- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Updated: Meltdown and Spectre - new vulnerability in modern processors - the WDATP angle
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
On Jan 3rd, a new serious vulnerability was made public that affects most computers out there. Details of it and what we can do is below in the context of the WDATP suite (both AV and EDR)
What is the fuss all about? This one is big.
In a nutshell, Meltdown and Spectre exploit critical vulnerabilities in modern processors allowing an attacker running user-level, non admin code, to steal kernel memory data breaking the fundamental isolation of layered endpoint security. Simply put, if you have a host running multiple VMs, by running a non-admin code on the host machine you will potentially be able to see and harvest sensitive data belonging to apps running in the VMs.
For a good read on this go to this dedicated website - https://spectreattack.com/
Who is affected? Everyone.
Desktop, Laptop, and Cloud computers may be affected, smartphone. Essentially if you are running a modern CPU (not only Intel) you are at risk.
If this is exploited, is it detectable? It’s tricky.
Exploitation of this vulnerability is VERY hard to detect as it effectively exploits at the CPU level and therefore hard to be generically detected by AV/EDR solutions at large. That said, if an attacker is using this as part of campaign ATP is designed to detect across various stages prior to and after the exploitation. We continue to monitor activity around this exploit and will update our defenses accordingly.
How to get protected? Patch.
It will be eventually a two step conditional operation
- OS Patch for all machines from Microsoft per the MSRC advisory - https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/ADV180002
- Some machines - Firmware patch from the CPU vendors for the microcode. Release is ongoing, check vendor sites
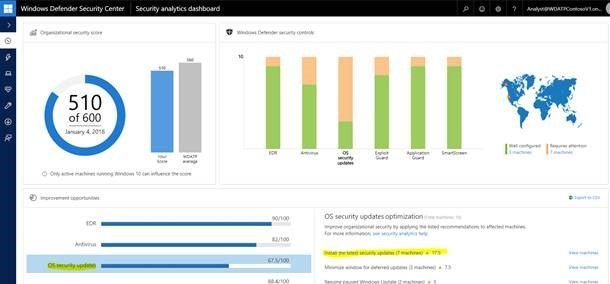
How WDATP can help? Security Analytics can help.
#1 See if the patch was applied to all machines
OS updates will be delivered through Windows Update - see if machines are patched with latest security updates and view unpatched machines under the “OS Security Update” section
#2 (coming) which machines require the firmware patches
Once OS patches will be applied, resulting instrumentation will enable us to collect information about processor versions. As CPU vendors release detailed patch information, we will work to further enhance Security Analytics dashboard to help identify those machines still requiring patching.
Check your 3rd party solutions first. Some might blue screen.
Since the mitigation to this problem involves changes at the OS kernel, there is a possible compatibility issue caused when anti-virus or other 3rd party security applications make unsupported calls into Windows kernel memory.
These calls may cause stop errors (also known as blue screen errors) that make the device unable to boot.
To help prevent stop errors caused by incompatible anti-virus applications, customers will not receive these security updates and will not be protected from security vulnerabilities unless their anti-virus software vendor sets a dedicated registry key.
See here for more details - https://support.microsoft.com/en-us/help/4072699/important-information-regarding-the-windows-securit...
Update: Some AVs are setting the registry key while others are providing KBs with instructions to their customers on how to mass update machines. Adding links to a table listing various AV vendors readiness status. note this is 3rd party info posted by a security influencer, so take it as “best effort” public information on the AV ecosystem.
WDATP and WDAV? Ready. protection is built in.
WDATP and WDAV are compatible with the security updates since they are built into the OS and therefore always certified with the updates.
Ensuring WDAV cloud protection is enabled will serve to expedite the automated patching.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.