- Home
- Security, Compliance, and Identity
- Microsoft Entra
- CBA, MFA, and AADSTS54008 Certificate is not supported as first factor
CBA, MFA, and AADSTS54008 Certificate is not supported as first factor
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 24 2022 08:50 AM - edited May 24 2022 09:22 AM
Greetings All,
I'm trying to get CBA MFA working for Azure AD, exchange online specifically, but I can't get past the following error: AADSTS54008: Multi-Factor authentication is required and the credential used (Certificate) is not supported as a First Factor. Obviously, I have something configured incorrectly. Does anyone have a suggestion?
What I'm trying to achieve is have our users login to Outlook online with their username and password and then have the option to select a user certificate as their second form of authentication.
Regards,
KB
- Labels:
-
Azure Active Directory (AAD)
-
MFA
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 24 2022 09:24 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 24 2022 09:44 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 05 2022 04:47 AM
Did you sort this out?
I encounter the same error in my test tenant, the user certificate is successfully mapped to my user.
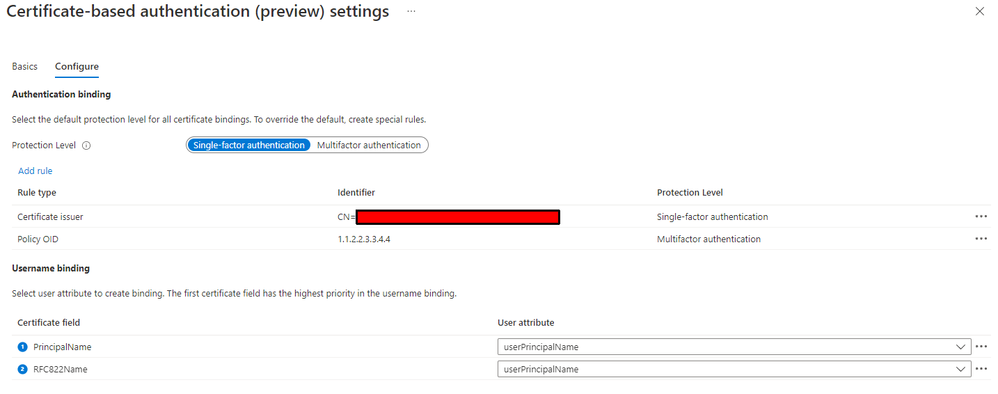
If I switch the protection level over to "multifactor authentication" I get signed in without MFA prompt.
When I attempt to sign in with the protection level set to "single-factor authentication", sign-in fails with the error AADSTS54008: Multi-Factor authentication is required and the credential used (Certificate) is not supported as a First Factor. Contact your administrator for more information.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 05 2022 05:28 AM
@manshellstrom Yes sir. The settings below work as desired for my tenant.
Be sure to check that you don't have any of policies in your tenant that may be conflicting.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 20 2022 01:04 PM
You ever figure this out? I am having the same issue. I only want the cert to be used as a single factor, and have the toggle and issuer rule set as such. I have no policy oid rule for MFA. When entering upn, I choose log in with a certificate, and get the same error you cited. My expectation is that the cert replaces password, and the user will require mfa through their default method, which is authenticator app.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 22 2022 08:12 AM
No, and my best guess is that the service is broken.
You and I are reaching for the exact same functionality, but it seems you can't get this working without a certificate policy that can be mapped in the configuration.
We'are also missing the posibility to use OCSP in favor of CRL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2022 09:43 AM
FYI it is misleading, but if you look at the Microsoft documentation on CBA, the only way to do MFA with a cert is to add a Policy O.I.D rule that checks for a value in your cert. The cert then acts as the first factor and second factor. There seems to be no other MFA options supported with CBA yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2022 09:47 AM - edited Aug 23 2022 09:51 AM
Also, if you you are getting that MFA sign in error regarding "first factor", and want it to work with CBA, you have to disable MFA enforcement at the user level and make sure they aren't included in any other conditional access policies that require MFA. Just make sure you have other user account protections such as additional Conditional Access Policies based on device or IP Range etc.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2022 10:45 AM - edited Aug 23 2022 10:46 AM
So you're saying that limiting its use to "single factor" implies having to have MFA disabled entirely for the user, while enabling it for "multi-factor" basically makes this the equivalent of a FIDO key, minus the hardware security and pin? It simply can't be configured as the equivalent of any other form of single factor, so some other factor is needed to go along with it in order to authenticate? If so, that's pretty weak..
I guess this part of the documentation made me think otherwise-- thinking the experience would be cert replaces password, then the user can choose from mobile app, passcode, fido key, etc as a 2nd factor..
