- Home
- Windows
- Windows IT Pro Blog
- Getting started with FSLogix profile containers on Azure Files in Windows Virtual Desktop
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Back in March, we released the public preview of Windows Virtual Desktop, a cloud-based desktop and app virtualization service that supports multi-session Windows 10 experiences, Remote Desktop Services (RDS), and Office 365 ProPlus. Today I wanted to share some guidance on how to set up FSLogix profile containers on Azure Files with Azure Active Directory (Azure AD) Domain Services authentication, a scenario also available in public preview as of the date of this post.
For the purposes of this step-by-step guide, I’m going to assume that you already have a set of virtual machines (VMs) that are part of a Windows Virtual Desktop environment. If not, you can find information on how to get started with Windows Virtual Desktop on the Tech Community or through our official technical documentation on Docs.
This post will walk you through the process of:
- Configuring Azure AD Domain Services.
- Creating an Azure Files storage account and enabling Azure AD Domain Services authentication
- Configuring FSLogix.
Configuring Azure AD Domain Services
First, you’ll need to log in to the Microsoft Azure Portal with an account that has contributor or administrator permissions.
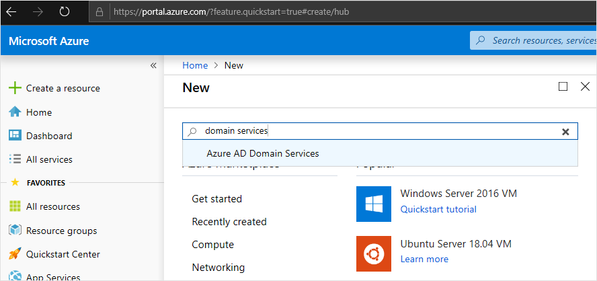
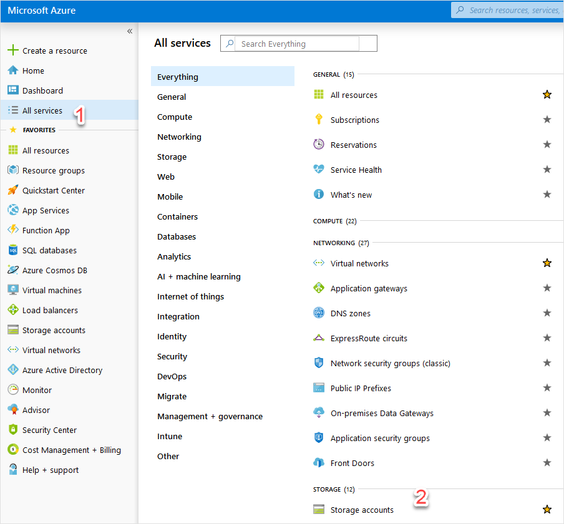
From the sidebar, select All services, type “domain services” in the search box, select Azure AD Domain Services, and hit Enter.
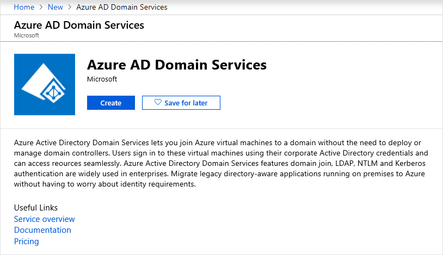
In the Azure AD Domain Services window, select Create.
This will start the wizard for configuring an Azure AD Domain Services deployment.
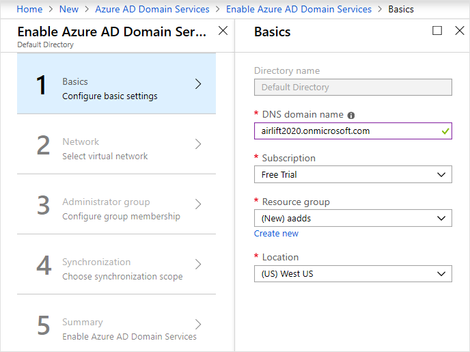
For step 1, Basics:
- Enter the DNS domain name.
- Select an active Azure subscription (if multiple are available).
- Select an empty resource group or create a new one by selecting Create new.
- Select a location.
