- Home
- Microsoft 365
- Microsoft 365 admin center
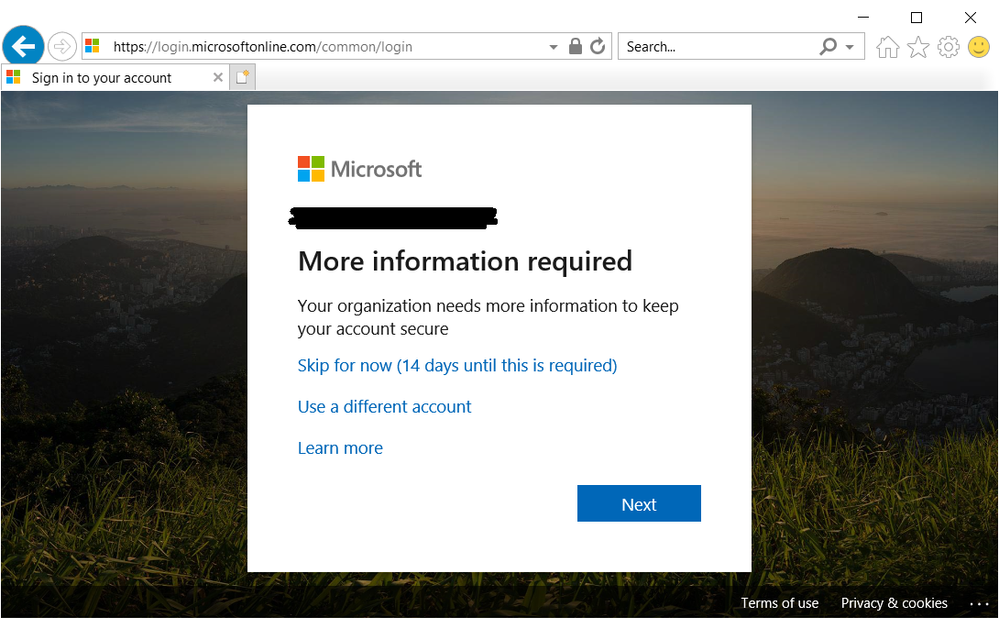
- All users receive "Your organization needs more information to keep your account secure" when logon
All users receive "Your organization needs more information to keep your account secure" when logon
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
Feb 06 2020
10:15 PM
- last edited on
Feb 07 2023
07:59 PM
by
TechCommunityAP
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 06 2020
10:15 PM
- last edited on
Feb 07 2023
07:59 PM
by
TechCommunityAP
All users receive "Your organization needs more information to keep your account secure" when logon o365 web portal.
Users can select "skip for now (XX days until is required)" but it will finally require all users to provide it.
I will have some user accounts to use on some applications or devices which must logon without multi-factor authentication and password should never changed.
I have checked that the multi-factor authentication page of the "MULTI-FACTOR AUTH STATUS" for all users are disabled.I also checked that the "Self service password reset enabled" is set to "none".
I don't have idea why all users still receive such message.
How can I disable this message and requirement to all user accounts?
Thank you.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 10 2020 09:22 AM
It's almost certainly a Conditional Access Policy.
Is the "End user protection (Preview)" baseline enabled?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 11 2020 05:02 AM
SolutionThank you for the hint.
Finally solved by:
Azure Active Directory > Properties
Manage security defaults
set Enable security defaults to No
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 30 2020 12:27 AM
CHECK THE SCREENSHOT BELOW MAKE SURE YOU SEARCH FOR THE PROPERTIES.
IF YOU DIDN'T CREATED AN AZURE ACCOUNT MAKE SURE YOU SIGN IN WITH YOUR ACCOUNT FACING THAT IS ISSUE.
THE SOLUTION IS TOTALLY FREE DO NOT SIGN UP FOR ANY AZURE PLANS PROVIDED
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 01 2020 05:15 AM
@microc1 Thanks for your support this helped me to resolve the problem of login for users in my organization. Kind Rgards
Mankay-Sierra Leone West Africa
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jun 01 2020 05:22 AM
Step 1 - Create a Security group in Office 365. To do this, go to https://portal.office.com and sign-in with your office 365 Global Administrator account > Select Admin Center.
Step 2 - On the left-Navigation pane, select Groups > Groups
Step 3 - Click on Add a Group. > Choose Security Group from the type drop-down > Give the group a name. Click Add.
Step 4 - Once the security group is created, navigate to the group and click Edit, next to members to add the user as the member of this security group.
