- Home
- Microsoft Intune and Configuration Manager
- Intune Customer Success
- Resolved: Known issue for FileVault configuration profiles on macOS devices
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Updated 12/19/19 - This is now resolved!
We’ve noticed an issue with a setting when configuring FileVault settings for macOS devices within Device Configuration. This may cause FileVault profiles to not deploy as intended depending on how the settings are configured. We’re sharing a workaround here until this is fixed in a future release.
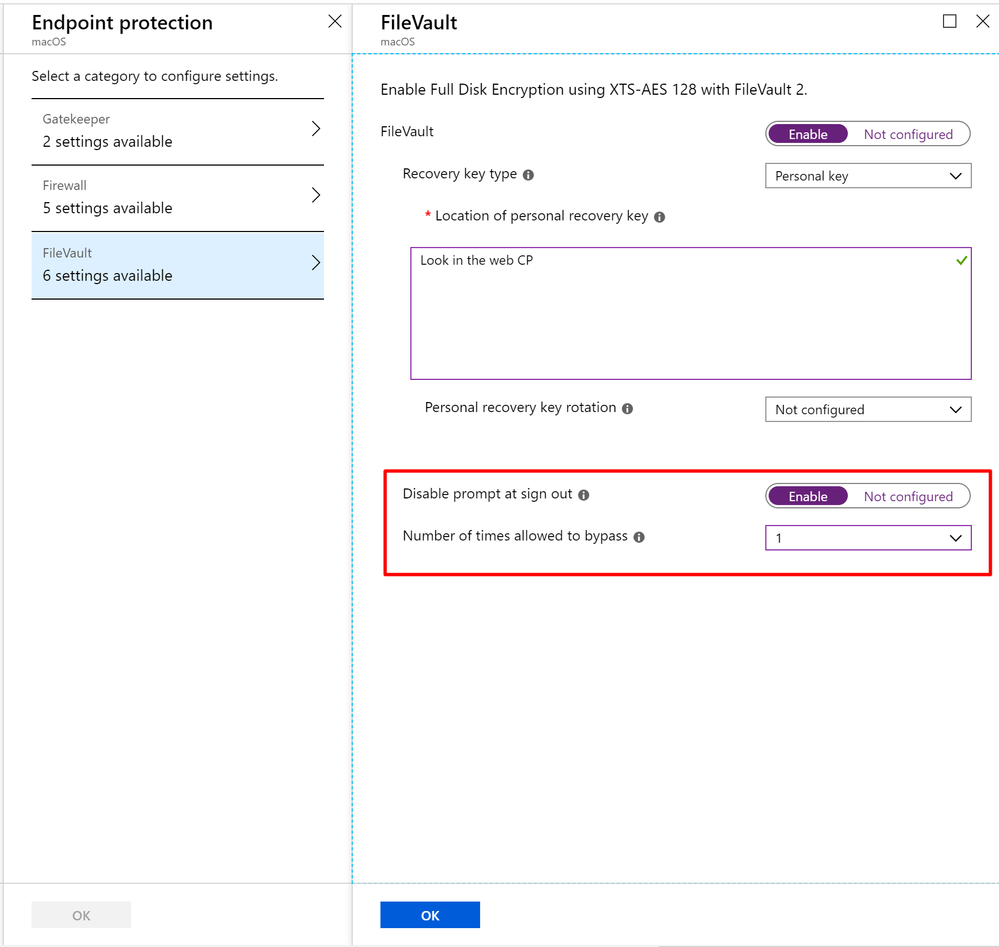
When Disable prompt at sign out is Not configured, the Number of times allowed to bypass can be set to any value. The screenshot below is a working scenario.
When Disable prompt at sign out is set to Enable, the Number of times allowed to bypass must be set to a value other than Not configured, as shown in the screenshot below.
The scenario below will not work because Disable prompt at sign out is enabled, and Number of times allowed to bypass is set to Not configured. The FileVault profile will not be deployed to devices and reporting will show an error.
We’ll update this post as this is fixed in the console in an upcoming release!
Blog post updates:
- 12/19/19 with an update that this is now resolved.