- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- What’s new in the WDATP Portal? July 24th, 2017
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Alert & machine reporting - Power BI content pack [Internal Preview]
WDATP Alert & machine statistics data is now consumable via a Power BI content pack and displays:
- "Data Dashboard" - Summary of the past month, showing:
- Machine statistics: Breakdown by machine health status, and by OS platform
- Alerts: Breakdown by: severity, status, detection source
- Resolved alerts: Breakdown by severity, by detection source, by precision, and trend of resolved alerts (by day)
Clicking on any of the tiles will take you to the respective tab that drills down further into the data:
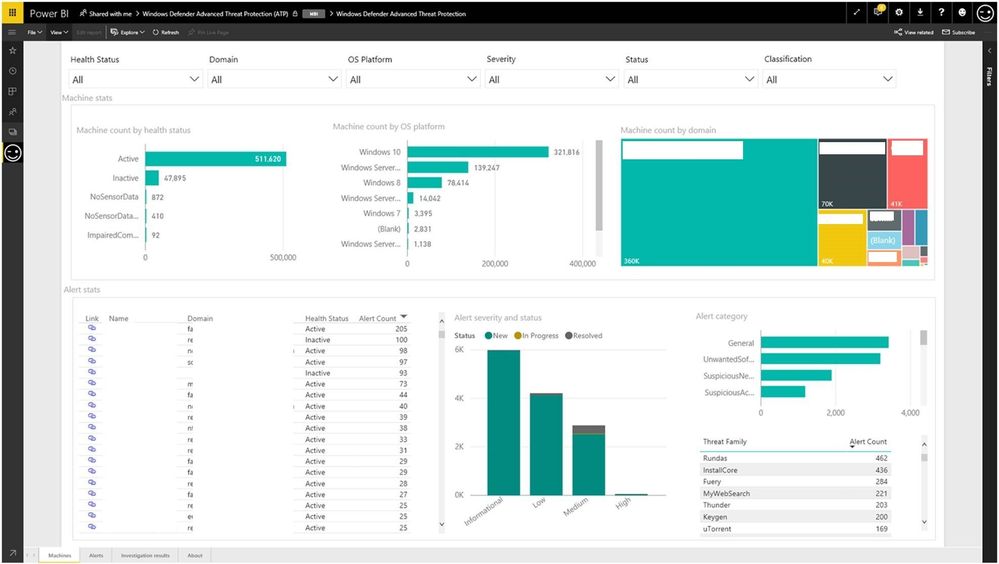
- "Machines tab" - Summary of the past month, showing:
- Machine statistics: Breakdown by machine health status, OS platform, and domain
- Alert statistics: List of machines, ranked by # of reported alerts, alert breakdown by severity and status, by category, and by threat family
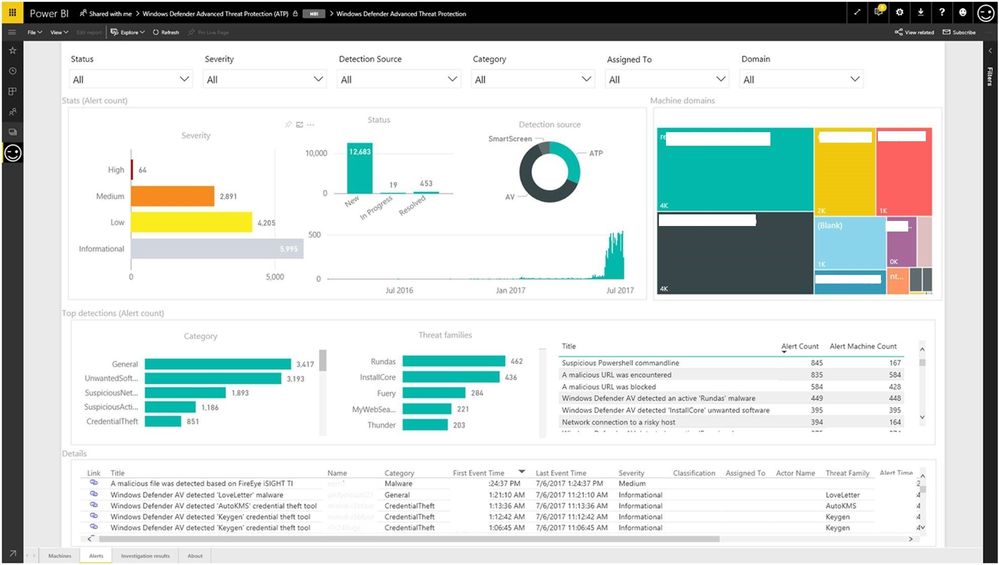
- "Alerts tab" - Summary of the past month, showing:
