- Home
- Azure
- Apps on Azure Blog
- Announcing Secure Baseline accelerators for multi-tenant App Service deployments
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Microsoft Azure is excited to announce a new Secure Baseline scenario in the Landing Zone Accelerator for Azure App Service. This new scenario provides a simple, secure starting point to build new apps in the multi-tenant cloud platform, or to modernize your existing web apps running on-premises or in Virtual Machines with Azure App Service.
Landing Zone Accelerators accelerate deployment of Azure App Service at scale
Azure App Service is an easy way to deploy and manage web apps at scale, making it a no-brainer for developers looking to streamline their application deployments in the cloud and be more successful at any skill-level.
Landing Zone Accelerators were built to fast-track your production-grade deployments to Azure. These accelerators include a set of best practices, architectural guidance, and a customizable infrastructure-as-code template known as a reference implementation. This new Secure Baseline scenario empowers developers with the confidence to evaluate critical infrastructure decisions in multi-tenant Azure App Service deployments.
If you run apps in a fully isolated, dedicated environment at high scale, check out the resources below for the Azure App Services Environment scenario. This scenario guides you through running a web-app workload for line-of-business applications in a secure configuration.
New scenario and features anchored by a security strategy your web app needs
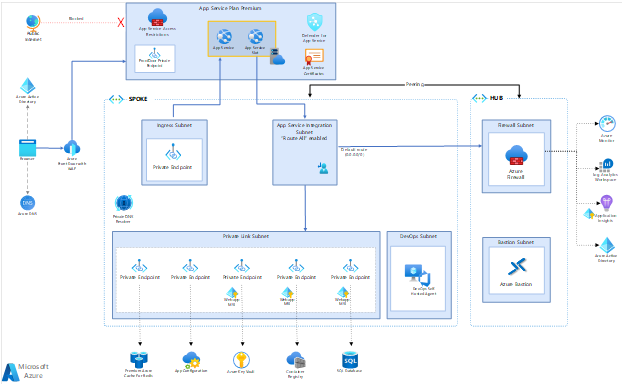
The secure baseline uses a security strategy called ‘defense in-depth’. This approach recommends creating multiple layers of defense at different points within your network or system, making it harder for attackers to access your sensitive information or critical systems. It is currently available as two separate implementations: Terraform and Bicep.
The reference implementation is built on the following key principles:
- Use isolated network layers for the different components.
- Use protected Azure Active Directory-based access via Managed Identity (where possible).
- Use private endpoints for Azure services.
- Use Network Security Groups to control inbound and outbound traffic at the subnet level.
- Enable Standard DDoS Protection for the SPOKE.
This reference implementation is built using the following features and services:
- Azure Front Door is used as a public front-end for all internet requests, acting as a global HTTP reverse proxy and cache in front of several Azure services. It enables protection from layer 3 and 4 DDoS attacks additionally providing you with a range of other features including WAF (web application firewall), caching, and custom rules to enhance the security and performance of your application.
- Virtual Network enables Azure resources to securely communicate with each other, the internet, and on-premises networks. This is done by creating boundaries, isolation, and segmentation of your workloads in the cloud, much like a physical network.
- Network Security Group is a set of security policies that Allow or Deny Inbound/Outbound traffic (Protocols/Ports).
- Azure App Service (Premium) to host the front-end API applications that are called by the app.
- Azure Cache for Redis provides a high-performance distributed cache for session state and general-purpose caching.
- Azure SQL DB provides a fully managed relational database service for back-end application services.
- Private Endpoints allow connections to Azure services from private VNETs and allow the public endpoints on these services to be disabled.
- Azure private DNS automatically configures and updates the DNS records required by private endpoint services.
- Azure Key Vault securely stores secrets and certificates to be accessed by Azure services.
- Azure App Config provides central management for application settings and feature flags.
- Azure Monitor and Application Insights to collect service logs and application performance metrics for observability
- The reference implementation also provides optional guidance for developers interested in using Azure Active Directory (Azure AD) or Azure AD B2C to authenticate the app’s users.
Get started today
When you're ready to begin, take a look at the guidance and reference implementation for Azure App Service Landing Zone Accelerators on GitHub: aka.ms/ModernApps/AppServiceLZA
- Scenario 1: Secure Baseline for Multitenant App Service
- Scenario 2: Line of business application using App Service Environment
Here are some other Landing Zone Accelerator resources you may be interested in. Watch this space, as new scenarios for Azure Container Apps and Azure Spring Apps are on the roadmap.
- Azure App Service: aka.ms/EnterpriseScale-AppService
- Azure API Management: aka.ms/EnterpriseScale-APIM
- Azure Integration Services: aka.ms/EnterpriseScale-Integration-Services
- Azure Kubernetes Service: aka.ms/AKSLZA/Documentation
- Azure Red Hat OpenShift: aka.ms/AROLZA/Documentation
Stay up-to-date on the latest in Azure app modernization
Bookmark the Apps on Azure blog to keep up with our expert coverage and product announcements and follow Microsoft Azure on Twitter for the latest news and updates.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.