- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Conditional Access GPS-based named locations now in public preview
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Today, I am excited to share how you can improve your Conditional Access policies and ensure compliance with data regulations thanks to the public preview of GPS-based named locations. This feature helps admins strengthen their security and compliance posture and allows them to restrict access to sensitive apps based on the GPS location of their users.
I have asked Olena Huang, a PM on the Identity team, to tell you more. Let us know what you think!
Alex Weinert
-------------------------------------
Hello,
With the public preview of GPS-based named locations, admins can refine their Conditional Access policies by determining a user’s location with even more precision. GPS-based named locations allow you to restrict access to certain resources to the boundaries of a specific country. Due to VPNs and other factors, determining a user’s location from their IP address is not always accurate or reliable. Leveraging GPS signals enables admins to determine a user’s location with higher confidence. This is especially helpful if you have strict compliance regulations that limit where specific data can be accessed.
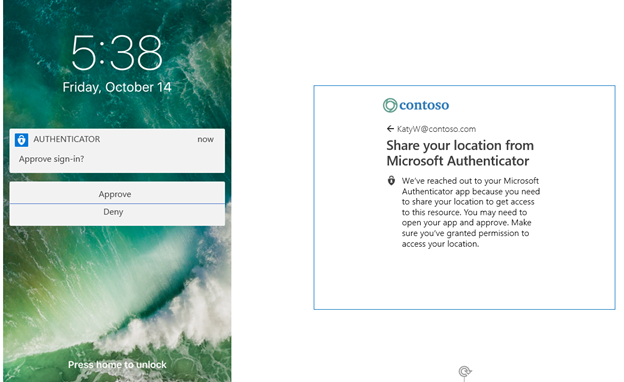
When the feature is enabled, users will be prompted to share their GPS location via the Microsoft Authenticator app during sign-in.
Create a policy to allow or restrict access based off a user’s GPS location
There are two simple steps:
- Create a GPS-based named location.
- Create or configure Conditional Access with this named location.
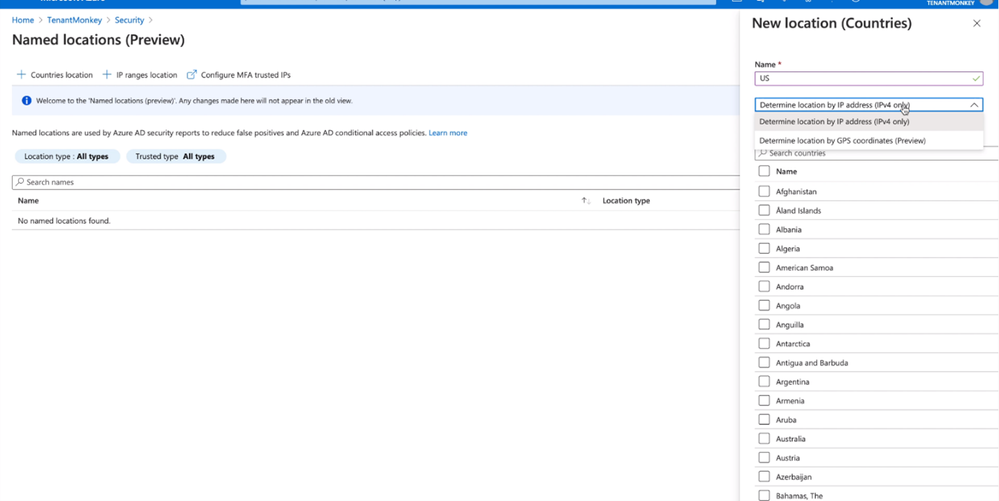
You’ll first need to create a countries named location and select the countries where you want the policy to apply. Configure the named location to determine the location by GPS coordinates instead of by IP address.
Next, create a Conditional Access policy to restrict access to selected applications for sign-ins within the boundaries of the named location.
For more information, check out our admin documentation or our Graph API documentation.
Test out the location-sharing experience
First, make sure you have the Microsoft Authenticator app installed and set up with your test account.
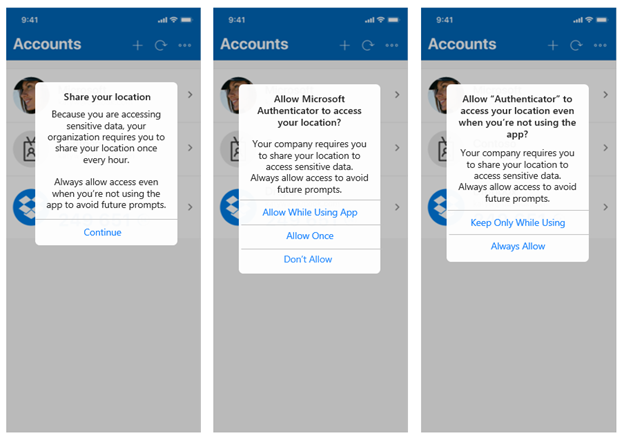
Next, try to access the files or data restricted by the Conditional Access policy. You’ll be prompted to share your geolocation from the Authenticator app.
The first time you encounter this prompt, you will need to grant location permissions to the Authenticator app.
iOS
Android
For the next 24 hours, your location will be shared silently once per hour from that device, so you won’t keep getting notifications.
After 24 hours, you will be re-prompted when trying to access the same resource. However, you will not need to grant permissions again (unless you’ve disabled them).
If you have questions, check out our FAQ page.
We’d love to hear from you! Feel free to leave comments below or reach out to us on Twitter.
Learn more about Microsoft identity:
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.