- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Support Tip - How to configure NDES for SCEP certificate deployments in Intune
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hi everyone, today we have another post from Intune Support Escalation Engineer Mingzhe Li. In this post, Mingzhe goes through setting up and configuring NDES for SCEP certificate deployments in Intune. There are a few different ways you can setup NDES and we have our official documentation on this here, but if you’re looking for a simple step-by-step guide for a single certificate scenario with lots of details and screen shots, this post is for you.
=====
The purpose of this post is to provide an easy, end-to-end guide on setting up a SCEP infrastructure for Microsoft Intune. When working on this topic as a Support Engineer, many customers ask me for a simple tutorial with as many screenshots as possible. In response to that, I decided to write this article with the hopes that it will help you too and make getting this setup as easy as possible.
When talking about NDES and SCEP, I like breaking the process up into three parts:
- Installing the NDES server
- Configuring the NDES server
- Creating the SCEP profile in the Intune portal
We’ll walk through each of these in order, however before you start please go through the pre-requisites for setting up SCEP which are described here: https://docs.microsoft.com/en-us/intune/certificates-scep-configure.
1. Installing the NDES server
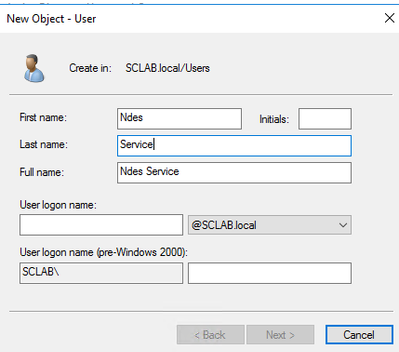
Before we install the NDES server, we first need to create a new service account in your Active Directory domain using Active Directory Users and Computers. This is the account that will be used to request the SCEP certificate from your Enterprise Certification Authority (CA).
Once the account is created, go to the computer you want to use for the NDES role and run compmgmt.msc (Note that the NDES computer should be running Windows Server 2012 R2 or later). Add the newly created account into the local group IIS_IUSRS:
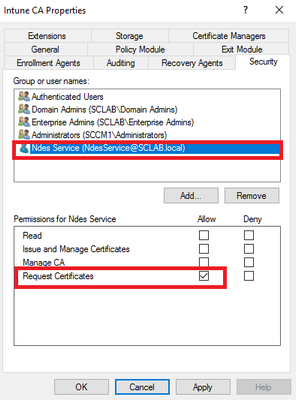
Next, we need to add the proper permissions for this account on your Enterprise CA. Logon to your Enterprise CA and add the NDES service account on the Security tab with ‘Request Certificates’ permissions:
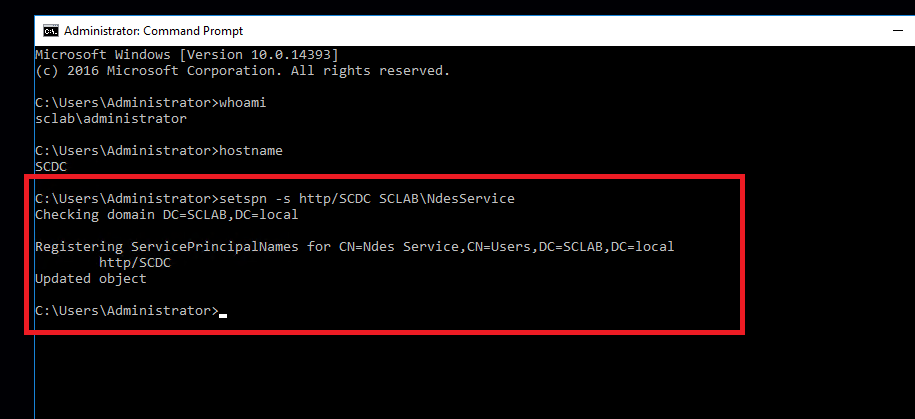
Now we need to set the SPN for the NDES service account. Logon to your NDES server, open command prompt, then run the command below:
setspn -s http/<computer name of NDES server> <domain name>\<NDES service account name>
This will set the SPN for your NDES service account.