- Alert statistics: Breakdown by severity, status, detection source, (machine) domain, category, threat family
- Alert lists: ranked list of alerts, total number of alerts, and total number of machines reporting that alert, and a list of the reported alerts
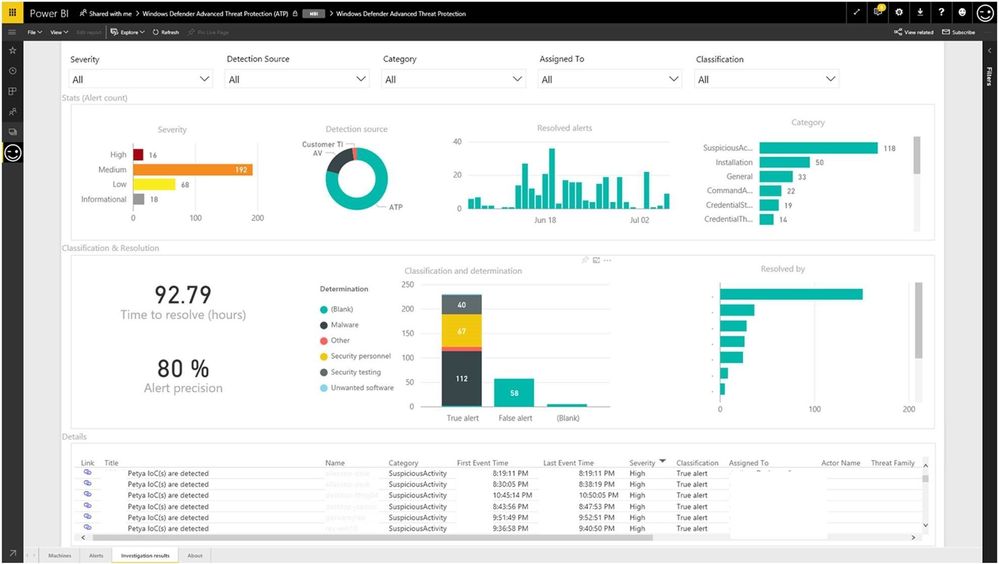
- "Investigation results tab" - Summary of the past month, showing:
- Resolved Alerts statistics: Breakdown by severity, detection source, daily trend (# of alerts resolved), and category
- Classification and resolution: Average time to resolve, alert precision, breakdown by classification & resolution, and # resolutions per analyst
- List of alerts and details
Note: Access to this feature is currently limited within Internal Preview and not [yet] fully exposed via the WDATP portal to all approved users on the MSIT tenant
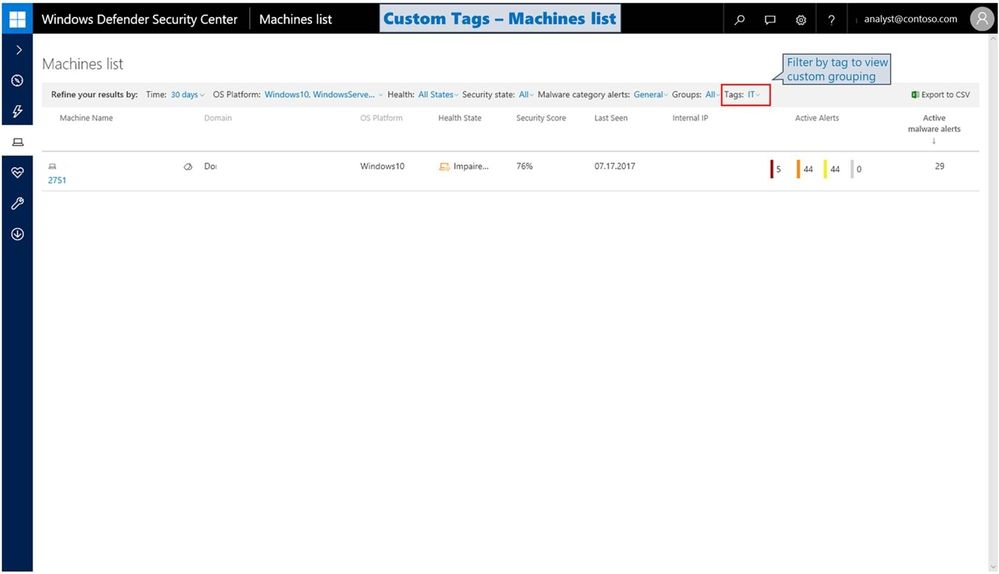
Tagging in portal [Internal Preview]
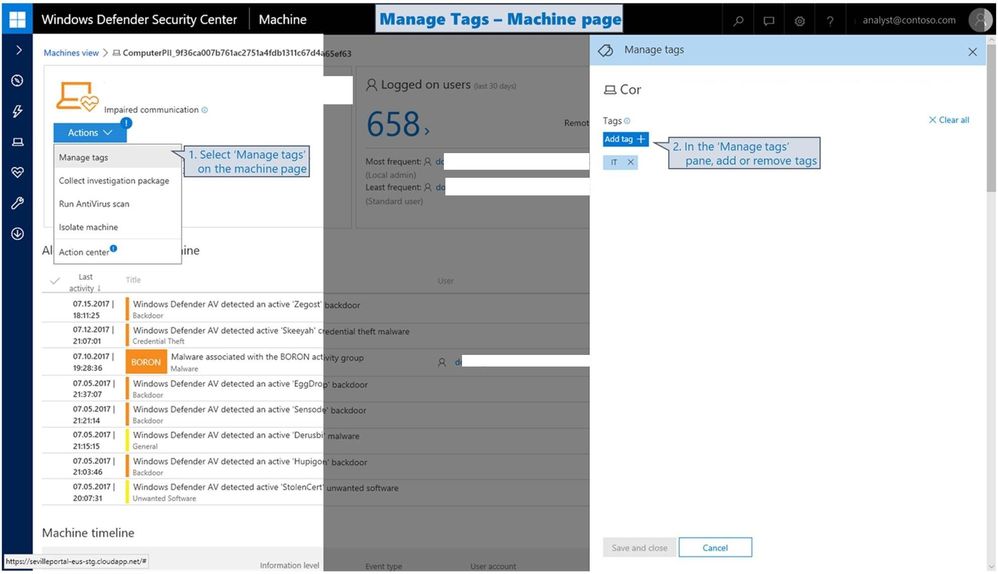
We now support adding custom tags to machines (e.g. SAWs, etc.), to support easier filtering and focusing on customer-defined grouping.
Filter the Machines list by custom tag/s
Managing and applying custom tags to machines
Custom tags appear on the Machine page
