- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- What’s new in the WDATP Portal? June 6th 2017
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Alert Suppression rules evolution [Internal Preview]
We've created a new flow and added functionalities to the alert suppression feature.
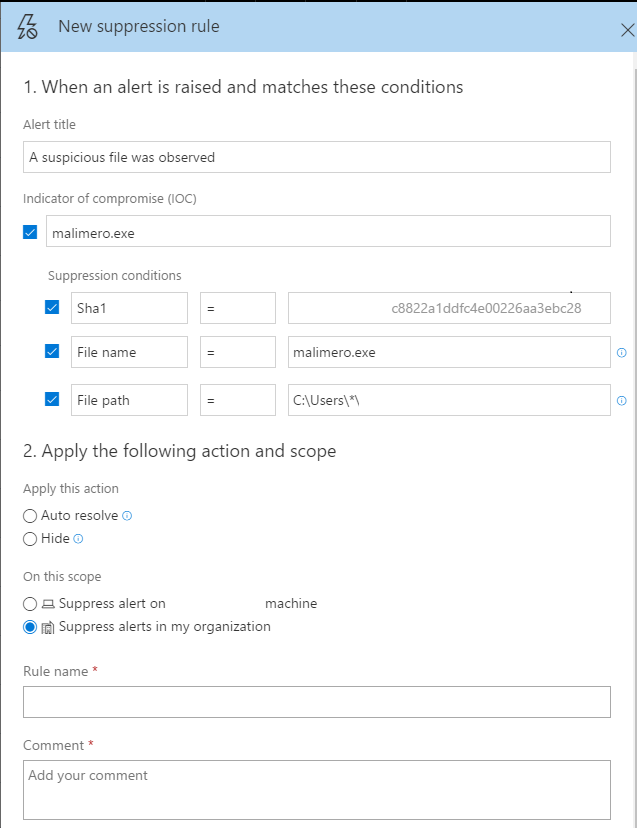
From an alert, you can create a new suppression rule. No longer will you choose all or nothing. You can now suppress alerts based on specific alert attributes:
• File hash
• File name - wild card supported
• File path - wild card supported
• IP
• URL - wild card supported
The feature supports two actions that will be enforced on the alerts:
• Auto resolve - matching alerts will be resolved automatically and presented in the resolved section of the alerts queue
• Hide - matching alerts will not be presented in the portal
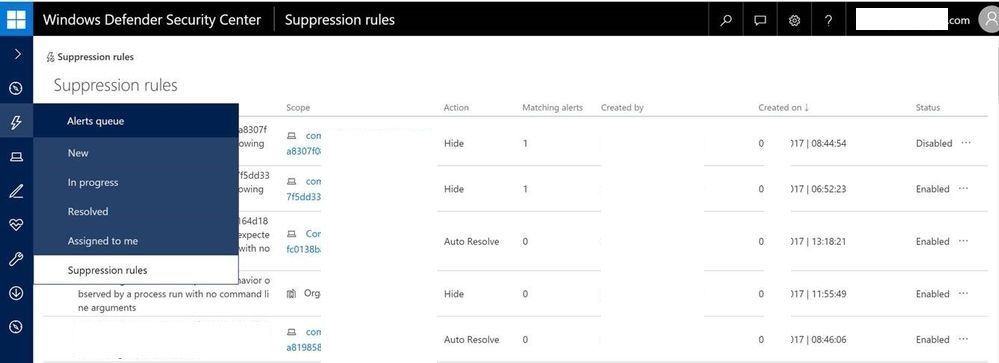
New suppression rules view
We've made the suppression rules tab more accessible and redesigned the suppression rules page so that you can see more details about the suppression rules and their scope.
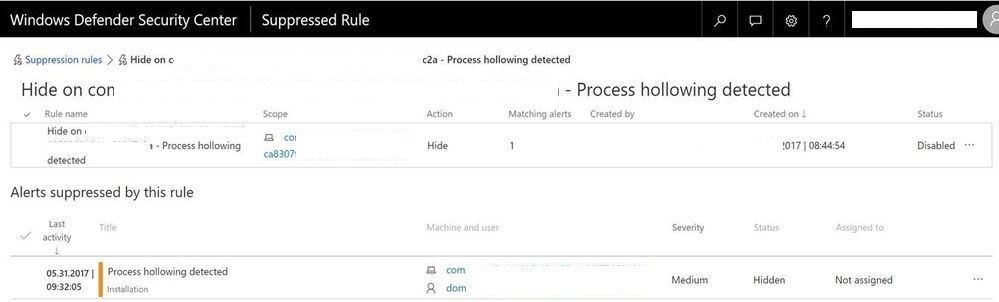
New suppression rule page
We've created a new suppression rule page where you'll be able to see additional details about the rule, such as the associated alerts that were hidden or auto resolved by this rule. The same page will also allow you to restore the alerts, disable or enable the rule.
SIEM enhancements
LogOnUsers exposed to SIEM
We've exposed LogOnUsers data at time of the event to enrich the information sent to SIEM.
A new field LogOnUsers is now added to the alerts payload populated with the logon users and their domains at time of the alert.
Suppressed alerts will not be sent to SIEM tools [Internal Preview]
We've fixed the issue of suppressed alerts being sent to SIEM tools. Suppressed alerts will no longer be sent to SIEM tools.
New ArcSight mapping file
We've updated the mapping file between our schema and ArcSight fields to help you get the most out of the data exposed in the alerts API.
New mapping file is available for download from the portal:
Preferences setup -> SIEM integration -> Choose HP ArcSight -> Save details to file.
In the downloaded .zip file, you will find the new mapping in the WDATP-Connector.jsonparser.properties file.
Alert process tree enhancements [Internal Preview]
Decode PowerShell encoded commands
You can now see the decoded PowerShell encoded commands in the side-pane of relevant processes.
Leaner & meaner process tree
The alert process tree now goes up the attack chain showing processes and actions that were previously not visible, while showing fewer irrelevant processes.
To clean-up the process tree, we no longer show children of known root processes (such as svchost.exe) if they are not associated with the alert.
This enables us to show instead more events that are interesting. One of the changes that were done is to extend the time period displayed in the alert process tree from 20 minutes to up to 1.5 hours. Another change includes showing process trees that were previously not shown, if they are related to the detected process trees. In the example below, we now also show the download of the malicious doc, although it's in a different tree than the one initially detected. Finally, we now display click-on-links from outlook, word and other programs - when they are done right before a browser download that is related to the alert.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.