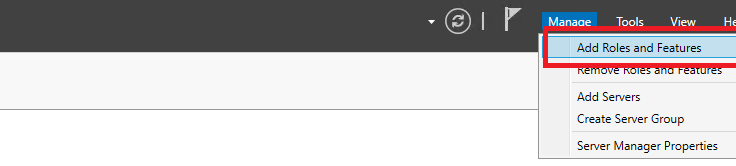
That’s it for the account, so now we can start with the configuration of the NDES computer. On the computer you want to use for the NDES role, open Server Manager and select Add Roles and Features:
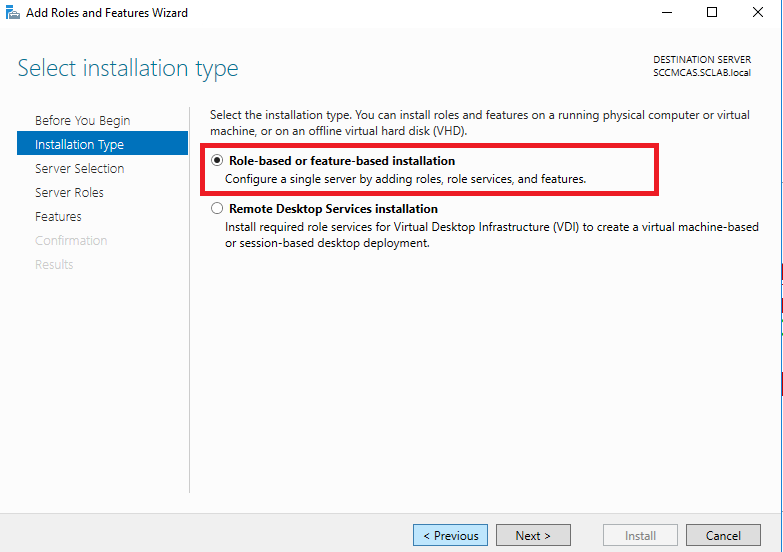
Choose Role-based or feature-based installation:
Add the ADCS role:
Add the NDES role:
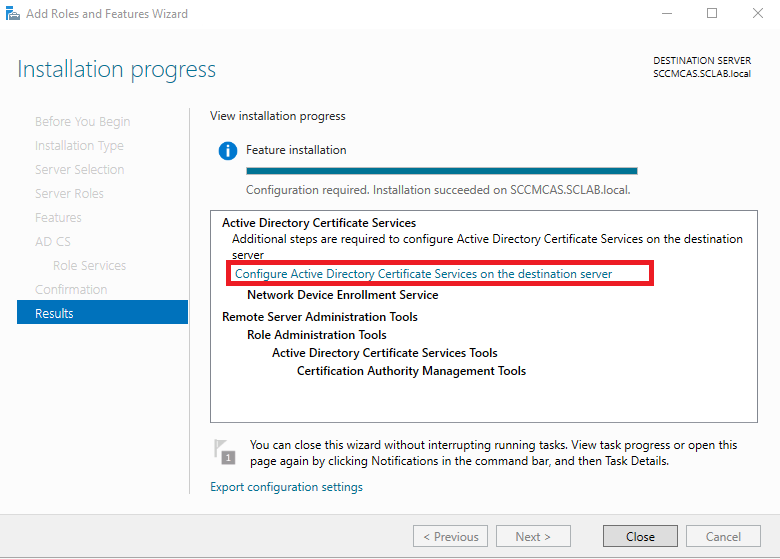
Wait until installation completes, then start the post-installation steps:
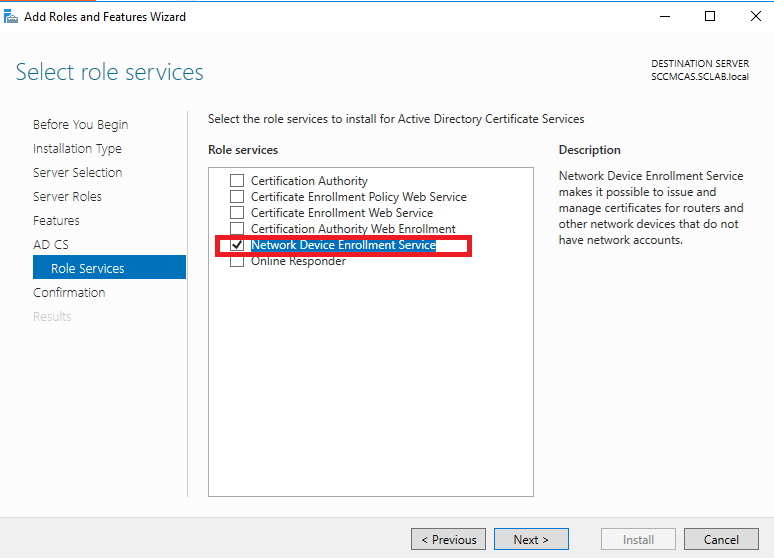
Choose Network Device Enrollment Service:
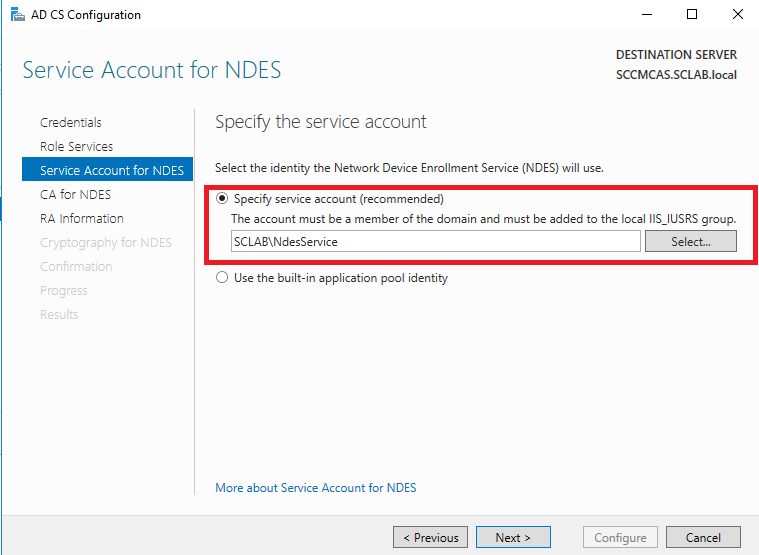
Next, choose the NDES service account you created for the service account:
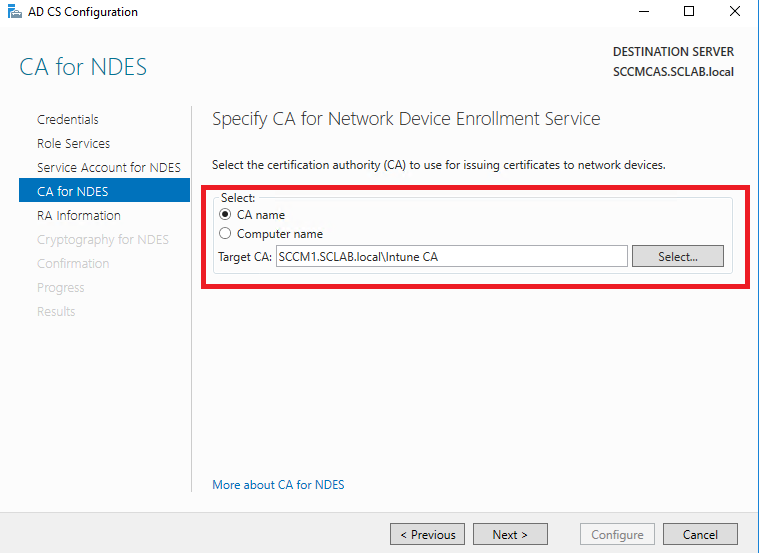
Now we need to connect your Enterprise CA with the NDES server. Please note that the CA and the NDES server must be installed on separate servers.
