- Home
- ITOps Talk
- ITOps Talk Blog
- Step-By-Step: Enabling Custom Role Based Access Control in Azure
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Hello Folks,
During the preparation of the Ignite The Tour conference, @Neil Peterson and I along with the whole Cloud Ops Advocate team, were looking at issues that IT/Ops professionals are facing when looking at hybrid environments and migrating workloads to the cloud.
One of these issues is more than a technological problem to solve. It’s a business decision that can be supported by a set of tools available in azure. I’m talking about Governance. Governance refers to the ongoing process of managing, monitoring, and auditing the use of Azure resources to meet the goals and requirements of your organization.
Azure implements two primary governance tools, role based access control (RBAC), and resource policy, and it's up to each organization to design their governance model using them.
In this post we will cover RBAC. More specifically, custom RBAC, because built in roles may not always cover every situation so you can customize the RBAC so they are tailored to your specific needs. Here’s a quick video we recorded to cover that. The details are below.
So, To create custom RBAC roles you need to create a JSON file with the specific and granular access you want to grant or deny. Here is the JSON files Neil used in his demo.
{
"Name": "Restart Virtual Machines",
"IsCustom": true,
"Description": "Restart Virtual Machines.",
"Actions": [
"Microsoft.Compute/virtualMachines/read",
"Microsoft.Compute/virtualMachines/start/action",
"Microsoft.Compute/virtualMachines/restart/action",
"Microsoft.Resources/subscriptions/resourceGroups/read"
],
"NotActions": [
],
"DataActions": [
],
"NotDataActions": [
],
"AssignableScopes": [
"/subscriptions/d5b9d4b7-6fc1-46c5-bafe-38effaed19b2"
]
}
As you can see the file has 8 sections:
- Name --> that one is pretty evident
- IsCustom --> Boolean value telling the Azure Resouce manager if this is built in role or custom. When you create a custom role, it appears in the Azure portal with an orange resource icon.
- The next 4 sections dictate what rights that new custom role will inherit Action à what you’re allowed to do, NotActions --> what you’re not allowed to do. The next 2 are the same, but focused on data operation.
- The last section, the AssignableScopes --> the subscription IDs that this role will cover. As mentioned in the documentation, to create a custom role you MUST have either Owner or User Access Administrator roles yourself in the subscriptions listed.
Once you have the file, you need to use either PowerShell or Azure-CLI to create the new role in Azure using the JSON file you created. The Azure-CLI command documentation can be found here.
az role definition create --role-definition vm-restart.json
Once the role has been create you can use the following command to assign it to a group or user(s)
az role assignment create --role "Restart Virtual Machines" --assignee rebecca@nepeters.com
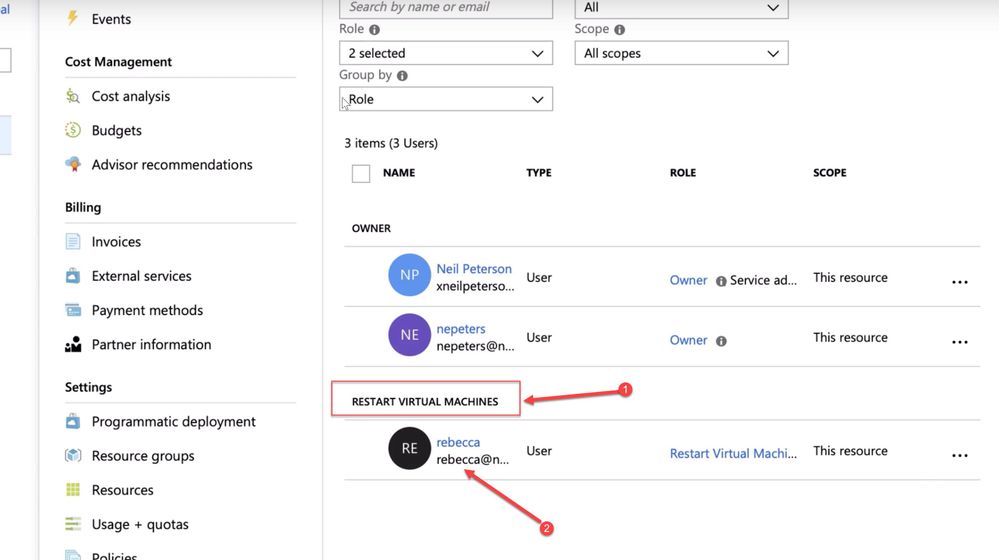
or assign it using the portal. As you can see bellow. We now have a new role (1) and it is assigned to the Rebecca user as per our last command.
Here you go. It's pretty simple to create your own roles. However, there needs to be significant thoughts around the entire governance issue.
For now. more information about RBAC for Azure resources and Custom roles for Azure resources can be found in our docs.
To view the list of operations, see the Azure Resource Manager resource provider operations.
I hope you found this helpful. let us know in the comments what topics you want us to cover.
Cheers!
Pierre
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.