- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Azure AD Password Protection is now generally available!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks!
Many of you have already been using Azure AD Password Protection in public preview. Azure AD Password Protection allows you to eliminate easily guessed passwords and customize lockout settings for your environment. Using it can significantly lower the risk of compromise by a password spray attack. Best part, it’s available for both cloud and hybrid environments. We’d like to thank all the customers who have tried the preview and provided us valuable feedback.
Today, I’m excited to announce this feature is now generally available!
To help users avoid choosing weak and vulnerable passwords, we updated the banned password algorithm. Using the global banned password list that Microsoft updates and the custom list you define, Azure AD Password Protection now blocks a wider range of easily guessable passwords.
Read our detailed documentation to learn more about how password strength is evaluated and how Azure AD Password Protection can help block weak passwords in your organization.
Getting started
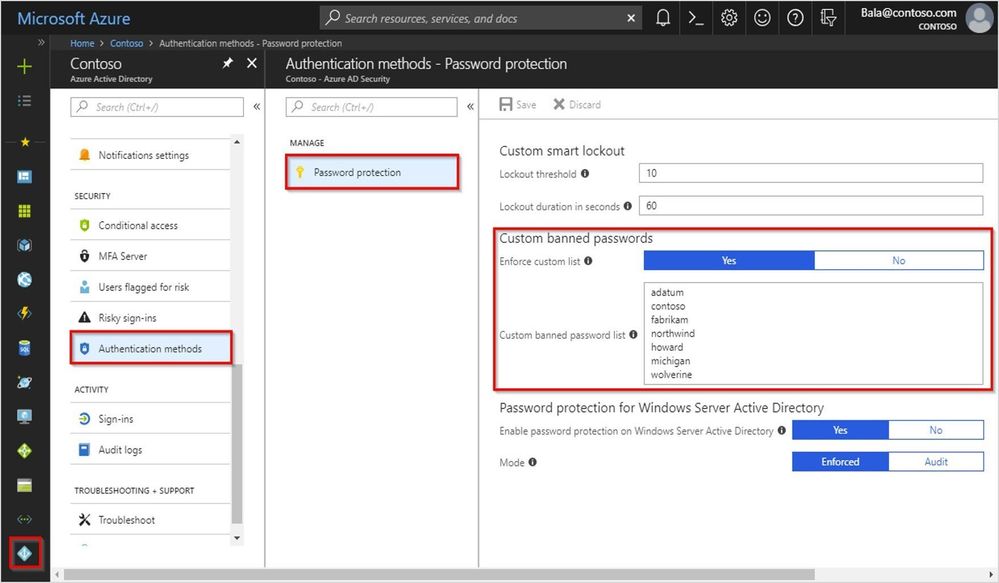
Azure AD Password Protection can easily be configured from the Azure AD portal. First, sign-in to Azure Portal with a global administrator account. Next, navigate to the Azure Active Directory and then to the Authentication methods blade, where you’ll see Password protection, as shown below:
Configure Azure AD Password Protection
- Customize your smart lockout threshold (number of failures until the first lockout) and duration (how long the lockout period lasts).
- Enter the banned password strings for your organization in the textbox provided (one string per line) and turn on enforcement of your custom list. We strongly recommend this for all customers that have multiple brands and products that their users identify with.
- Extend banned password protection to your Active Directory by enabling Password Protection for Windows Server Active Directory. Start with audit mode, which runs Password Protection in “what if” mode. Once you’re ready for enforcing Password Protection, flip the mode to Enforced to start protecting users by preventing any weak passwords being used.
Note: All synced users must be licensed to use Azure AD Password Protection for Windows Server Active Directory.
Protecting your on-premises environment
To use Azure AD Password Protection on our Windows Server Active Directory, download the agents from the download center and use the instructions in the Password Protection deployment guide.
Once a global administrator has enabled Password Protection for Windows Server Active Directory, security administrators can take it from there and complete the registration for both proxy agents and Active Directory forests. Both the domain controller agent and the proxy agent support silent installation that can be leveraged using various deployment mechanisms like SCCM.
Note: Preview customers MUST update the agents to the latest version (1.2.125.0 or higher) immediately. The current agents will stop working after July 1, 2019.
As always, we're eager to hear from you! Still have more questions for us? Email aadppfeedback@microsoft.com. We look forward to hearing your feedback!
Best regards,
Alex Simons (@Alex_A_Simons )
Corporate VP of Program Management
Microsoft Identity Division
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.