- Home
- Windows
- Windows Blog Archive
- Achieving Assurance with Windows 10 Security
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
First Published on TechNet on: Jun 29, 2016
Guest author: Chris Hallum
Microsoft has a long history pursuing security certifications for our products, and in particular for Windows. Every major version of Windows since Windows 2000 has been validated against FIPS 140 and against the Common Criteria (CC). The relevance of these certifications is most applicable to IT organizations that have procurement policies that require or recommend evaluated products, or have formal accreditation processes. Organizations that may not have formal mandates for certified products still benefit from the fact that these products were evaluated to meet the needs of customers that depend on certification. Additionally, whenever possible, Microsoft also certifies our consumer editions of Windows, so that non-commercial customers can benefit from the same kind of security evaluations that governments expect from independent third party evaluators.
2016 has been a busy year for securing new Windows security certifications for Windows 10, which include:
There are also CC evaluations underway for Windows 10 (November 2015 Update) against the IPsec VPN Client protection profile, and FIPS 140 validations of Windows 10 (November 2015 Update) with Surface Pro 4 and Surface Book, as well as Windows 10 Mobile.
As the Windows 10 Anniversary Update approaches, we will reload the evaluation machinery with the latest operating system and start a new wave of certifications.
We also are operating at a faster certification cadence in 2015 and 2016 than in the past. This table shows the increased tempo:
| Year | CC certifications completed |
| 2016 (year to date) | 4 |
| 2015 | 5 * |
| 2014 | 1 |
| 2013 | 1 |
| 2012 | 0 |
| 2011 | 1 |
| 2010 | 0 |
| 2009 | 1 |
| 2008 | 1 |
* Essentially there were three evaluations in 2015 because one evaluation project generated two certificates that were issued in early January 2015 for work completed in 2014.
This reflects the faster release speed of Windows: as well as structural changes in the CC environment. First, Microsoft now releases Windows more frequently:
| Operating System | Release date |
| Windows Vista | November 2006 |
| Windows 7 | July 2009 |
| Windows 8 | August 2012 |
| Windows 8.1 | October 2013 |
| Windows 10 | July 2015 |
| Windows 10 November 2015 Update | November 2015 |
| Windows 10 Anniversary Update | Summer 2016 |
Another important reason for the faster turn-around time in certifications is the July 2014 revision of the Common Criteria Recognition Arrangement (CCRA), which enables product vendors to evaluate their products in any of the CCRA certificate-authorizing countries, and the results are accepted as being valid CC certificates in the twenty-five CCRA member nations. This wide scope allows Microsoft and other IT suppliers to efficiently certify their products once and apply the results to a broad market.
The revamped CCRA emphasizes product certification with "Protection Profiles", using an evaluation approach based on repeatable processes to verify collections of security functional requirements for a specific type of technology, such as routers, firewalls, and encryption at rest products. These requirements are created in working groups, with industry, CC certification schemes, and product users all agreeing on acceptable functionality and verification procedures, particularly for testing. Evaluating products using protection profiles results in more focused (i.e. faster) examinations because the evaluation criteria are more precisely defined.
The net effect of the faster release cadence for Windows and the shift to evaluations based on protection profiles and assurance activities is clearly visible over the past ten years of Windows certifications:
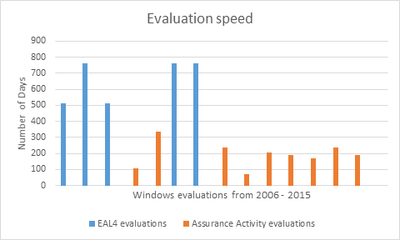
A faster evaluation does not necessarily have to provide less insight into the product, or less assurance. As an example, Windows 7 was evaluated against the "US Government Protection Profile for General-Purpose Operating Systems in a Networked Environment", which did not include requirements for protocols like TLS, nor evaluator instructions to confirm correctness. The Windows 7 security target, which is the formal description of the product undergoing evaluation, added its own requirement for TLS, but the lab was on its own to devise verification procedures. In contrast, the Mobile Device Fundamentals protection profile used for the Windows 10 evaluations has eight mandatory requirements for TLS, covering acceptable protocol versions and ciphersuites, certificate validation, use during EAP-TLS, and twenty-two corresponding tests. The result was a more thorough review of the Windows TLS implementation. Combining the conformance-based methodology with a structured approach in searching for general kinds of weaknesses may yield further assurance about the product's resistance to attack.
Microsoft was one of the leaders in calling for changes in CC to speed up certifications and increase the relevance of evaluation in the 2015 presentation Lessons Learned in the Adoption of the Common Criteria, which helped set the agenda for reforming CC, and provided early results that the new approach could be applied successfully in Evaluating Windows in 2013.
The result is that, with the emergence of Windows as a Service (WaaS) and the updated CC methodology, Microsoft can provide more in-depth assurance and more timely product independent third party certifications to our customers.
More information on Windows Platform Common Criteria status and approach can be found on TechNet: https://msdn.microsoft.com/en-us/library/dd229319.aspx. Information on Windows Platform FIPS 140 status and approach can be found at: https://technet.microsoft.com/en-us/library/security/cc750357.aspx.