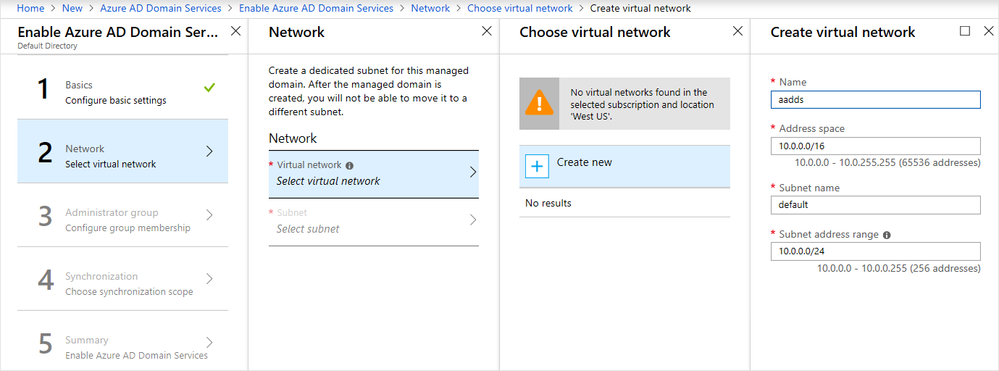
For step 2, Network, configure a virtual network or select an existing one. Our recommendation is to create a new one by selecting Create new and entering the following information:
- Name
- Address space
- Subnet name
- Subnet address range
For step 3, Administrator group, select the Azure AD users that are going to be managing the Azure AD Domain Services configuration.
For most deployments, there is no need to change any of the information in step 4, Synchronization. The default values should suffice.
In step 5, Summary, you will see a summary of your configuration, similar to that shown below.
Click OK to continue. This will start the deployment in Azure. If it is not automatically shown, you can click on the Notifications icon in the global controls bar to view deployment progress, as shown here:
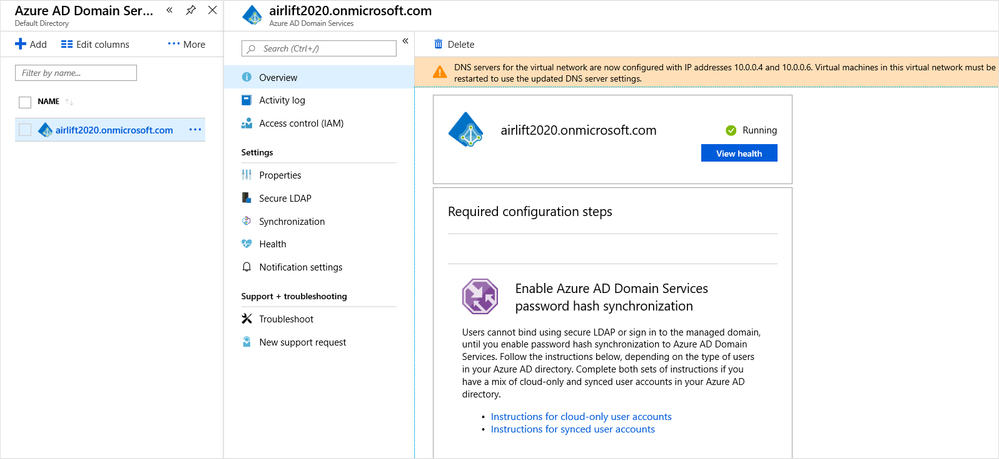
Once the deployment has completed, navigate to Azure AD Domain Services and confirm that Azure AD Domain Services is running.
Adding additional Azure AD Domain Services administrators
To add additional administrators, we are first going to create a new user and then grant permissions to that user. To do this:
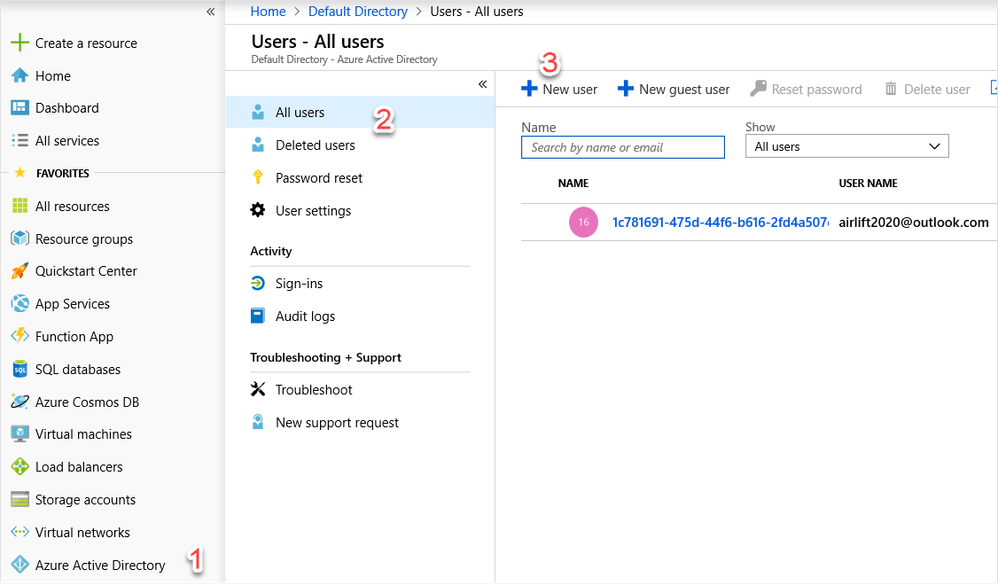
- Select Azure Active Directory from the sidebar, select All users, and select New user.
