- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Intune MAM Delve app dataloss issue?
Intune MAM Delve app dataloss issue?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 27 2018 02:37 AM
We have set up conditional access policy requiring approved apps for access to Office 365 data
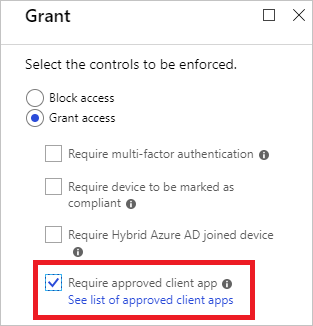
The documentation https://docs.microsoft.com/en-us/azure/active-directory/conditional-access/technical-reference#appro... lists Microsoft Delve as one of the client apps. It goes on to say "The approved client apps support the Intune mobile application management feature."
In Intune we have set up iOS app protection policy for Word, Excel etc., Delve is not a choice here. We add Delve using the bundle id, with the result that the sign-in in the Delve app now registers the device through Authenticator. None of the other app policy settings are applied however, no PIN requirement, copy paste is allowed to any app etc. These are restrictions we have working in the other apps such as Word and Excel.
In the Delve app users can still read all accessible documents from O365 with no PIN prompt and copy/paste anywhere. How do we prevent this so not to render the policy pointless? Does anyone have a recipe for blocking access to the Delve app (through conditional access?), or any way of managing the app properly?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 06 2018 04:05 PM
SolutionThis can by remediated by creating a Conditonal Access policy targeted to Office Delve and IOS/Android devices. Setting that to block will prevent access. Microsoft should really update their list of apps approved for CA for mobile though as we noticed the same thing.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 17 2018 01:41 AM
@esmugala wrote:This can by remediated by creating a Conditonal Access policy targeted to Office Delve and IOS/Android devices. Setting that to block will prevent access. Microsoft should really update their list of apps approved for CA for mobile though as we noticed the same thing.
This works well, with the one caveat that Delve/My profile is not accessible anymore i Edge when browsing SharePoint Online sites in the tenant from iOS devices. Acceptable stop-gap I suppose whilst waiting for Microsoft to remedy this properly.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 08 2020 09:18 AM
@Vegard Strømsøy What bundle id did you use for the iOS app protection policy here?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 09 2020 01:30 AM
@Samuel Aderemi we created a conditional access policy which targets cloudapp Office Delve (94c63fef-13a3-47bc-8074-75af8c65887a)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dec 06 2018 04:05 PM
SolutionThis can by remediated by creating a Conditonal Access policy targeted to Office Delve and IOS/Android devices. Setting that to block will prevent access. Microsoft should really update their list of apps approved for CA for mobile though as we noticed the same thing.