- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Azure AD Certificate-Based Authentication now in Public Preview
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
Today I'm very excited to announce the public preview of Azure Active Directory certificate-based authentication (Azure AD CBA) across our commercial and US Government clouds!
In May of 2021, the President issued Executive Order 14028, Improving the Nation’s Cybersecurity calling for the Federal Government to modernize and adopt a Zero Trust architecture including phish resistant multi-factor authentication (MFA) for employees, business partners, and vendors.
“Incremental improvements will not give us the security we need; instead, the Federal Government needs to make bold changes and significant investments in order to defend the vital institutions that underpin the American way of life.”
– President Biden, Executive Order 14028
Based on our experience working with Government customers, PIV/CAC cards are the most common authentication method used within the Federal Government.
While valuable for all customers, the ability to use X.509 certificate for authentication directly against Azure AD is particularly critical for Federal Government organizations using PIV/CAC cards and looking to easily comply with the Executive Order 14028 requirements.
Vimala Ranganathan, Product Manager on our Identity Security team, will walk you through the details.
Best Regards,
Alex Simons (Twitter: @Alex_A_Simons)
Corporate Vice President Program Management
Microsoft Identity Division
----------------------------------------------------------------------------------------------------------
Hi everyone,
I’m Vimala from the Identity PM team and I am excited to walk you through Azure AD CBA.
As part of our commitment to the US Cybersecurity Executive Order, Azure AD CBA helps Government customers easily meet phishing-resistant MFA authentication using the PIV/CAC cards. Azure AD users can authenticate using X.509 certificates on their smartcards or devices directly against Azure AD for browser and application sign-in.
Key benefits include:
- Higher security with phish resistant certificate-based authentication (the majority of the identity attacks are related to passwords)
- Easily meet the Executive Order 14028 requirements for phish resistant MFA
- Eliminate costs and risks associated with on-premises federation infrastructure
- Simplified management experience in Azure AD with granular controls
SAP has been a great partner on the Azure AD CBA journey and provided feedback that was critical to shaping the public preview today!
“CBA is historical in the heart of SAP Products. Certificate Based Auth is in use at SAP since 1999 and has been migrated and adopted multiple times, having these capabilities natively in Azure AD also allows us in the long run to retire our ADFS where Azure AD is the last Federation endpoint we still have.” - Sven Frank, identity architect at SAP
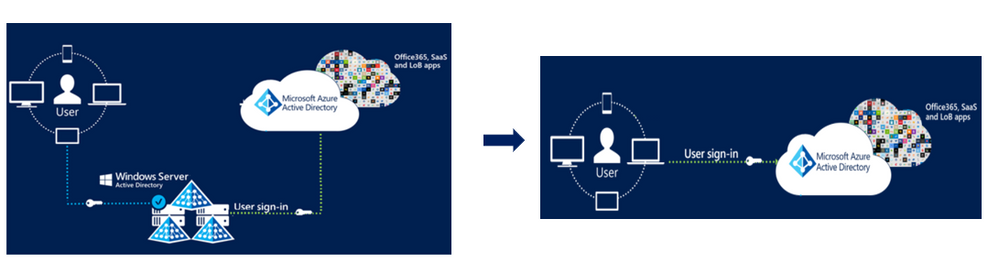
What is Azure AD Certificate-Based Authentication (Azure AD CBA)?
As you might be aware, authentication using X.509 certificates against Azure AD used to require a federated identity provider (IdP) such as AD FS. With the Azure AD CBA Public Preview today, customers will be able to authenticate directly against Azure AD without the need for a federated IdP.
Certificate-based authentication method management
The picture below shows the steps for an admin to enable CBA.
Check out our public documentation to learn more: http://aka.ms/AADCBA
End-User Experience
As an end-user, once you type in the User Principal Name (UPN), you will see the “Sign in with a certificate” link on the password screen.

You will be prompted to select the correct client certificate and that’s it – you will get authenticated to the application.
Note: If CBA is enabled on the tenant, all users in the tenant will see the link to ‘Sign in with a certificate’ on the sign-in page. However, only the users in scope for CBA will be able to authenticate successfully against Azure AD and the rest will see a failure.
What’s next
We're working on more great features like Windows smart card logon, CBA as a second factor of authentication, removal of limits on trusted issuer list, and Certificate Revocation List (CRL).
As always, please keep the feedback loop open by reaching us at Azure Active Directory Community!
You can learn more about Microsoft’s commitment to Executive Order 14028 here.
Thanks,
Vimala
Learn more about Microsoft identity:
- Related Articles: http://aka.ms/AADCBA
- Return to the Azure Active Directory Identity blog home
- Join the conversation on Twitter and LinkedIn
- Share product suggestions on the Azure Feedback Forum
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
