Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Microsoft Graph Security API
- Using Graph Explorer with the Graph Security API
Using Graph Explorer with the Graph Security API
Discussion Options
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 28 2018 03:35 PM
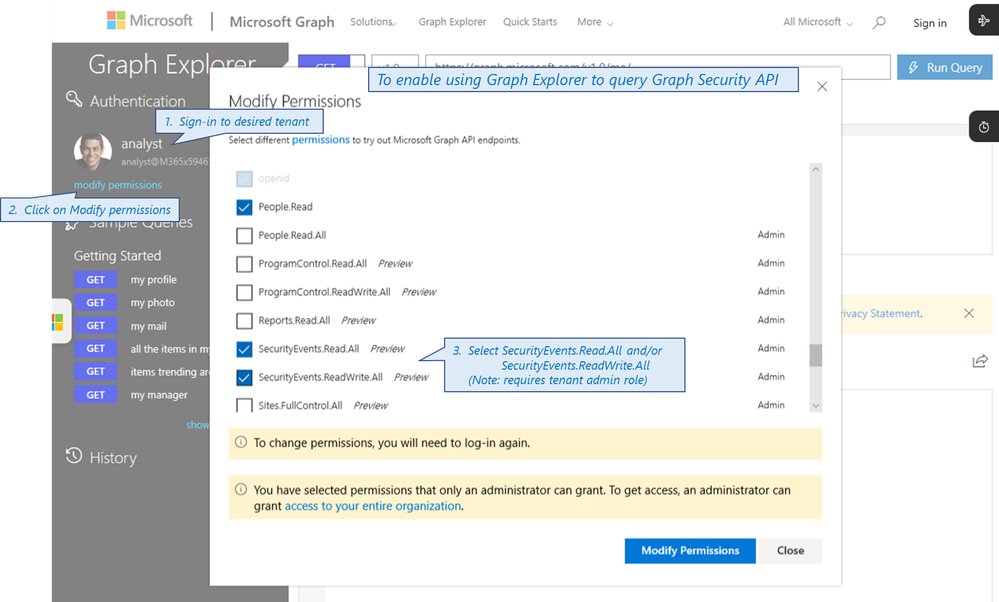
We've received several questions about not being able to see existing alerts using the Graph Explorer.
The reason for this is that the Graph scopes, or permissions, required to call the Graph Security API - SecurityEvents.Read.All, SecurityEvents.ReadWrite.All - are not selected by default in Graph Explorer.
To enable using Graph Explorer, an Azure AD tenant admin must grant these scopes (see figure below)
Once this is done (and the signed in user account is assigned a limited administrator SecurityReader or SecurityAdmin Azure AD role) - alerts may be viewed using the Graph Explorer. Enjoy!
0 Replies