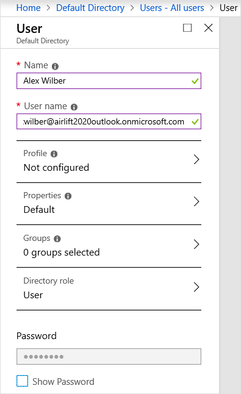
- Enter user details.
- Back in the Azure Active Directory left pane, select Groups.
- Select the AAD DC Administrators.
- In the left pane, select Members, then select Add members in the main pane. This will show a list of all users available in Azure AD. Select the user that was just created.
Create an Azure Files storage account and enable Azure AD Domain Services authentication
Now it’s time to enable Azure AD Domain Services authentication over Server Message Block (SMB). For more details on this process, see the Azure Storage Documentation.
First, navigate to the Microsoft Azure Portal, select All services from the sidebar, and select Storage accounts.
Next, click Add to start the Create storage account wizard. Enter the following details:
- Select Subscription (if applicable).
- Select an existing Resource group or select Create new to create a new one.
- Enter the Storage account name.
- Select the (We recommend using the same location as the session host VMs.)
- Select the Performance
- Select a StorageV2 (general purpose V2) Account kind.
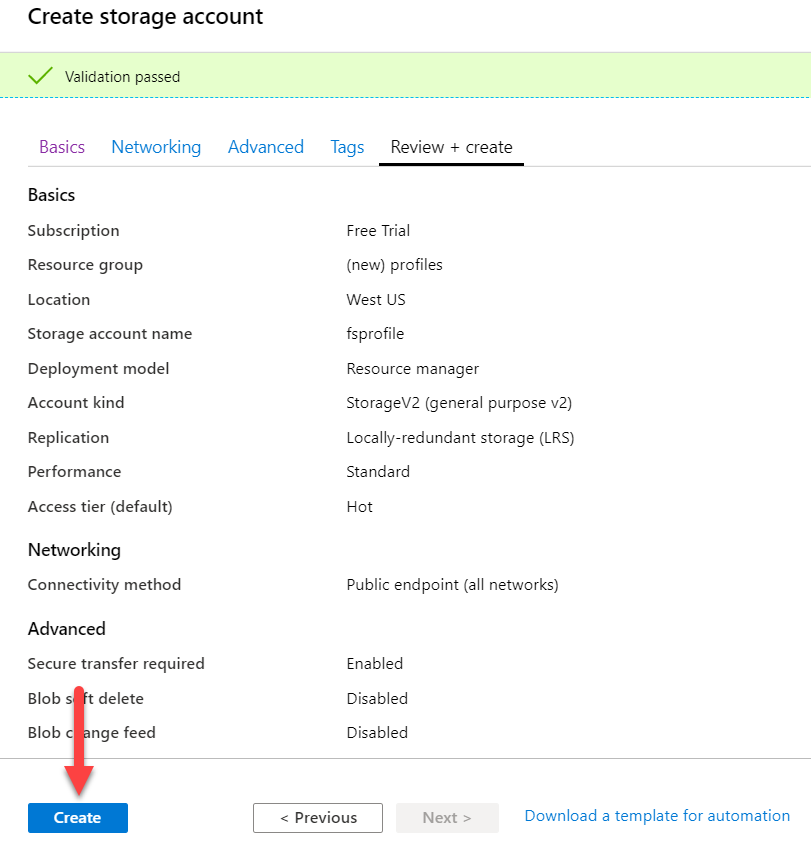
Select Review + create.