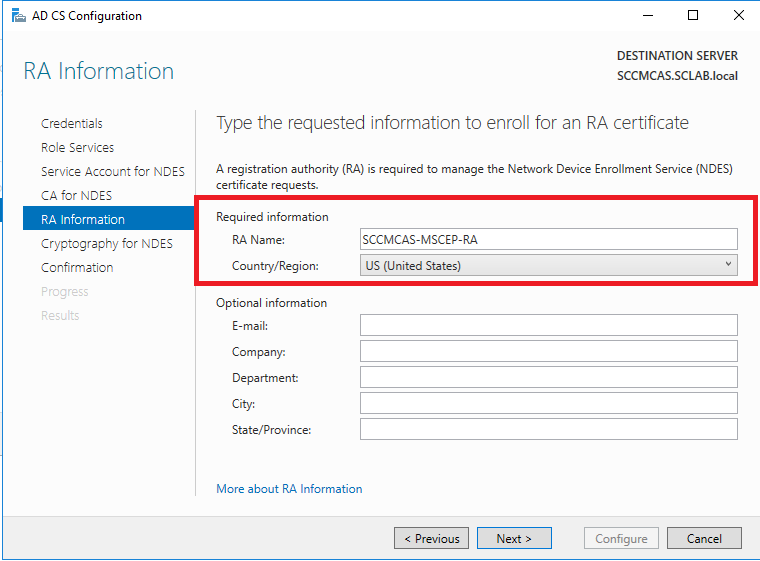
Leave RA Information set to the defaults. This information will be used when the signing certificate is created:
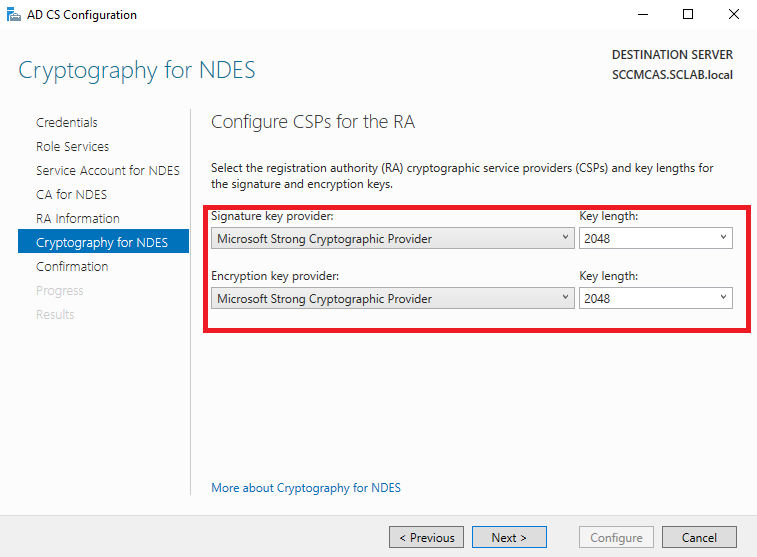
Configure the cryptography as shown below:
Continue through the wizard to complete the installation of NDES. Once the installation completes, we now need to do a few steps to finish configuring the NDES computer.
2. Configuring the NDES server
The NDES server needs to accept long URL requests so we first need to configure IIS accordingly. On the NDES computer, open IIS Manager and select Default Website -> Request Filtering then select Edit feature settings’:
Configure Maximum URL length and Maximum query string as shown below:
