- Home
- Security, Compliance, and Identity
- Microsoft Defender for Endpoint Blog
- Inside SecOps: Are we impacted by this new APT campaign?
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Inside SecOps is a new series of blog posts that we’ll be publishing to showcase how security analysts inside Security Operations Centers (SOC) are leveraging Windows Defender ATP.
My name is Milad Aslaner (@MiladMSFT on Twitter) and I’m a security professional in the Windows Defender Advanced Threat Protection (ATP) product engineering team. In my role, I’ve had the privilege of learning how strategic customers are using our product. This has proven to be an invaluable source of feedback which has helped us not only improve existing capabilities but also build new features from the ground up.
In this blog post, we’ll focus on two capabilities that can help analysts determine if a newly disclosed Advanced Persistent Threat (APT) campaign affects their organization:
- Advanced hunting
- Custom detections
Consider the following scenario: You start your day as a security analyst by catching up on e-mails, threat intelligence feeds, and cybersecurity related news. You notice that a newly disclosed indicator of compromise (IOC) has just been disclosed by a computer emergency response team (CERT). According to the CERT report the threat actor group specializes in the same industry as the company you work for.
What do you do?
The CERT provides a list of known IOC’s. These IOC’s contain malicious file hashes, domains and IP addresses. In order to assess if your organization is affected by the threat, it’s prudent to verify if those IOCs can be found in your environment.
Windows Defender ATP is connected to the Microsoft Intelligent Security Graph (ISG). It’s highly likely that the IOCs you’ve just read about are already known and monitored by Microsoft but as any diligent security analyst, you’ll want to verify that.
With Advanced hunting and the new custom detection capabilities you can do just that!
Advanced hunting allows you to create queries using Kusto Query Language. You’ll have access to 30 days’ worth of raw data where you can run your queries on.
When you’ve made your queries, you can save it as a detection logic, which will then raise custom alerts.
Example IOCs
The following list of IOCs are a subset of a recently disclosed campaign by Unit42, but we’ll use them later to demonstrate how to assess if a threat actor group has made an impact in an organization:
Domains:sydwl.cn, dwn.rundll32.ml, w3w.aybc.so, a.ssvs.space
IP addresses: 118.24.150.172, 120.55.54.172
Advanced hunting
If you are not familiar with Advanced hunting, I recommended that you check out the official documentationand the blog post on how to get started.
Based on the sample IOC list in the previous section, I’ve created the following sample query to determine if:
- any endpoint in the organization had connections to the malicious URLs,
- any endpoint in the organization had connections to the malicious IP addresses
NetworkCommunicationEvents
| where RemoteIP in (
"118.24.150.172","120.55.54.172")
or RemoteUrl in ("sydwl.cn","dwn.rundll32.ml","w3w.aybc.so","a.ssvs.space")
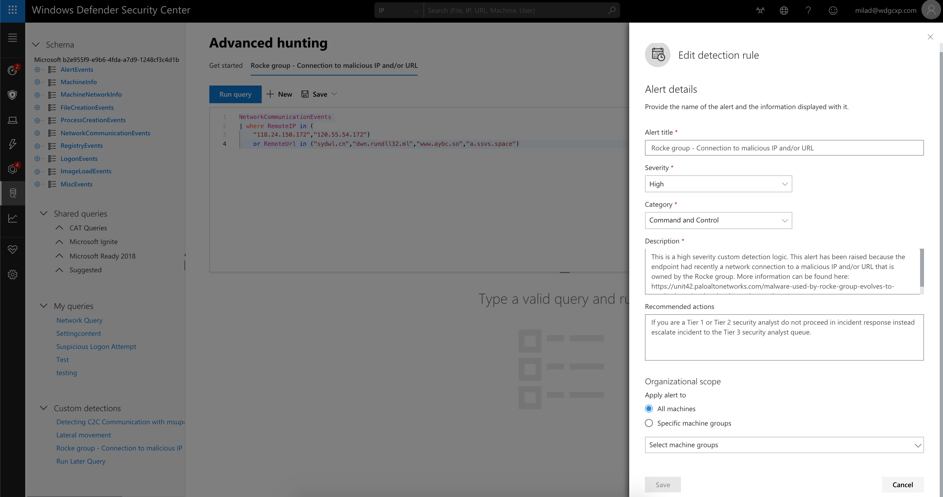
Custom detection
Custom detections build on top of Advanced hunting. Essentially instead of running manual queries you can save them as custom detections. Once saved, queries will run automatically every 24 hours, creating alerts complete with your own description, categorization and severity. See the image below for a custom detection rule that raises a high severity alert when it detects any machine in the organization connecting to any of the IP or URLs described in the above query.