This will trigger validation of the input, as shown below.
Once the account has passed validation, select Create. This will start the deployment.
Once the deployment has completed, proceed to the next step by selecting Go to resource.
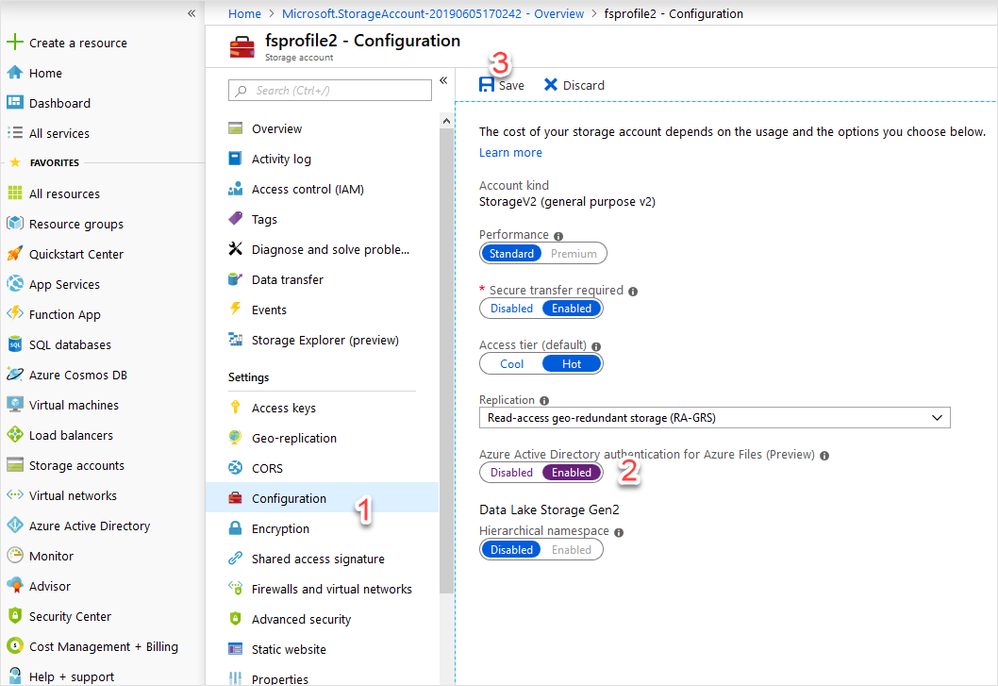
Select Configuration from the left pane, then enable Azure Active Directory authentication for Azure Files (Preview) in the main pane. Confirm this change by selecting Save.
Once saved, select Overview in the left pane, then Files in the main pane.
Select File share and enter the Name and Quota.
Copy and paste the following information into Notepad or other plain text application:
{
"Name": "<Custom-Role-Name>",
"Id": null,
"IsCustom": true,
"Description": "Allows for read, write and delete access to Azure File Share over SMB",
"Actions": [
"*"
],
"NotActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action"
],
"DataActions": [
"*"
],
"AssignableScopes": [
"/subscriptions/<Subscription-ID>"
]
}
Replace <Custom-Role-Name> with AADDCpreview and replace <Subscription-ID> with the subscription I in which the storage account is located.
Note: To get the subscription ID, navigate to the Microsoft Azure Portal, select All services from the sidebar, and select Subscriptions from the Everything menu.
Save the file as CustomRole.JSON.
Open Windows PowerShell as an administrator.
In PowerShell,
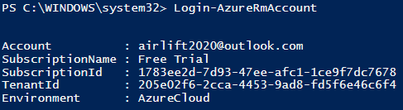
- Execute the following command:
Login-AzureRmAccount
- When prompted, enter Global administrator or Contributor.
- If needed, select the desired subscription, then execute the following command:
New-AzureRmRoleDefinition -InputFile "C:\temp\CustomRole.json"
- When prompted to -InputFile, enter the file path for the JSON file.
- Assign the new role to all users that will be getting user profiles.
