|
Lately a lot of customers have been asking if we support Modern Auth for the following topology where SfB and Exchange are onprem (but are not hybrid). The answer is YES! This topology allow you to use features like O365 Multi Factor Auth (MFA) and Intune MAM with your users who are homed onprem.
|
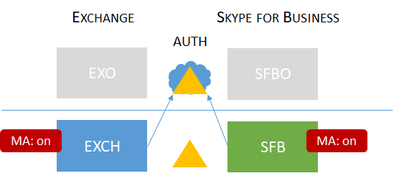
NOTE: Gray components indicate they do not exist in the topology. So, this topology only has Exchange onprem and Skype for Business onprem.
|
The following is a high level explanation of the steps needed to enable Modern Auth for Skype for Business onpremises with AAD. For greater details, you can find them in Carolyn's blog post here. Essentially, these are the first set of steps you would need to do to set up SfB hybrid, but it is not all the steps required.
Note: If you only enable MA for one of the servers (either Exchange or SfB), but not both, your users may see multiple authentication prompts. We recommend you enable MA for both servers to get the best end user experience.
I am going to assume we start with a completely onprem deployment. So, typically, you would only have SfB onprem, Exchange onprem and AD onprem.
To enable Modern Auth on SfB onprem with AAD:
- Ensure you meet the basic pre-reqs for SfB HMA. Namely:
- All SfB servers running 2015 CU5 or greater
- All SfB Front Ends must have outbound access to the internet.
- Get an O365 tenant.
- Add your SIP domain as a Federated domain in Office 365.
- Do this is in the O365 admin portal àSetup àDomain section.
- Do NOT make any DNS changes as the wizard will ask you to do. All DNS records should still point to OnPrem for SFB to work.
- Sync your users from onprem AD to AAD using AADConnect. There are many options here and you can use any option that is officially supported by the AAD team (Password Hash Sync, Pass Through Authentication, Federation with AD onprem, Federation with a 3rd party STS).
- You MUST sync the SFB attributes to AAD. You can see a list of these attributes here.
- If you use the AADConnect wizard, you get these automatically for single forest deployments. If you have a resource forest topology, use the account/resource forest topo here. It joins on ObjectSID and msExchangeMasterAccountSID attributes.
- Assign one user in O365 an SfB license.
- Yes, you will have to buy this one license.
- This user can be the tenant admin user that gets created by default when you create a tenant, or it can be a new user you create. This does NOT mean you have to move any users from SfB onprem to SfBonline. And this user doesn't really have to use the service. Why do you have to do this step? Well, if you don’t, then you cannot do step #4, which is critical. It turns out doing this step hooks up some plumbing to allow you to do step #4.
- Follow the steps in the "Turn on Hybrid Modern Authentication for Skype for Business on-premises" section of this article. The steps can be boiled down to the following:
- Tell AAD about onprem webservice urls.
- This is a very important step. When HMA was in TAP, most (if not all) issues encountered by customers were due to a mistake made in this step.
- Turn on MA for SfB onprem server.
To enable Modern Auth for Exchange on-premises with AAD, you need to follow all the steps described here. Essentially, you will set up Exchange Hybrid and enable HMA but you don’t have to move any mailboxes to Exchange online.
|
