- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Continuous Access Evaluation in Azure AD is now in public preview!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
A few months back, we introduced Continuous Access Evaluation (CAE) for tenants who had not configured any Conditional Access policies. CAE provides the next level of identity security by terminating active user sessions to a subset of Microsoft services (Exchange and Teams) in real-time on changes such as account disable, password reset, and admin initiated user revocation.
Today marks an important milestone in bringing this capability to everyone – now CAE is available in public preview for Azure AD tenants who have configured Conditional Access policies. Microsoft services, like Exchange and SharePoint, can terminate active user sessions as soon as a Conditional Access policy violation is detected. More Microsoft services, such as Dynamics and Azure, will be enabled in the future. You can turn on CAE to improve the security posture in your tenant with just a few clicks!
Getting started
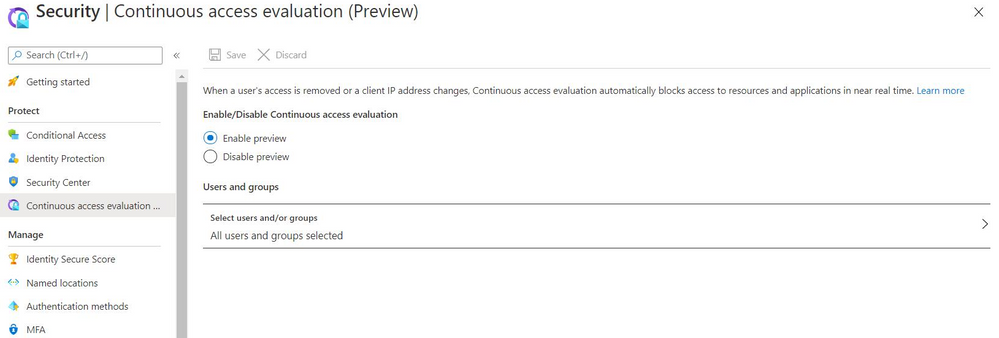
For tenants with Azure AD Premium subscription, you can configure CAE in our portal by going to Azure Active Directory -> Security -> Continuous Access Evaluation. There you can Enable Preview and you can also choose to configure this initially for a select set of users and groups.
If there are no conditional access policies configured in your tenant. CAE is already enabled for all users in your tenant and there are no additional actions you need to take. This is enabled even if your tenant has no Azure AD premium subscription.
To learn more about these changes, check out here: continuous access evaluation.
As always, we’d love to hear any feedback or suggestions you have. Let us know what you think in the comments below or on the Azure AD feedback forum.
Best regards,
Alex Simons (twitter: @alex_a_simons)
Corporate Vice President Program Management
Microsoft Identity Division
Learn more about Microsoft identity:
- Related Articles: Continuous Access Evaluation
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.