"Restrict code execution" response action [Internal Preview]
In this update, we're further enhancing response capabilities and adding the ability to disrupt & contain attacker activity by applying a lock down policy on potentially compromised machines to prevent execution of unknown, malicious programs.
The new "Restrict code execution:" response action will be available in the portal for Windows 10 machines running the Creators Fall (RS3) update.
To use this new capability:
- Open the action menu and select "Restrict code execution"
- Type a comment (optional) and select yes to take action on the machine
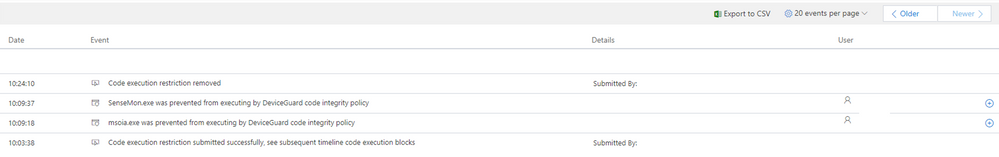
- The action center shows the submission information similarly to other response action
- When execution restriction action is applied on the machine, a new event is reflected in the machine timeline
Note: undoing execution restriction is also possible from the console by opening the action menu and selecting "Undo restrict code execution" on a machine the action was previously applied on.
We'd love to hear your feedback on the new features - that's it for this time!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.