#Get the name of the custom role:
$FileShareContributorRole = Get-AzRoleDefinition "<role-name>"
#Constrain the scope to the target file share:
$scope = "/subscriptions/<subscription-id>/resourceGroups/<resource-group>/providers/Microsoft.Storage/storageAccounts/<storage-account>/fileServices/default/fileshare/<share-name>"
#Assign the custom role to the target identity with the specified scope.
New-AzRoleAssignment -SignInName <user-principal-name> -RoleDefinitionName $FileShareContributorRole.Name -Scope $scope
Make the following modifications to commands above:
- For <role-name>, specify the same name as one defined in JSON (AADDCpreview).
- Replace <subscription-id> with the desired subscription id.
- Replace <resource-group> with the name of the resource group where the storage account is (profiles).
- Replace <storage-account> with the name of the resource storage (fsprofile).
- Replace <share-name> with the name of the share created earlier (share).
- Replace <user-principal-name> with user principal names of those users that will utilize FSLogix profiles on Azure Files.
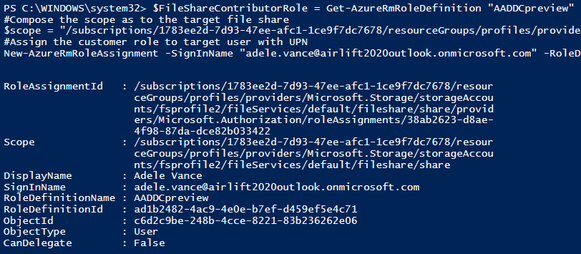
Here's an example:
$FileShareContributorRole = Get-AzureRmRoleDefinition "AADDCpreview"
#Compose the scope as to the target file share:
$scope = "/subscriptions/1783ee2d-7d93-47ee-afc1-1ce9f7dc7678/resourceGroups/profiles/providers/Microsoft.Storage/storageAccounts/fsprofile2/fileServices/default/fileshare/share"
#Assign the customer role to target user with UPN
New-AzureRmRoleAssignment -SignInName "adele.vance@airlift2020outlook.onmicrosoft.com" -RoleDefinitionName $FileShareContributorRole.Name -Scope $scope)
- Finally, navigate to the Microsoft Azure Portal, select Virtual machines from the sidebar, select the desired VM, select Overview in the left pane, then Connect in the main pane to sign in as an administrator and start a Remote Desktop (RDP) session.
Obtain storage account access key
From the Microsoft Azure Portal sidebar, select Storage accounts. From the list of storage accounts, select the account for which you enabled Azure AD Domain Services and created the custom roles in steps above.
Under Settings, select Access keys and copy the key from key1.
Note: If the key contains the “/” symbol, hit the Refresh icon to generate a new key.
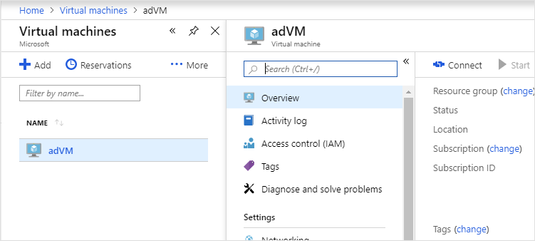
Navigate to the Virtual Machines tab and locate any VM that is going to be part of your hostpool.
Click on the name of the VM under Virtual Machines (adVM) and select Connect.
This will download an RDP file that allows you to connect to the VM via the credentials specified during VM creation.
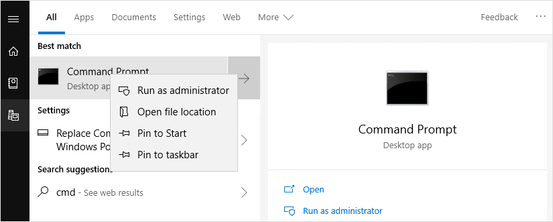
Once remotely connect to the VM, run Command Prompt as an administrator.
Execute the following command, making the modifications noted below:
net use <desired-drive-letter>: \\<storage-account-name>.file.core.windows.net\<share-name> <storage-account-key> /user:Azure\<storage-account-name>
Modifications to this command should be as follows:
- Replace <desired-drive-letter> with a drive letter of choice (e.g. y:).
- Replace all instances of <storage-account-name> with the name of the storage account specified earlier.
- Replace <share-name> with the name of the share created earlier.
- Replace <storage-account-key> with the storage account key from Azure.