Next, launch Registry Editor (regedit) and go to HKLM\SYSTEM\CurrentControlSet\Services\HTTP\Parameters, then edit the values as shown here:
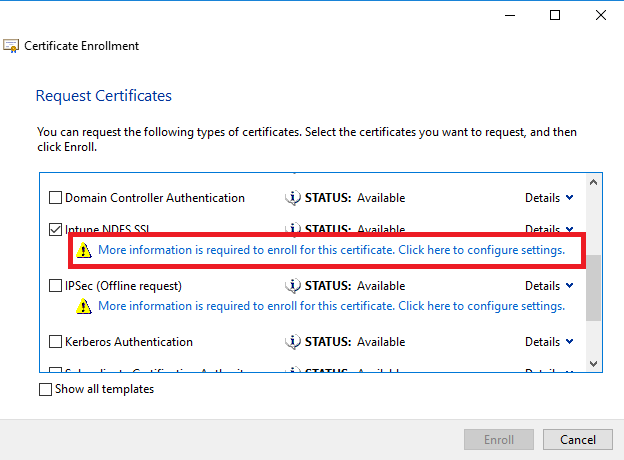
These settings will make sure that the NDES server can receive https requests which are large in size. If this is not done, none of your devices will be able to receive a SCEP certificate profile and you’ll see the following authentication error messages within the Intune Ibiza portal:
Experiencing authentication issues
The portal is having issues getting authentication tokens for Microsoft_Intune_DeviceSettings
As a next step, we need publish your NDES server to the Internet and generate an external FQDN. In this article we do this using Azure Application Proxy, however you can achieve the same by using the Windows Application Proxy (WAP).
