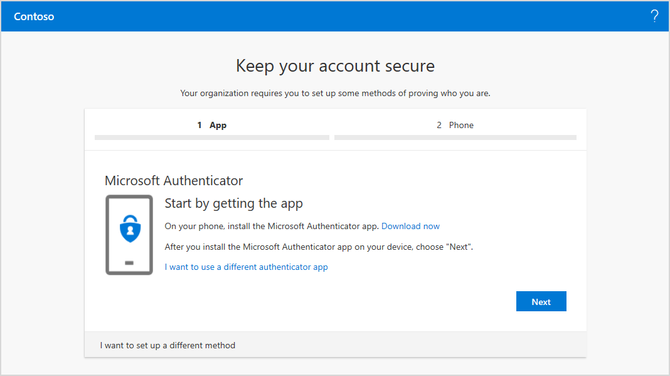 Enhanced step-by-step registration experience.
Enhanced step-by-step registration experience.
Once a user completes registration, they’ll see an overview of what they registered to confirm the information is correct and then they’re back to work!
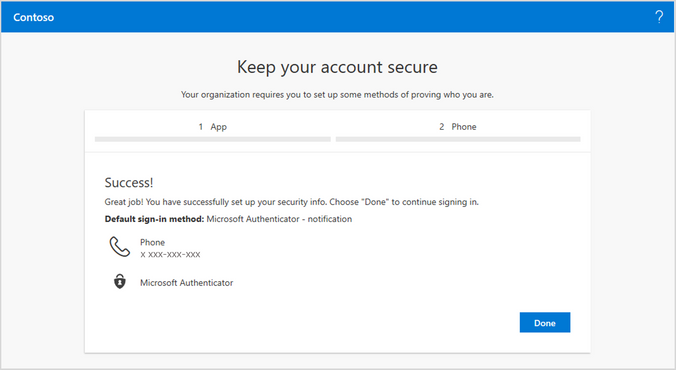 Overview of the security info setup by the user.
Overview of the security info setup by the user.
To learn more about the enhanced security info registration experience, check out our admin documentation and user documentation.
New My Profile experience
When you enable the enhanced security info registration experience for your users, they’ll also have the new My Profile experience, now in public preview. My Profile is the central location where users manage their identity including security info, devices, and more.
 The new My Profile experience.
The new My Profile experience.
From the Security info page, users can easily change their phone number or choose a different default method. From here they can also add, delete, or change a method.
 Manage security info.
Manage security info.
To learn more about the new My Profile experience, check out our documentation.
Try it out!
To enable the enhanced security info registration experience and the new My Profile experience for your users, follow these steps:
- Sign into the Azure portal as a global administrator or user administrator.
- Browse to Azure Active Directory > User settings > Manage settings for access panel preview features.
- Under Users you can use the preview features for registering and managing security info – refresh, you can choose to enable for a Selected group of users or for All users.
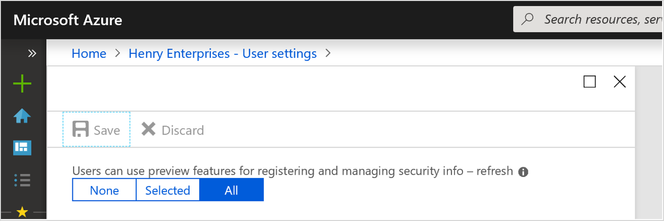 Enable the enhanced security info registration experience.
Enable the enhanced security info registration experience.
Users who are enabled for the old security info registration experience will continue to see that experience until you enable them for the refreshed experience. This means that if you have enabled the non-refreshed experience, you will have the ability to enable and disable that experience.
If a user is enabled for both the old experience and the enhanced experience, they will see the enhanced experience.
As we move forward, we will continue to make improvements and fixes in the enhanced registration experience. If your users are using the old experience, we recommend moving them to the enhanced experience as soon as possible so that they have access to the latest updates.
Please submit your ideas to our feedback forum and we will review and respond to them. You can also let us know what you think in the comments below. As always, we’d love to hear any feedback or suggestions you have.
Best Regards,
Alex Simons (@Alex_A_Simons )
Corporate VP of Program Management
Microsoft Identity Division