- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune
- Azure AD Join via Office 365 installation!?
Azure AD Join via Office 365 installation!?
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 12 2019 12:07 AM - edited Jul 12 2019 12:53 AM
Hi All,
The company i manage Intune for, states that when installing office 365 on their private device and they sign in to it, they join Azure AD. I've checked my devices in intune and this is really the case...
I've found out that Automatic Enrollment was set to All users.
How can i prevent users for not Azure AD joining via an Office 365 installation or Private device?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2019 01:31 PM - edited Jul 15 2019 01:32 PM
SolutionHi @Abdelhakim_Y95,
actually the device does not Azure AD join, it gets Azure AD registered. This is a slight difference as you still logon via your user you used before. With Azure AD join you would logon after Azure AD join with the Azure AD user afterwards. Regarding your concern about private devices, this would be the same. I assume you won't like to have private devices managed by Intune. As soon as they get registered (aka Workplace Join) they receive Intune policies for example. With auto enrollment an Azure AD register will end up in a device MDM managed by Intune. If we talk about Windows 10 you could easily prevent Azure AD join via:
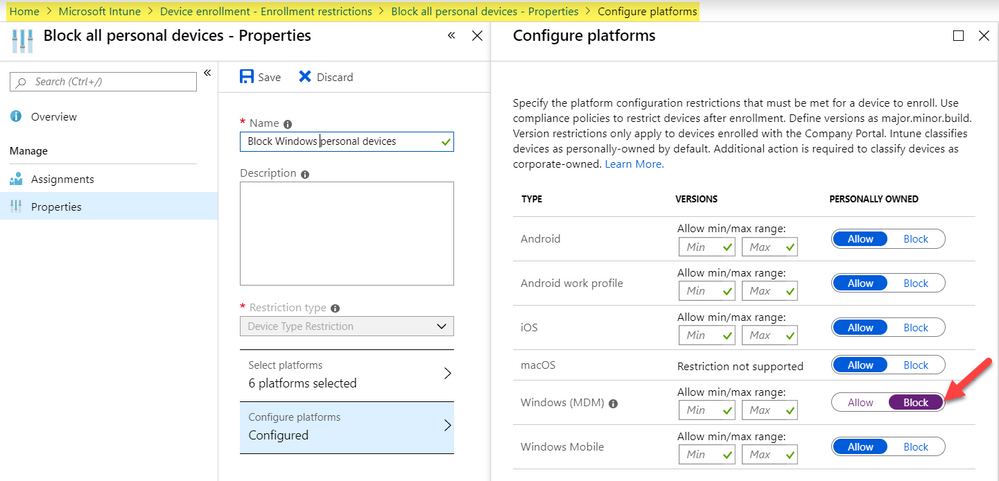
device enrollment > enrollment restrictions > device type restriction > new policy > Properties > configure platforms > Windows (MDM) set to "Personally Owened" > Block
This will only allow Windows Autopilot devices to enroll into MDM and block personal devices
see: https://docs.microsoft.com/en-us/intune/enrollment-restrictions-set
Blocking personal Windows devices
If you block personally owned Windows devices from enrollment, Intune checks to make sure that each new Windows enrollment request has been authorized as a corporate enrollment. Unauthorized enrollments will be blocked.
The following methods qualify as being authorized as a Windows corporate enrollment:
- The enrolling user is using a device enrollment manager account.
- The device enrolls through Windows AutoPilot.
- The device is registered with Windows Autopilot but isn't an MDM enrollment only option from Windows Settings.
- The device’s IMEI number is listed in Device enrollment > Corporate device identifiers. (Not supported for Windows Phone 8.1.)
- The device enrolls through a bulk provisioning package.
- The device enrolls through GPO, or automatic enrollment from SCCM for co-management.
The following enrollments are marked as corporate by Intune. But since they don't offer the Intune administrator per-device control, they'll be blocked:
- Automatic MDM enrollment with Azure Active Directory join during Windows setup*.
- Automatic MDM enrollment with Azure Active Directory join from Windows Settings*.
The following personal enrollment methods will also be blocked:
- Automatic MDM enrollment with Add Work Account from Windows Settings*.
- MDM enrollment only option from Windows Settings.
* These won't be blocked if registered with Autopilot.
best,
Oliver
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 15 2019 01:31 PM - edited Jul 15 2019 01:32 PM
SolutionHi @Abdelhakim_Y95,
actually the device does not Azure AD join, it gets Azure AD registered. This is a slight difference as you still logon via your user you used before. With Azure AD join you would logon after Azure AD join with the Azure AD user afterwards. Regarding your concern about private devices, this would be the same. I assume you won't like to have private devices managed by Intune. As soon as they get registered (aka Workplace Join) they receive Intune policies for example. With auto enrollment an Azure AD register will end up in a device MDM managed by Intune. If we talk about Windows 10 you could easily prevent Azure AD join via:
device enrollment > enrollment restrictions > device type restriction > new policy > Properties > configure platforms > Windows (MDM) set to "Personally Owened" > Block
This will only allow Windows Autopilot devices to enroll into MDM and block personal devices
see: https://docs.microsoft.com/en-us/intune/enrollment-restrictions-set
Blocking personal Windows devices
If you block personally owned Windows devices from enrollment, Intune checks to make sure that each new Windows enrollment request has been authorized as a corporate enrollment. Unauthorized enrollments will be blocked.
The following methods qualify as being authorized as a Windows corporate enrollment:
- The enrolling user is using a device enrollment manager account.
- The device enrolls through Windows AutoPilot.
- The device is registered with Windows Autopilot but isn't an MDM enrollment only option from Windows Settings.
- The device’s IMEI number is listed in Device enrollment > Corporate device identifiers. (Not supported for Windows Phone 8.1.)
- The device enrolls through a bulk provisioning package.
- The device enrolls through GPO, or automatic enrollment from SCCM for co-management.
The following enrollments are marked as corporate by Intune. But since they don't offer the Intune administrator per-device control, they'll be blocked:
- Automatic MDM enrollment with Azure Active Directory join during Windows setup*.
- Automatic MDM enrollment with Azure Active Directory join from Windows Settings*.
The following personal enrollment methods will also be blocked:
- Automatic MDM enrollment with Add Work Account from Windows Settings*.
- MDM enrollment only option from Windows Settings.
* These won't be blocked if registered with Autopilot.
best,
Oliver