- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Re: Microsoft Bitlocker Management from Intune
Microsoft Bitlocker Management from Intune
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 22 2019 07:48 AM
Howdy Folks!
I guess everyone is doing well with the Microsoft as all of you might got inspired much from the session last week held in Las Vegas(Microsoft Inspire)!!
Though I missed it everyone badly as I didn't get chance to visit but the questions keep peeping on my head!!
Now with the BitLocker issue where I guess someone can answer this as well,
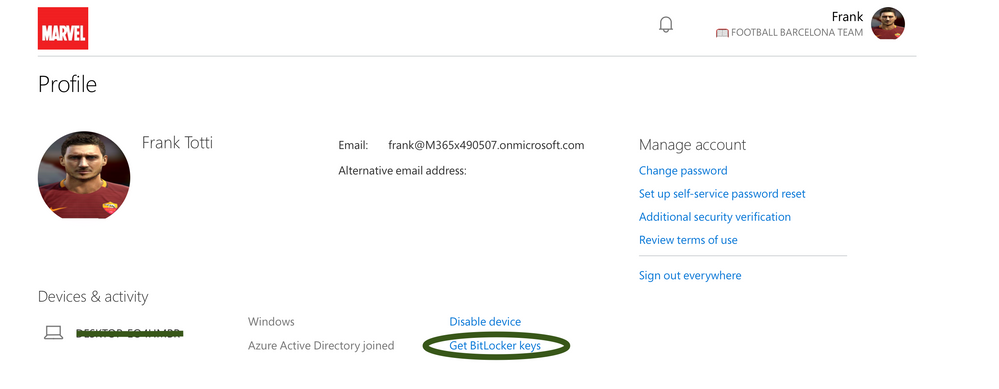
So my query is straight as I need to disable or hide this option of getting the Recovery Keys from the End User level as it is a vulnerable for the Admins to provide the Recovery Keys for OS Encryption Disk like given below with an example
Bitlocker Keys Available from end user level using my apps.microsoft.com
Is there any option from the administrator level from Azure Portal to hide this Keys from the end user side??
Please help me out as customer is seeking help for this!!
- Labels:
-
Bitlocker Encryption
-
Microsoft Intune
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 29 2019 02:26 PM
Hey @Mitul Sinha,
as far as I know it, there is no option to disable this. It is designed as a self-service with no option to disable it in the portal.
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 29 2019 09:51 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2019 08:35 AM - edited Jul 30 2019 08:37 AM
And there is one more question @Oliver Kieselbach just clicked on my mind..Suppose BitLocker PIN if I reset it then will it generate the new recovery key or store the new recovery key in my apps.microsoft.com or not?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2019 08:51 AM
Hey @Mitul Sinha,
what do you mean by MFA and BitLocker exactly? You can disable Windows Hello for Business, which would enforce you to do MFA for the Hello PIN creation (this PIN is only for WHfB!) and disable the AADJ MFA requirement, then you end up in a situation, that you can enroll a device without doing MFA. With the correct BitLocker policies in place, the Intune device will get encrypted and the key will backup to AAD.
A key rotation like MBAM implemented this for domain joined clients, is currently not available. Although, the implementation with MBAM was a key rotation after BitLocker key usage, not the BitLocker pre-boot PIN reset. The pre-boot BitLocker PIN is used to protect access to the TPM further. While TPM-only verifies just the integrity of the platform (hardware and a few firmware/software components) to control access to the TPM. So, even in the domain join scenario pre-boot auth PIN reset (aka BitLocker PIN reset) did not rotate the BitLocker recovery key. Native BitLocker key rotation in Intune is currently not available.
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2019 09:58 AM
For a successful Encryption we must have to set up the Windows 10 PIN. Though we haven't pushed any MFA or PIN policies from Intune.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2019 11:08 AM
SolutionHey @Mitul Sinha,
then I think your test setup had a different problem because there is no dependency on MFA for BitLocker enablement. To really confirm my statement I verified it in my test tenant right now. I disabled all MFA (AADJ & WHfB), enrolled a device, didn't see any MFA prompt (no MFA at all) and my BitLocker policies in Intune enabled encryption and my AADJ device is encrypted. BitLocker key is in AAD and everything is fine in the Intune portal (green icons - configurations successful applied).
So, again BitLocker has no dependency to MFA and can be enabled without MFA. Your problem in your tests seems to be rooted somewhere else.
Key rotation is currently not available but BitLocker is functional without MFA.
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2019 09:02 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 31 2019 04:26 AM
@Oliver So I have tested it out today came up with this screenshot as it always ask this option. Before asking if the Windows Machine has fingerprint I must have to set that as well so I set both the options MFA as well as PIN for Windows and then Encryption done for BitLocker but yes I didn't get any BitLocker PIN to setup as Device Configuration Policies didn't push and got error.
