- Home
- Security, Compliance, and Identity
- Microsoft Entra
- Azure AD Connect (AADC) V2 upgrade case-by-case scenario
Azure AD Connect (AADC) V2 upgrade case-by-case scenario
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Sep 25 2021
07:14 AM
- last edited on
Jan 14 2022
03:24 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 25 2021
07:14 AM
- last edited on
Jan 14 2022
03:24 PM
by
TechCommunityAP
Microsoft strongly recommends upgrading to AADC 2.0 or later by June 2022. Changes in AADC 2.X version can be checked at the following link.
What is Azure AD Connect v2.0? | Microsoft Docs
However, the actual customer's AADC server infrastructure is very diverse, so there are many concerns in making an upgrade plan. So, I would like to share a possible upgrade plan considering the customer's AADC server infrastructure.
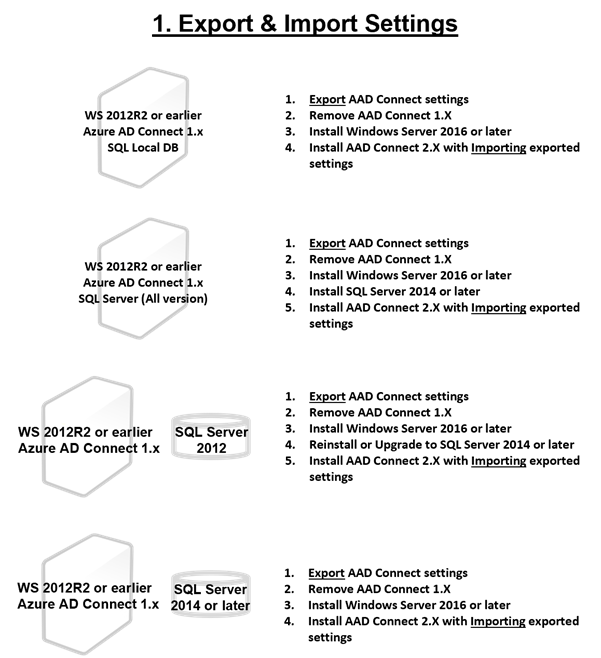
Things to consider in advance
First of all, if the Windows Server version of the AADC server is 2012R2 or earlier, OS reinstallation is required. In-Place Upgrade for Windows Server with AADC is not supported.
I also tried OS In-Place Upgrade once, the sync of AADC was normal, but I couldn't change the configuration at all.
It is also important to consider SQL Server. When using LocalDB, it is automatically upgraded to SQL 2019 Local DB within the upgrade process. However, if a separate SQL Server 2012 or earlier is used, reinstallation or upgrade to SQL Server 2014 or higher is required. Actually, a higher version would be better.
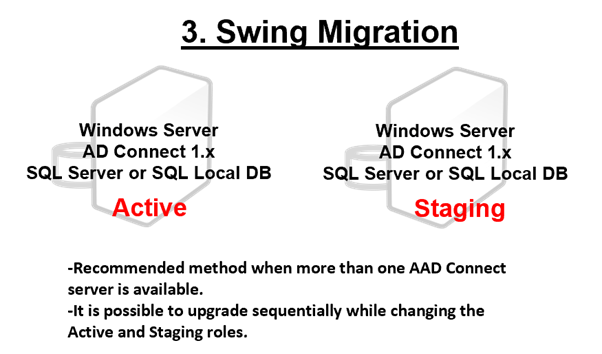
Three ways to upgrade
- Export & Import Setting: Create an export file including the current setting information and import this file when reinstalling AADC 2.X. In fact, this method can be used in all conditions, but it will also be necessary to verify whether it is normal after upgrading. How to import and export Azure AD Connect configuration settings | Microsoft Docs
- In-Place Upgrade : This is the most convenient way to migrate using the Wizard. Azure AD Connect: Upgrade from a previous version | Microsoft Docs
- Swing Migration: This is the recommended method to minimize the impact of changes due to the upgrade, but requires two or more AADC servers. Azure AD Connect: Upgrade from a previous version | Microsoft Docs
Based on the current AADC server infrastructure, which of the three upgrade methods could be chosen? The scenarios in the figure below are not absolute. If you have a better scenario, please share.
