- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Tamper protection in Microsoft Defender ATP
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Update (October 14, 2019): Tamper protection is now generally available for Microsoft Defender ATP customers and enabled by default for home users
We are committed to making our solutions resistant to attacks and continuously working towards raising the bar in security. In this blog we’re covering the tamper protection feature in our antimalware solution. This feature builds on our previously announced Windows Defender Antivirus sandboxing capability and expands existing tamper protection strategies across Microsoft Defender Advanced Threat Protection.
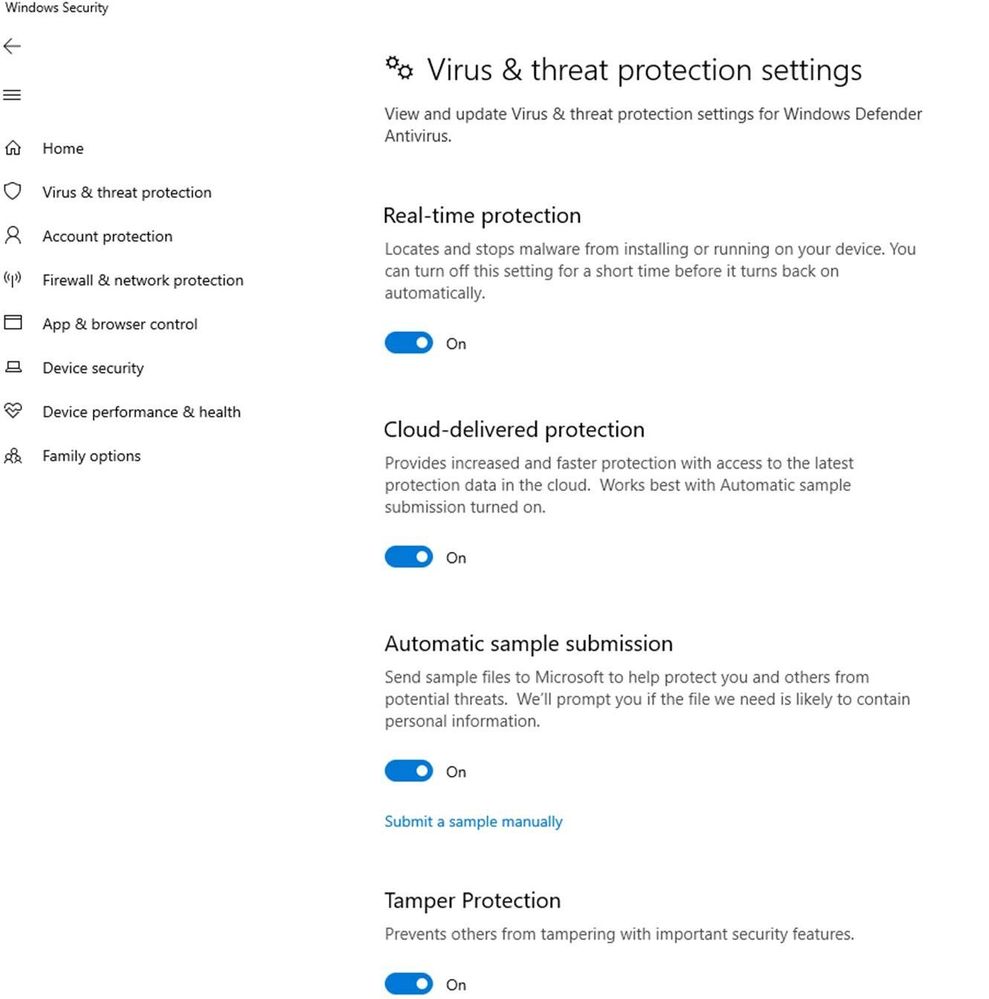
Tamper protection is a new setting available in the Windows Security app which provides additional protections against changes to key security features, including limiting changes that are not made directly through the app.
If you are a home user, you can toggle the setting from the Virus & threat protection settings area in the app. For enterprise environments, the setting can be managed centrally through the Intune management portal.
We’re continuing to work on the feature, but the current version of the setting is available to Windows Insiders today. The full functionality of the feature (including support for enterprise-level management) will be released along with the upcoming release of Windows 10.
Enabling this feature prevents others (including malicious apps) from changing important protection features such as:
- Real-time protection, which is the core antimalware scanning feature of Microsoft Defender ATP next gen protection and should rarely, if ever, be disabled
- Cloud-delivered protection, which uses our cloud-based detection and prevention services to block never-before seen malware within seconds
- IOAV, which handles the detection of suspicious files from the Internet
- Behavior monitoring, which works with real-time protection to analyze and determine if active processes are behaving in a suspicious or malicious way and blocks them
The feature also prevents the deletion of security intelligence updates and the disabling of the entire antimalware solution. Note: There's no change in the way third-party antivirus solutions are registered with the Windows Security app.
For Windows home users, the feature will be On by default when Windows is installed. If you are upgrading and Cloud-delivered protection is enabled, then the tampering protection feature will also be turned On.
For enterprise E5 customers (such as those with a Microsoft Defender ATP license), this feature will be opt-in and can only be managed from the Intune management console. Local device admin users will not be able to change the setting. This ensures that even malicious apps – or malicious actors – can’t locally override the setting. Note that enterprise management is currently in preview.
We’re continuing to work on this feature, and you can test it out now on any recent Windows Insider build released during March 2019 or later. If you’d like to test this feature, please send us feedback via the Feedback Hub, or email us at wdcustomer@microsoft.com.
We’d love to have you on the journey so we can use your feedback and insights to deliver strong protection across platforms.
Not yet reaping the benefits of Microsoft Defender ATP’s industry-leading optics and detection capabilities? Sign up for free trial today.
Iaan D’Souza-Wiltshire (@iaanMSFT) & Shweta Jha (@shwetajha_MS)
Microsoft Defender ATP
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.