Open your Azure portal and go to Enterprise Applications:
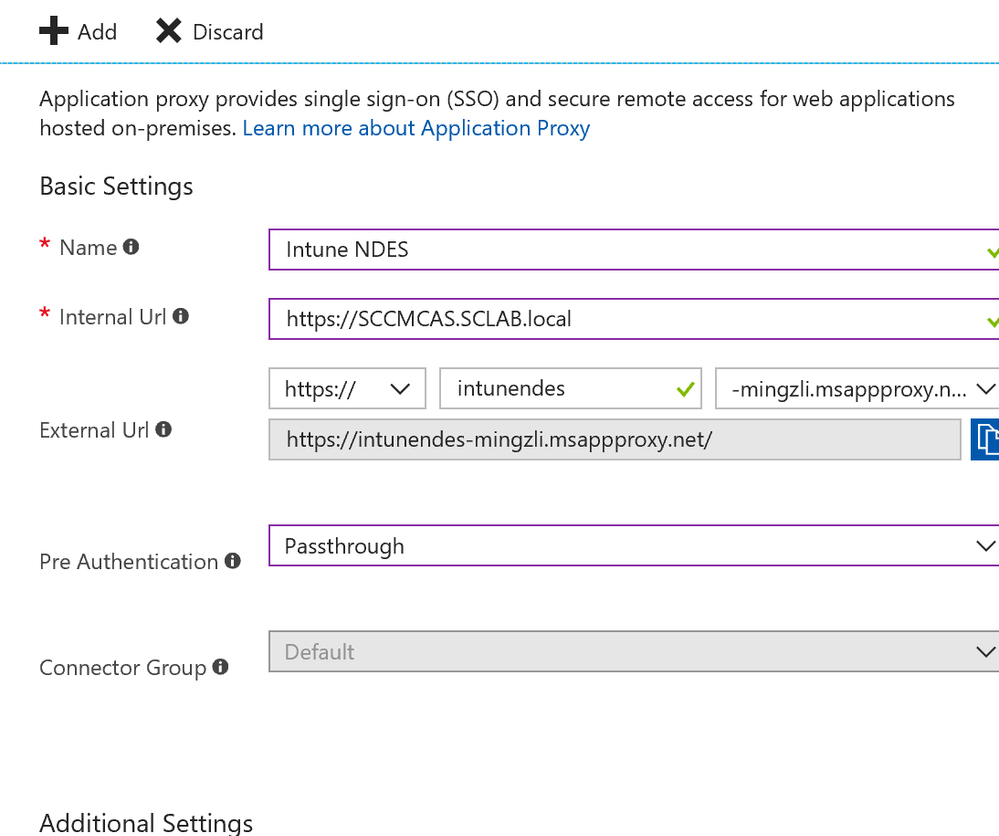
Click on ‘Add application’ and select the ‘On-premises application’.
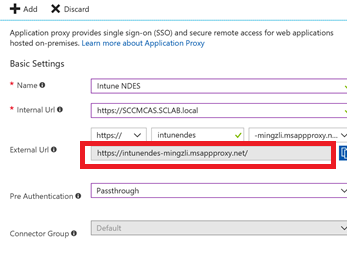
Configure the settings as shown below, using the internal FQDN of your NDES server for Internal URL:
Make a note of External Url (this will be generated automatically). You will need this at a later point in time.
Now we need to create an SSL certificate template on the Enterprise CA and assign a client/server authentication certificate to the NDES server. The reason behind this is that all certificate requests to the NDES server will come from the Internet and therefore, the communication needs to be encrypted.
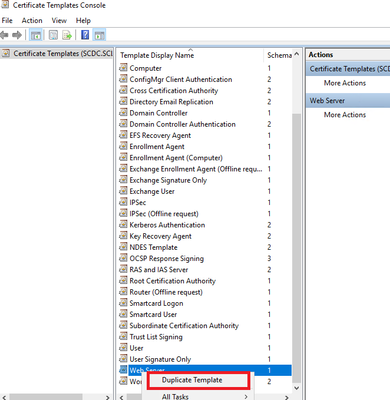
Log on to your Enterprise CA and launch the CA console. Go to Certificate Templates and right-click on Manage, then duplicate the Web Server template:
Assign an appropriate name to the duplicated certificate template (e.g. NDES SSL certificate).
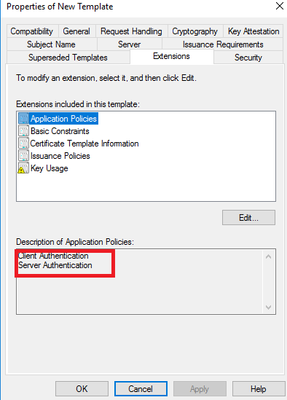
The certificate should include both client and server authentication under Extensions tab -> Application policies. On the Security tab, the computer account of the NDES server should have Read and Enroll permission:
On the Subject Name tab, make sure that Supply in the request is checked.