- Labels:
-
Azure Active Directory (AAD)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 06 2022 02:38 AM
Hi @PyungraeCho
Thank you for your article, it was very useful for me. Any way I have a doubt: I upgraded successfully AD Connect from 1.6 to 2.0.91 in a Windows Server 2019. I expected the AD Connect 2.0.91 wizard to show me the error of not using TLS 1.2, because the powershell scripts show me that the corresponding entries were not defined, but I could install it with out errors. I would really like to know if the server is using TLS 1.2 or not. I've googled and it is supoosed that Windows Server 2016 and newer versions use TLS 1.2 by default but I'm confussed because the scripts to check it shows me another think, and I haven't run any script to disable it.
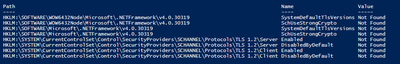
I attach the results of scripts privided in https://docs.microsoft.com/en-us/azure/active-directory/hybrid/reference-connect-tls-enforcement ...
Path Name Value
---- ---- -----
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319 SystemDefaultTlsVersions Not Found
HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319 SchUseStrongCrypto Not Found
HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 SystemDefaultTlsVersions Not Found
HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319 SchUseStrongCrypto Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server DisabledByDefault Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client Enabled Not Found
HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client DisabledByDefault Not Found
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 06 2022 08:52 AM - edited Feb 06 2022 08:58 AM
Hi, @joseparra.
As far as I know, even in AzureAD Connet 1.X version, TLS 1.2 was already used unless disabled on the server. Also, TLS 1.2 is already enabled by default from Windows 2012 or later.
Protocols in TLS/SSL (Schannel SSP) - Win32 apps | Microsoft Docs
AzureAD Connect Server requires Windows 2016 or later. (In fact, Windows 2016 server or higher is required because SQL Server Express 2019 is required for AzureAD Connect). Then, shouldn't there be no errors about the TLS 1.2 requirements? But when I upgraded, I got an error like the following picture.
But you completed the upgrade on Windows 2019 without any errors. Right?
Perhaps there was an issue in checking the TLS 1.2 version when upgrading. You can find these in the document below. Up to version 2.0.10.0, there was a known issue with the TLS 1.2 check.
Azure AD Connect: Version release history | Microsoft Docs
And this issue was fixed in version 2.0.25.1. (You used the latest 2.0.91.0 installer. )
Azure AD Connect: Version release history | Microsoft Docs
Even when installing a new AzureAD Connect rather than an upgrade, if you use the 2.0.10.0 or lower version of the installation file, you can check the TLS 1.2 error, but in versions higher than this, the installation is completed without any errors like your upgrade.
Regarding TLS 2.0 in AzureAD Connect Upgrade, I also think that the documentation does not explain exactly, but this is my opinion based on test results.
""As a result, the TLS 1.2 force activation script was not needed unless it was previously disabled. And there was an error checking this in the upgrade process and it was fixed. If there are no errors when upgrading with the latest installer now, there is no problem." "
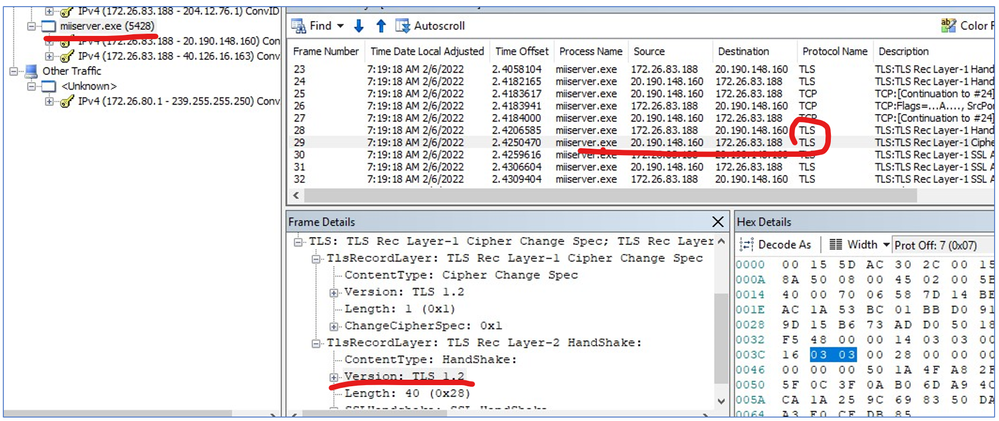
If you want to know if TLS 1.2 is really being used, you can check the network packets.