Here’s an example of what the command will look like:
net use y: \\fsprofile.file.core.windows.net\share HDZQRoFP2BBmoYQ=(truncated)= /user:Azure\fsprofile)
Execute the following command to grant full access to the Azure Files share:
icacls <mounted-drive-letter>: /grant <user-email>:(f)
Modifications to this command should be as follows
- Replace <mounted-drive-letter> with a drive letter of choice.
- Replace <user-email> with the UPN of the user who will be accessing the session host VMs and needs a profile.
Here’s an example of what the command will look like:
icacls y: /grant alexwilber@airlift2020outlook.onmicrosoft.com:(f)
Configure FSLogix on session host VMs
Now it’s time to configure the FSLogix profile container. For more details on this process, see Set up a user profile share for a host pool.
While still remotely logged in to the session host VM, download and install the FSLogix agent (.zip file, 166 MB. Unzip the downloaded file and navigate to x64\Releases and execute FSLogixAppsSetup.exe.
Note: if there are multiple VMs in the host pool the below configuration must be done for each VM.
Once the installer launches, select I agree to the license terms and conditions. If applicable, provide a new key. Select Install.
Navigate to C:\Program Files\FSLogix\Apps to confirm that the FSLogix agent was properly installed.
Run Registry Editor (RegEdit) as an administrator.
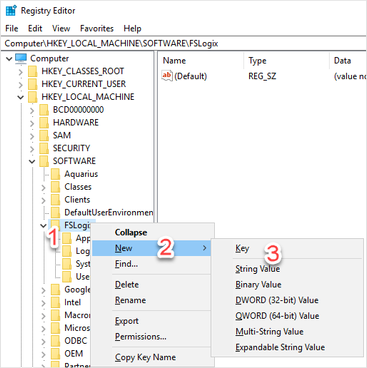
Navigate to Computer\HKEY_LOCAL_MACHINE\software\FSLogix, right click on FSLogix, select New, then Key. Create a new key named Profiles.
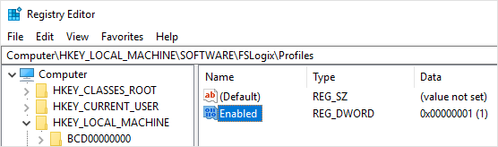
Right click on Profiles, select New, and select DWORD (32-bit) Value. Name the value Enabled and set the Value data to 1.
Right click on Profiles, select New, and select Multi-String Value. Name the value VHDLocations and set enter the URI for the Azure Files share (\\fsprofile.file.core.windows.net\share) as the Value data.
Assign users to session host
Run Windows PowerShell as an administrator and log in to Windows Virtual Desktop through PowerShell by executing the following command:
Import-Module Microsoft.RdInfra.RdPowershell (Optional) Install-Module Microsoft.RdInfra.RdPowershell $brokerurl = "https://rdbroker.wvd.microsoft.com" Add-RdsAccount -DeploymentUrl $brokerurl
When prompted for credentials, enter the same user that was granted the Tenant Creator role or RDS Owner/RDS Contributor role on the Windows Virtual Desktop tenant.
Execute the following commands to assign the user to the remote desktop group:
$tenant = "<your-wvd-tenant>" $pool1 = "<wvd-pool>" $appgroup = "Desktop Application Group" $user1 = "<user-principal>" Add-RdsAppGroupUser $tenant $pool1 $appgroup $user1
Here’s an example of what the command will look like:
$pool1 = "airlift2020" $tenant = "airlift2020" $appgroup = "Desktop Application Group" $user1 = "debra.berger@airlift2020outlook.onmicrosoft.com" Add-RdsAppGroupUser $tenant $pool1 $appgroup $user1)
Verify the profile creation
You are now ready to verify that the profile was created.
To do this:
- Open a browser of choice.
- Navigate to https://aka.ms/wvdweb.
- Sign in with the user account that was assigned to the remote desktop group.
- Once the user session has been established, navigate back to the Microsoft Azure Portal and log in with an administrative account.
- From the sidebar, select Storage accounts.
- Select the storage account that was configured as the file share for your session host pool and enabled with Azure AD Domain Services.
- Select the Files icon, then expand your share.
Inside there will be a Directory named <user SID>-<username>
Summary
This short video demonstrates the end user experience once all configuration steps in this document have been completed. For more detail on FSLogix profile containers and Azure Files from a conceptual perspective—as well as information on why Azure Files is a preferred method for storing user profiles, performance insights, and best practices—see our Windows Virtual Desktop documentation.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.