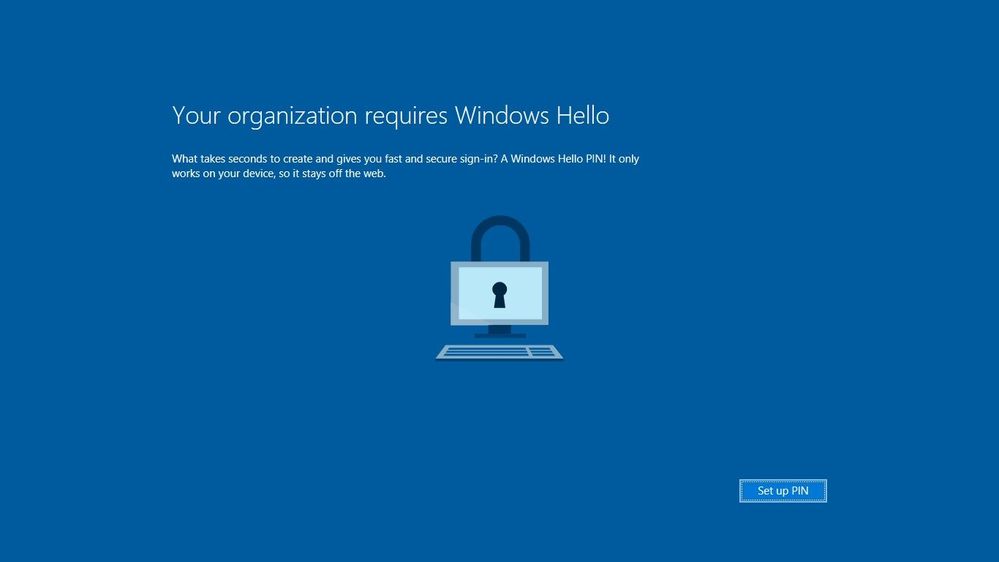
Windows PIN at Startup
Device Configuration got failed from Intune but Device Compliance Got Successful

Device Compliance Successful

Device Configuration Failed
Please let me know how we can achieve successful Bitlocker encryption with Bitlocker PIN should appear!!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 31 2019 05:04 AM
Hey @Mitul Sinha,
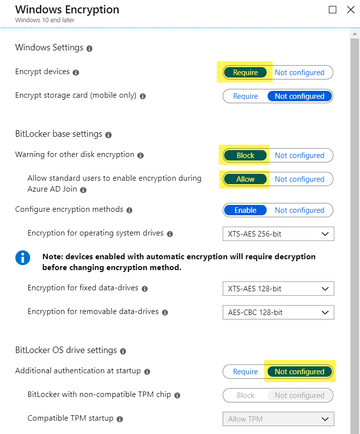
for silent encryption you have to skip the startup to require PIN settings. PIN can only achieved by using the Wizard which is user driven. Silent auto encryption is TPM-only. Can you please test automatic encryption with the following settings (no additional authentication at startup):
In addition I have a guide here:
Enabling BitLocker on non-HSTI devices with Intune
https://oliverkieselbach.com/2018/10/23/enabling-bitlocker-on-non-hsti-devices-with-intune/
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 31 2019 06:13 AM - edited Jul 31 2019 06:32 AM
There you go...that's where customer is looking to get the prompt of Encryption instead of having an auto one!! So let me setup the Additional Authentication at startup as "not Configured"
But I must have to setup the BitLocker PIN to ask as per client's request!! In that case how will I able to disable this policy which you mentioned about "Additional Authentication at startup"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 02 2019 02:56 AM
Hey @Mitul Sinha,
I have a guide for this here:
How to enable pre-boot BitLocker startup PIN on Windows with Intune
best,
Oliver
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 02 2019 10:55 PM
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 30 2019 11:08 AM
SolutionHey @Mitul Sinha,
then I think your test setup had a different problem because there is no dependency on MFA for BitLocker enablement. To really confirm my statement I verified it in my test tenant right now. I disabled all MFA (AADJ & WHfB), enrolled a device, didn't see any MFA prompt (no MFA at all) and my BitLocker policies in Intune enabled encryption and my AADJ device is encrypted. BitLocker key is in AAD and everything is fine in the Intune portal (green icons - configurations successful applied).
So, again BitLocker has no dependency to MFA and can be enabled without MFA. Your problem in your tests seems to be rooted somewhere else.
Key rotation is currently not available but BitLocker is functional without MFA.
best,
Oliver