- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Tracking Changes in the Pricing Tier for Microsoft Defender for Cloud
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
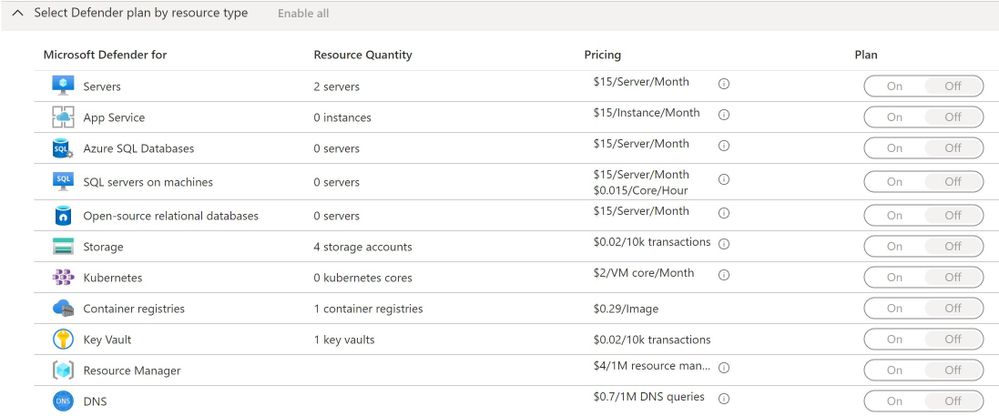
When you enable the enhanced security of Microsoft Defender for Cloud, you have the flexibility to choose which resource type you want to enable with the Defender for Cloud plan which includes: Virtual Machine, SQL Server, App Service and Storage Account.
When all resources are enabled, your subscription coverage will appear as "Fully Covered", and if you have at least one resource type that is not enabled, it will appear as "Partially covered".
In an environment where there are multiple administrators that have privilege to make changes in the pricing tier, it can be challenge to identify who made those changes, since this info is not available in the Microsoft Defender for Cloud dashboard. Luckily we have Azure Activity Log to help you audit changes in your Azure environment, which includes Microsoft Defender for Cloud configurations. I've talked about that previously for another scenario, and here the approach is basically the same. Go to Azure Activity Log to identify who made those changes.
Let's say you want to identify who changed the pricing tier from "fully covered" to "partially covered" by leaving only VM resource type enabled. In the example below you have the complete sequence of changes:
Now you need to open the operation that you want to investigate to see who made the change. When opening the "Update pricing settings" operation, click JSON tab, and there you will see the info that you are looking for, as shown in the example below:
There you have the identity of the user that made the change, the time that the change was made, the resource that was affected by this change, and the type of change that was done.
Note: You can also change the Pricing Tier using PowerShell and ARM Template.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.