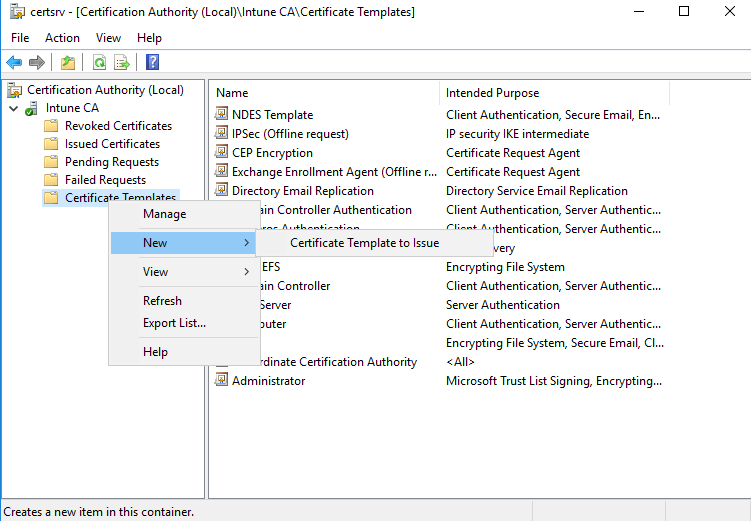
Now we need to issue the new template. Go to Certificate Templates and right-click on New, select Certificate Template to Issue then choose the SSL template you just created:
Now we need to go to the NDES computer and add the client/server authentication certificate. Open the MMC console on your NDES server and add the certificate snap-in for the local computer. Request a new certificate under Personal -> Certificates -> All Tasks -> Request New Certificate:
Select the SSL certificate template you just created on the Enterprise CA as shown below:
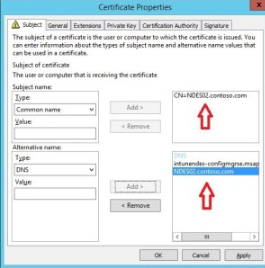
Fill in the information on the next screen according to the guidelines below:
Subject name:
- Type = Common name
Value = <NDES server internal FQDN>
Alternative name:
- Type = DNS
Value = <NDES server internal FQDN>
- Type = DNS
Value = <NDES server external FQDN>. This is the external FQDN that was previously generated on the Azure Application Proxy:
Here is an example:
Click OK to finish adding the certificate.
Now we need to bind our server authentication certificate in IIS. On the NDES computer, connect to your IIS console and go to Default Web Site -> Bindings. Click Add and bind the certificate on https port 443. Select the SSL certificate template you just created on the Enterprise CA.
Restart your NDES server.
The next step is to create the NDES certificate template. This template will be used to issue certificates to our Intune devices. Log on to your Enterprise CA and start the CA console. Right-click on Certificate Templates and select Manage), then duplicate the User template:
Give your new template a display name and make a note of the generated Template name as you will need this later. On the Subject Name tab, select the Supply in the request option:
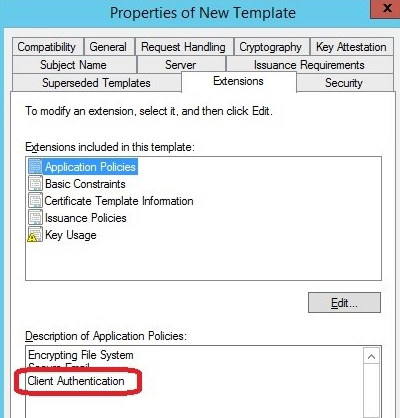
On the Extensions tab, make sure that Client Authentication is available under Application Policies.
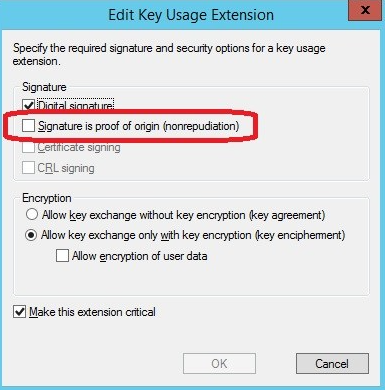
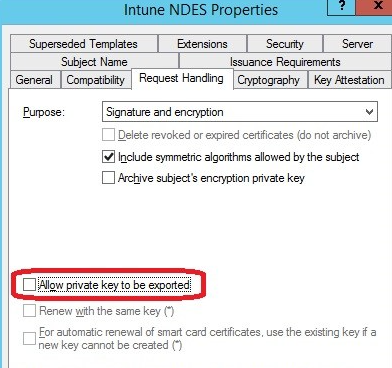
On the same tab, click on Edit and un-check the option Signature is proof of origin (nonrepudiation). This is required if the certificate is going to be assigned to iOS devices. Also make sure that you do not allow the private key to be exported on the Request Handling tab:
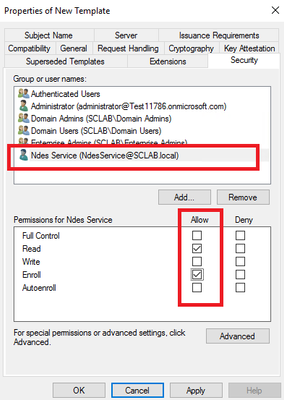
Now, add Read and Enroll permission to the NDES service account for the new template on the Security tab. On the Cryptography tab, the minimum key size should be 2048.