"If a unique user is found and the user has a conditional access policy and needs multifactor authentication (MFA) and the certificate authentication binding rule satisfies MFA, then Azure AD signs the user in immediately. If the certificate satisfies only a single factor, then it requests the user for a second factor to complete Azure AD Multi-Factor Authentication."
https://docs.microsoft.com/en-us/azure/active-directory/authentication/concept-certificate-based-aut...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2022 11:04 AM - edited Aug 23 2022 11:14 AM
I saw the same article and it contradicts the way I interpret this article and my testing so far:
"The policy OID in the certificate matches the configured value of 1.2.3.4 and it will satisfy multifactor authentication. Similarly, the issuer in the certificate matches the configured value of CN=ContosoCA,DC=Contoso,DC=org and it will satisfy single-factor authentication."
"Because policy OID rule takes precedence over issuer rule, the certificate will satisfy multifactor authentication."
https://docs.microsoft.com/en-us/azure/active-directory/authentication/how-to-certificate-based-auth...
In my testing, with password as first factor, cert is not available as second factor. Windows Hello, FIDO/yubikey, Authenticator passwordless act as 1st factor and 2nd factor so can't be used with cert. Phone sign in can't be used with MFA. If MFA is enforced on the user account, Cert auth will fail with the "first factor" error message you guys are getting.
The documentation says unless the policy information is included in the cert and there is a Policy OID rule to verify it, MFA will fail. I have yet to verify this works as I have not been able to get the "certificate policies" identifiers in our certs yet.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2022 11:38 AM
I'll also need to check to see if phone sign-in is enabled on my test account, and if so try without. It would be nice if Microsoft could give some clarity on the confusing documentation. If it truly can't be used as a "single-factor" --meaning it replaces password but user still needs at least some other factor -- they are ignoring the most obvious and beneficial use case -- eliminating the use of a password while still enforcing another factor of security.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 23 2022 12:22 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 11 2022 05:25 PM - edited Oct 11 2022 05:56 PM
@mikey365: "Currently, password can't be disabled when CBA is enabled and the option to sign in using a password is displayed.": https://learn.microsoft.com/en-us/azure/active-directory/authentication/concept-certificate-based-au... -> So your suggestion can not be done at the moment. Would be the end game though in my view.
It's like @jroth710 says: "They are ignoring the most obvious and beneficial use case -- eliminating the use of a password while still enforcing another factor of security."
When you go to the Azure Portal, you can now add authentication strengths policies: https://portal.azure.com/#view/Microsoft_AAD_IAM/AuthenticationMethodsMenuBlade/~/AuthStrengths. What we need is the "Certificate Based Authentication (Single Factor) + Microsoft Authenticator (Push Notification)" combination under 'Multifactor authentication'. I'll keep hoping
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 15 2023 11:19 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 17 2023 06:50 AM
Hi,
you have to configure under multifactor policy that is passwordless only, after that with all cba setup everthing will work.
I am ataching print screens from my environment.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2023 01:49 PM
a) enforce MFA (through CA) or
b) use CBA as a multi factor method (in CBA settings)
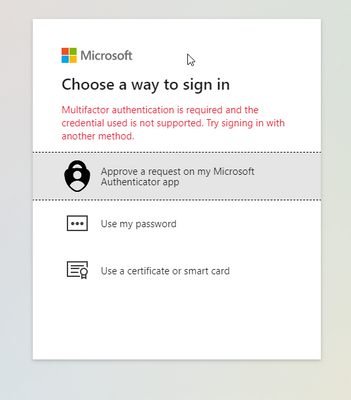
the login process breaks with "Multifactor authentication is required and the credential used is not supported. Try signing in with another method."
What I just want to achieve is:
- User logs in with username
- CBA is selected as first factor (user selects the certificate configured)
- Authenticator App is used as second factor (user types in the numbers at the prompt)
If you (or anyone else) have a way to get this to work, I am very interested;-)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 24 2023 02:14 PM
- User logs in with username
- Authenticator App is used as first factor (because passwordless is selected) (user types in the numbers at the prompt)
- CBA is selected as second factor (user selects the certificate configured)
In my setup CBA is configured with 'multi factor' as protection level
CA has two rules:
- one regular 'MFA required' (just like always)
- a second one (new policy!) requiring 'phishing resistant MFA' with 'Require authentication strength (Preview)' grant
That's Great!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 25 2023 03:02 AM
This way it worked first cba snd than numner matching from passwordless sign in :)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Mar 27 2023 12:46 PM
To top it of I also use a 'Location based' CA rule, so even when my full browser profile gets hijacked (including session tokens) it won't work, off my private network.
Still I would like to see browsers encrypting their cookie database with some machine specific key, to make the cookies not work if they are used on a different machine. It feels very strange this massive security hole has gone unplugged for so long...
Cheers!