- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Azure AD B2C now has JavaScript customization and many more new features
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy, folks!
I’m excited to announce that customizing your user flows with Azure AD B2C is now easier than ever with more features, including the general availability of our new portal experience and custom password complexity option. I’m also excited to share the public preview of the following features as well:
- User templates—Create beautiful authentication experiences using default templates as a starting point for your branded UI.
- JavaScript and page layout versions—Add more functionality to all your Azure AD B2C pages with your own custom JavaScript.
- Identity provider access token passthrough—Send the access token from social identity providers back to the application.
Read on for more details and try out these features through the Azure portal.
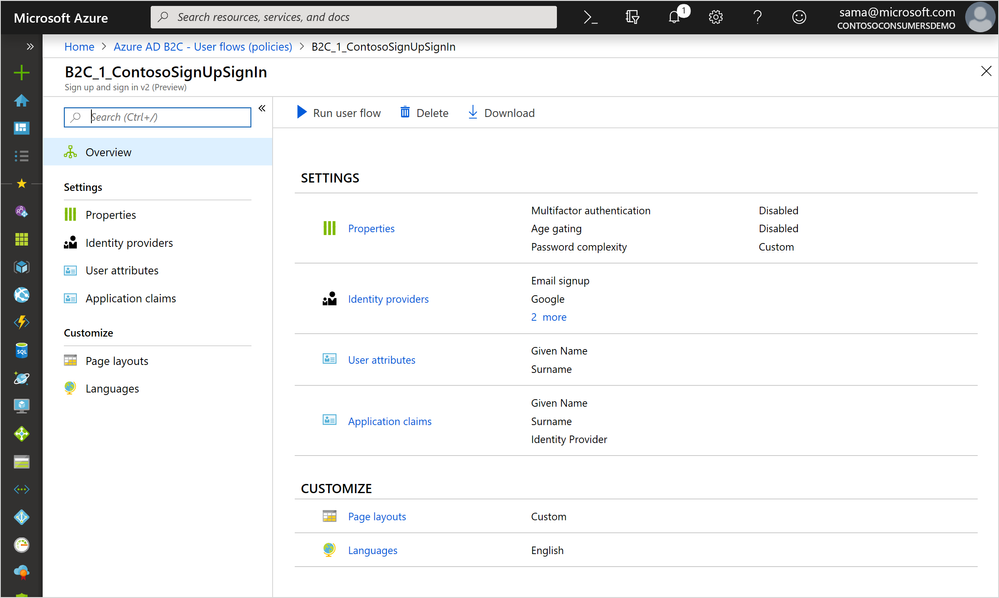
New portal experience
With the new portal experience, you can easily create your next user flow. First released back in November, we're now making it generally available by releasing to all directories! We’ve seen some great improvements overall from your usage including:
- Decreased task completion times for creating and editing user flows.
- Higher completion rates when creating or updating existing user flows.
Users have also reported that they love using run user flow in place with the changes they’re making.
If you haven't had a chance to use the new UI yet, go to the Azure portal, and then go to the Azure AD B2C extension. Ensure you’re in your B2C directory and select User flows from the left-hand menu.
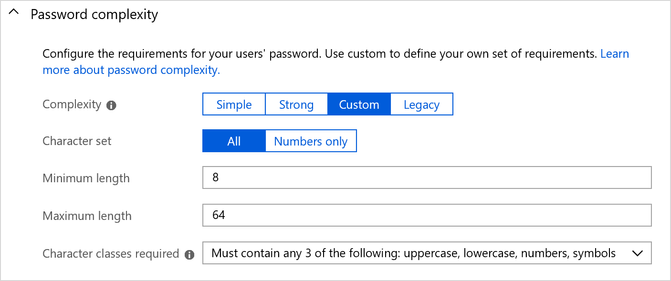
Custom password complexity
We’ve been cooking up this feature for a long time and are pleased that it’s now generally available. You can use this feature to lower password requirements to reduce user friction in signing up or increase the password complexity required to meet your compliance guidelines. Whatever requirement you enforce, you can help your users by having error messages that dynamically change as requirements are met. By default, password complexity is set to Strong for all newly created user flows. Read Configure complexity requirements for passwords in Azure Active Directory B2C to learn more.
New user templates
The new user templates, in public preview, allow you to easily get started with creating beautiful sign in and sign up experiences for your users. You can access these templates through Page layouts. In the command bar, select Ocean Blue or Slate Gray. We’ve also hosted sample templates to help you get started.

JavaScript and page layout versions in public preview
We heard from you that you want to customize your sign in and sign up experiences using your own JavaScript and here you go! To use JavaScript, we enabled page layout versions. This lets you control the content on the page provided by the Azure AD B2C service and opt into updated versions. By having this control, you can use JavaScript reliably and ensure predictable behavior. Read about using JavaScript and page contract versions in a user flow to learn more.

Identity provider access token passthrough in public preview
We’re making it even easier for your application to leverage the power of social identity providers and their APIs. When a user signs in using an identity provider, like Facebook, your application can get the identity provider's access token passed through as part of the Azure AD B2C token. You will be able to use this access token to call the identity provider’s API, such as the Facebook Graph API. Read Pass an access token through a user flow to your application in Azure Active Directory B2C to learn more.
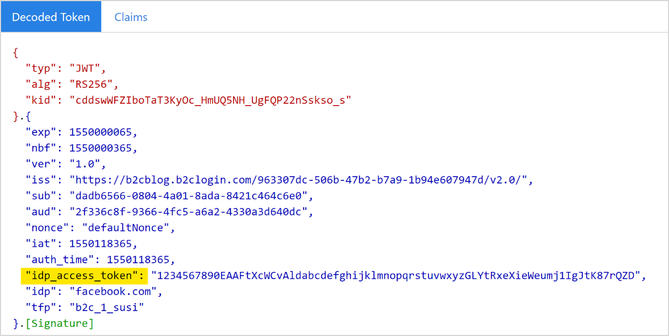
There’s a lot going on here! If you have any questions or feedback about these features, send us an email at aadb2cpreview@microsoft.com. You can also let us know what you think in the comments below. As always, we’d love to hear any feedback or suggestions you have.
Best regards,
Alex Simons (@Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.