Go back to the Certificate Authority management console and select Certificate Templates. Right-click and choose New -> Certificate Template to Issue, then select the template you just created:
Now the question is ‘How does the NDES server know which certificate template to request from the CA?’ The first step is to identify the purpose of the template that you just created which can be checked on the Request Handling tab:
In our example, the purpose is Signature and encryption. We need to map this information to the registry keys on the NDES computer. To do this, logon to your NDES computer, run regedit and navigate to HKLM\Software\Microsoft\Cryptography\MSCEP. You will see 3 registry entries:
- SignatureTemplate (corresponds to Signature purpose)
- EncryptionTemplate (corresponds to Encryption purpose)
- GeneralPurposeTemplate (corresponds to Signature and encryption purpose)
We have selected Signature and encryption as the template purpose, so we need to enter the template name as a key value for the GeneralPurposeTemplate key:
At this point you might have noticed that so far, our actions were not related to Microsoft Intune and we have done everything on our on-premise servers. With this complete, now it’s time to connect our on-premise service to the Microsoft Intune cloud. The interface between Intune and your NDES computer is the Intune Connector which we will install now.
Logon to the Intune Portal and navigate to Device Configuration -> Certificate Connectors -> Add and download the connector installation file:
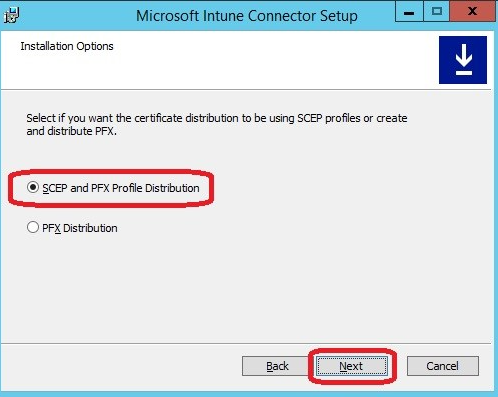
Copy the file to your NDES server and start the installation with Administrative rights. When the wizard starts, first select the option below:
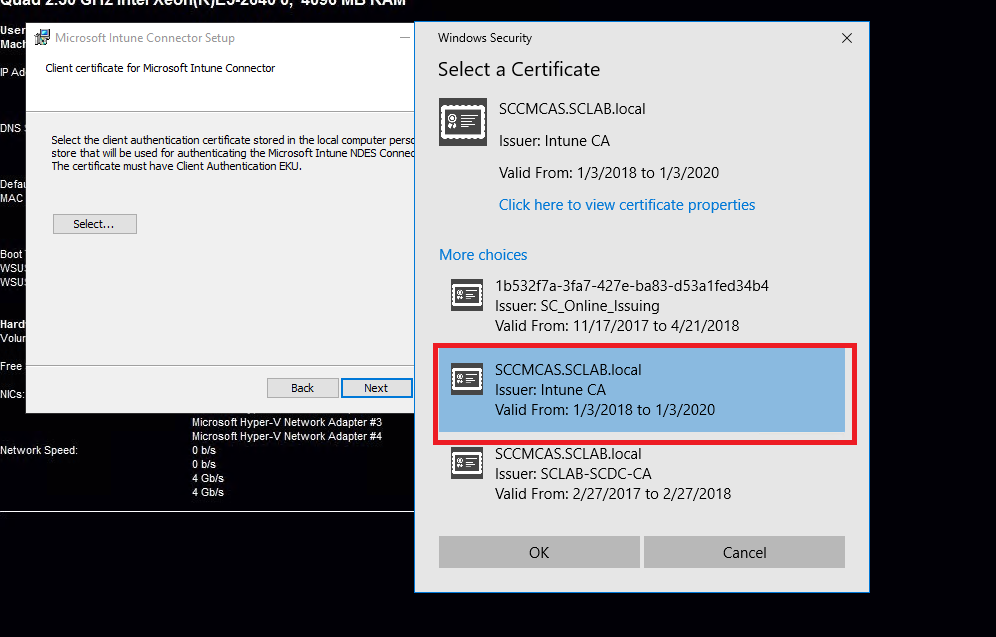
Follow the instructions and select the correct NDES SSL certificate:
Please note that the certificate chosen here is the SSL certificate for client/server authentication which we created in the beginning!