Step 5 - Once you add the user as a member of the security group, then from the left navigation pane, expand Admin Centers and click on Azure Active Directory.
Step 6 - From Azure Active Directory Admin Center, choose Azure Active directory from the left menu.
Step 7 - From the Dashboard and option menu in the middle, click on Password Reset.
Step 8 - In the Password Reset properties page, choose Properties and select Selected to select a security group. You can also choose All if you want to enable SSPR for everyone.
Step 9 - Click on the group, then find the Select a Group desired security group from the list and click on select and then finally click on Save. Once saved, Self-Service Password Reset has been enabled for the users in the selected security group in your Office 365/Azure AD tenant, and you're done!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 05 2020 02:30 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 27 2020 09:16 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 27 2020 09:17 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 16 2021 04:03 AM - edited Sep 16 2021 04:27 AM
Just pointing out that MS put those defaults there for a reason. You are disabling many security features instead of finding a solution to your specific issue. Hackers are now able to password spray your Exchange Online using IMAP / POP3 etc, among other things. Here's how to do it without undermining the security of the tenant:
1. Add any external IPs of the locations they will send from to Trusted IPs under MFA settings. In most cases you would do this for all company owned office locations. https://account.activedirectory.windowsazure.com/UserManagement/MfaSettings.aspx
2. Set Password Reset Registration to No so that new users are not prompted to register.
https://portal.azure.com/#blade/Microsoft_AAD_IAM/PasswordResetMenuBlade/Registration
3. If you need to send SMTP email through Exchange Online (e.g. from a printer), create an account with exchange license to use for sending.
https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/Overview
4. Load Cloud Shell from top of the Azure Portal. Connect to Exchange:
Connect-EXOPSSession
5. Create an Authentication Policy:
New-AuthenticationPolicy -Name "Allow Basic Auth SMTP" -AllowBasicAuthSmtp
6. Assign the policy to the user:
Get-User user@domain.com | Set-User -AuthenticationPolicy "Allow Basic Auth SMTP"
7. Force policy to apply within 30 minutes:
Set-User user@domain.com -STSRefreshTokensValidFrom $([System.DateTime]::UtcNow)
Reference:
https://www.howdoiuseacomputer.com/index.php/2021/09/16/do-not-disable-security-defaults/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 09 2021 07:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 22 2022 07:50 AM
Solved it also to me.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 14 2022 02:25 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 09 2023 07:08 AM
@SimBur2365
None of your suggestions make any sense for my scenario. I can't login to Teams with MY account even though I'm the org admin. We don't use Exchange online, we have Exchange on prem. I already have 2FA enabled for my account. After approving in the MS authenticator app I get the message "Your organization needs more information to keep your account secure."
Well, what f***** information does it want?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 09 2023 08:37 AM
@d_logaan you just told me the problem... you are using an admin account for your day to day use. Create yourself a could-only account email address removed for privacy reasons. This doesn't need to be licensed. Give it a 32+ character password. Assign only the admin roles you need (not Global Admin). Create a browser profile in edge or chrome so you can easily switch to that account when required for admin tasks. Now create an emergency admin account (two even better)... with 64+ character passwords and save them in a password vault or similarly secure location. Only use those when you must have Global Admin rights to perform a task (this will not be very often).
Now remove any admin roles from your day to day account so that if you get compromised they can't highjack your entire tenant.
If you don't want to do that then go to https://myaccount.microsoft.com and register another couple of methods like SMS and Email.
Cheers =)
PS - IMO it's becoming a no-brainer to go for Business Premium for up to 300 users, or an AD Premium add-on for more than 300. Having the granular control over these settings is worth it, and you get full Defender Antivirus, phishing and DLP protection etc. Appreciate that may not fit your scenario for some reason.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Apr 30 2023 02:11 PM
The issue for me was having enabled self-service password reset. Once I reverted that setting I was able to function with that account again as normal @microc1
I believe the problem was that there were not sufficient email/phone numbers listed for the account to enable self-service.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 27 2023 04:05 PM
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
May 28 2023 05:04 PM
@nick242 for me the only way I found out was to disable self service password resets. Have bot identified what it is within that setting causing me the issue (loop).
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 04 2023 05:22 AM
I have read the advices but for most of them, it is required to log in in order to make some changes. I haven no clue what to do
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 07 2023 09:25 AM
Our solution was to set "self service password resets" only for human accounts, which we handled by creating a specific group.
Thanks Thomo
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Feb 11 2020 05:02 AM
SolutionThank you for the hint.
Finally solved by:
Azure Active Directory > Properties
Manage security defaults
set Enable security defaults to No