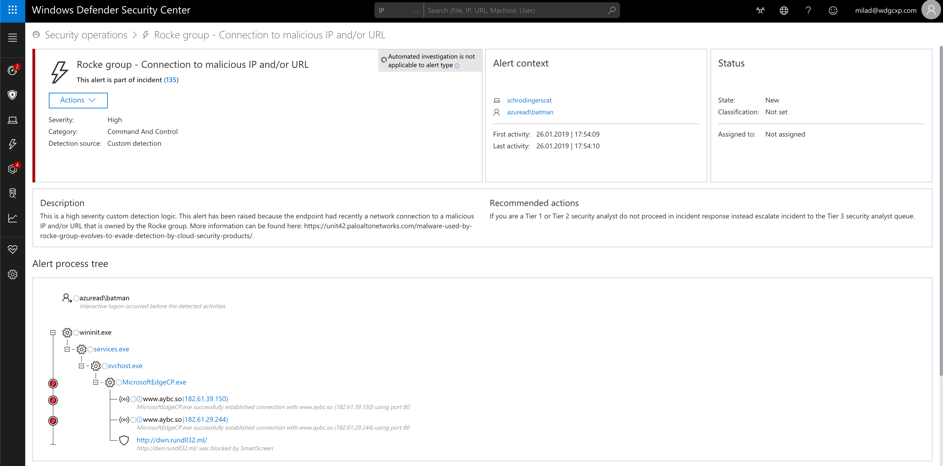
True Positive
After learning about the new APT campaign, you have created an Advanced hunting query and a custom detection. Following these actions, you receive a new alert from your custom detection, indicating a true positive in your environment - alert for an endpoint that has executed one of the known bad files.
Alert raised based on newly created custom detection
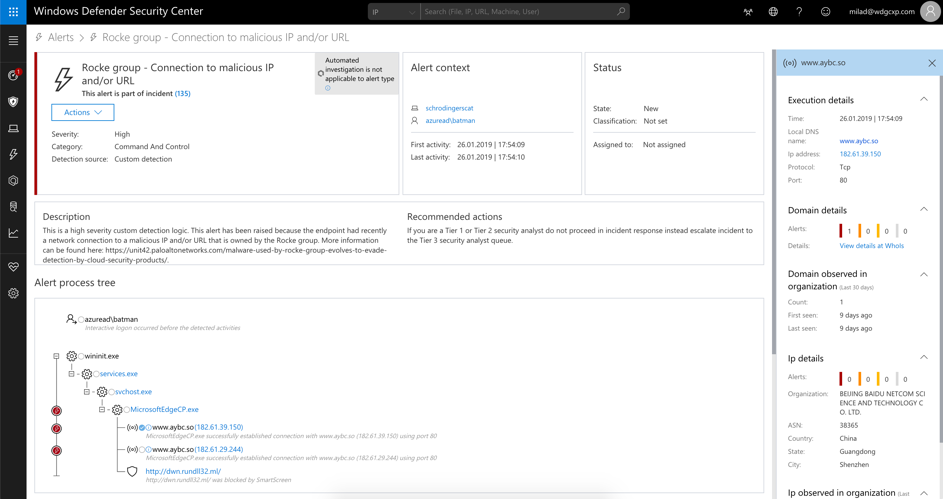
Clicking on the circle next to the domain provides further insights about the domain
Clicking on the URL provides more context about the impact within the organization
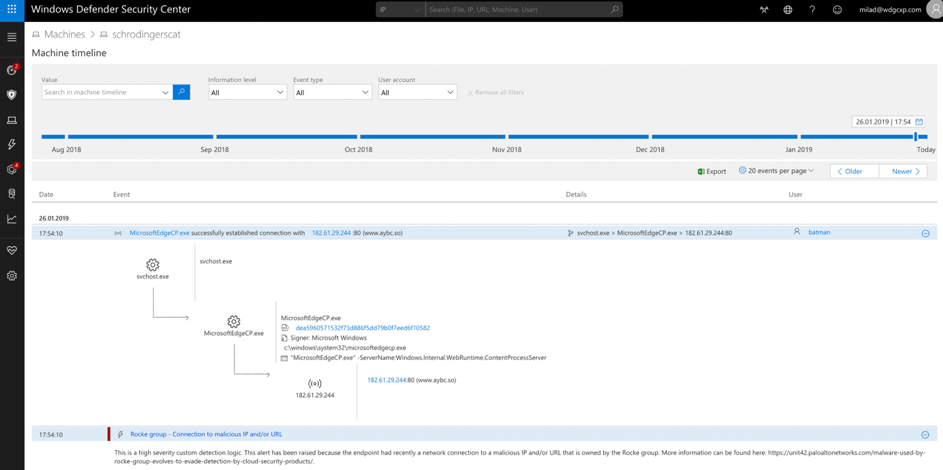
From the alert you are able to go to the respective machine page to further deep dive into the machine timeline.
Conclusion
As a security analyst in a SecOps team, there are instances when you need to quickly determine if your organization has been impacted by a specific campaign. Advanced hunting is one of the most loved capabilities in Windows Defender ATP which can help meet that need. As demonstrated in the example, all you need to do is create a query to check if there’s been direct impact in your environment. Custom detections build on top of Advanced hunting and lets you quickly transform the queries into custom detections that surface up as alerts in Windows Defender Security Center. Now all that is needed is to get engaged with your network team to block the access to the malicious URLs.
I hope you found this tutorial useful. I encourage you to take advantage of the Advanced hunting and custom detection capabilities, provide feedback, or ask questions about this post.
Recommended Reading
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.