- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Go hunt, join us on GitHub
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
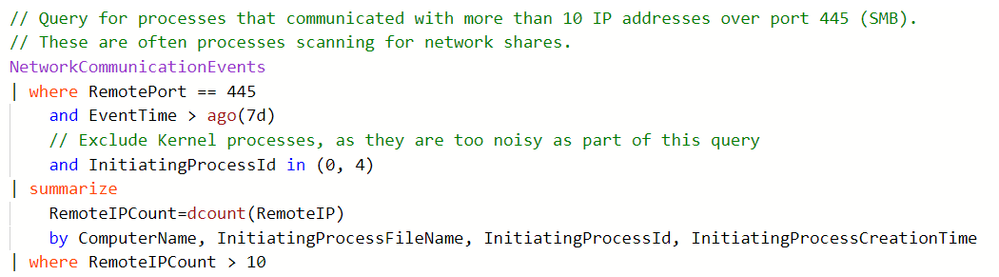
We’d like to invite you to explore our GitHub repository of sample queries for Advanced hunting in Windows Defender Advanced Threat Protection.
It has been exciting to see thousands of customers using our new Advanced hunting capabilities. We would like to take it a step forward by enabling our users to share their knowledge with the community and help others identify breaches and other unwanted activity.
Got your own interesting query? Everyone is welcome to contribute queries – so come and join the fun!
Visit the repository regularly to get hunting ideas, learn more about the query language and available data, and get familiar with specific attacker campaigns and tactics, techniques, and procedures (TTPs).
The queries in the repository can vary in complexity and purpose. To give a few examples, these queries could:
- Hunt for known TTPs (Persistence through accessibility features)
- Join multiple noisy signals together to find gold (Doc attachment > Click on link > Browser download)
- Focus on a single tool usage (Enumeration of users or groups using net.exe)
- Slice and dice the signals from Windows Defender suite (Exploit Guard audits and blocks)
- Track concrete CVEs (CVE-2018-1000006) or campaigns (Dofoil)
And so much more…
See you at the hunting grounds!
Thanks,
Windows Defender ATP team
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.