Once the installation finishes you will see the screen below. Sign-in into your Intune tenant:
IMPORTANT The sign-in account needs to be a Global Administrator or an Intune Administrator!
Once the sign-in is completed, Intune can now communicate with your NDES computer. Note that you can re-launch the above screen any time by running <Intune_Connector_Install_Path>\NDESConnectorUI\NDESConnectorUI.exe.
Restart the NDES server after the installation of Intune Connector.
3. Creating the SCEP profile in the Intune portal
At this point we’ve completed the installation and configuration of our NDES server and connected our on-premise environment to Intune, so now it’s time to create the SCEP profile in the Intune portal and deploy it to our target devices.
A requirement for deploying a SCEP profile is the successful deployment of the trusted root certificate from your CA to your targeted devices, as they will only accept certificates from a trusted certification authority. Logon to you CA, open a Command prompt and run the following command:
certutil -ca.cert C:\root.cer
This command will export the root certificate to the C:> drive as root.cer. Note that you can use any other name for the file and store it in any other location, we’re just using this in our example.
NOTE If you are going to deploy SCEP certificates to Android devices, you will need to export the root certificate from both the root CA and the issuing CA (if it exists). For iOS devices, you only need to export the root certificate from the root CA.
Next, logon to your Intune portal and create a trusted certificate profile first. In my example I created a profile for iOS devices:
When you create your profile, you need to upload the root certificate that you just exported from the root CA and deploy the trusted certificate profile to your target devices. If you plan to deploy SCEP profiles to Android devices, and if you have both a root CA and an issuing CA, you need to create one trusted certificate profile for the root CA and another one for the issuing CA. For iOS devices, you only need to deploy the trusted certificate profile including the root certificate from the root CA.
Once the trusted certificate profile has been successfully deployed to your devices, you can now create the SCEP profile itself. In this example I will again create a sample profile for iOS devices:
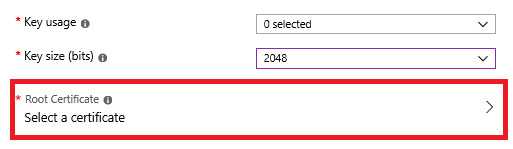
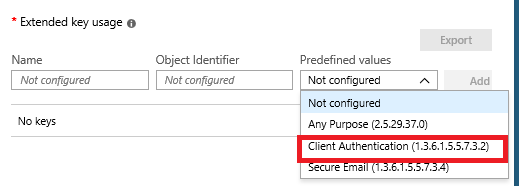
One important step is to define the key usage:
Do you still remember the certificate purpose registry keys we configured on the NDES server?
We need to map again the key usage from our SCEP profile to the registry keys we defined on the NDES server. If you select Digital signature in the SCEP profile, the Intune connector will read the value SignatureTemplate key and the NDES server will request the certificate based on the template name defined in the key value. If Key encipherment is selected, the connector will read the EncryptionTemplate key, and if both are selected in the SCEP profile the connector will read the GeneralPurposeTemplate key.
Select the trusted certificate profile we created earlier:
Define the key usage:
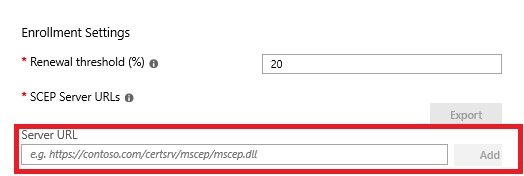
As a last step, specify the external FQDN of our NDES server in the SCEP profile:
The format needs to be as below:
https://<external FQDN of the NDES server>/certsrv/mscep/mscep.dll
In this example, we have previously generated the external FQDN with Azure Application Proxy:
Once you’re finished configuring your profile, all you need to do now is assign the SCEP profile to your target devices/users. Once the users/devices receive the profile, they will then retrieve a SCEP certificate. A brief overview of this process is shown below.
Additional Resources
Troubleshooting NDES configuration for use with Microsoft Intune certificate profiles
Troubleshooting SCEP certificate profile deployment in Microsoft Intune
Configure and use SCEP certificates with Intune
Mingzhe Li
Intune Support Escalation Engineer
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.