- Home
- Exchange
- Exchange Conversations
- ATP not scanning Subject Line for Hyperlinks
ATP not scanning Subject Line for Hyperlinks
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 09 2018 03:28 AM
Hi
I recently reported an issue with the Office 365 ATP not scanning subject lines (or re-writing the URL).
I reported this to MSRC, and they acknowledged the report, however they responded that this was "By Design". This to me is a gaping security hole for a product that you assume protects the subject along with the body of the organisation's email.
Basically, I potentially could place a link to a malicious file/exploit framework in the subject of an email (even using link shortening, such as bit.ly) and this link / URL will be completely ignored by the paid for Advanced Threat Protection.
I have been successful in proving this both in Outlook 2013 and 2016 on Windows. It has also been tested on Outlook for Mac, where this appears to not be a problem as the link is not clickable I am seeing the same results in OWA.
This leads me to believe the issues is 2 fold, initially ATP is not scanning the Subject line, which wouldn't be a problem if the Outlook Client didn't make the potentially malicious URL clickable.
So to highlight and demonstrate, i did the following:
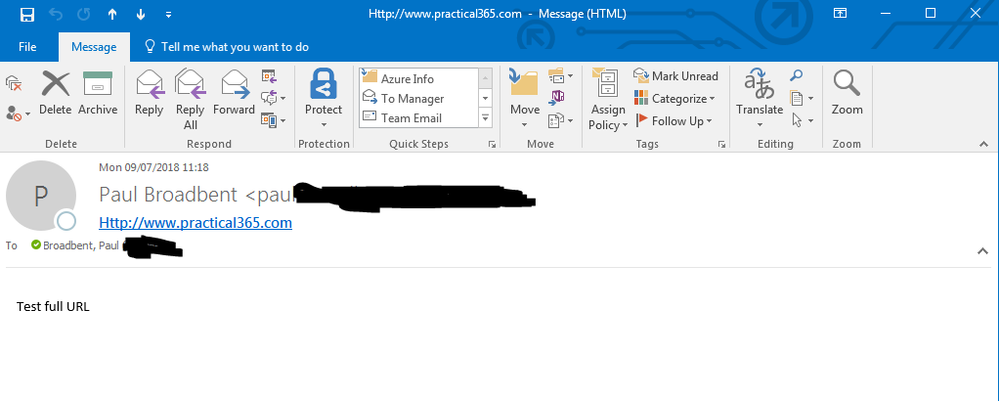
Went to http://bitly.com and shortened the URL http://www.practical365.com to give me: https://bit.ly/2KFzhZP
I logged into my personal Gmail account and created an email to send to my Work e-mail account (Office 365 E3 with EMS E5 and Office 365 ATP), here is what was delivered:
If i hover the cursor over the URL, it is NOT re-written and this is the case if i do not use a URL shortening tool also. Upon double clicking the URL, my web browser helpfully sprung to life and promptly displayed the www.practical365.com site.
Please let me know if you have this issue or have come across similar.
Thanks
Paul
- Labels:
-
Office365 ATP Outlook
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 09 2018 03:49 AM
It's possible that some other layer of protection in EOP would detect a malicious URL or some other characteristic of an actual attack, but I agree with you that ATP Safe Links should be looking at URLs in subject lines as well.
Since you already reported this to MSRC I've flagged this with the product group to see if there's anything more that can be done.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 09 2018 03:59 AM
Hi Paul,
I agree, there could be another layer of protection, but the lack of re-write in the URL makes me cautious.
I did want to try linking to a malicious payload, but unfortunately I am not in a position to do that in a production network.
If I get the time I may try this over the next week.
My concern is that people will buy ATP as an "Out of the box" security solution and just expect it will protect them from all incoming links.
Thank you for your advice and following this up.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 09 2018 04:45 AM
Well we expect Safe Links to rewrite URLs so they can be checked at the time of click. So that should be happening whether the URL is known (by us) to be safe or not.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jul 11 2018 02:01 PM
I am told by a member of the product group that they are aware of this issue and are actively working on it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 06 2018 01:23 AM
Is the clickable link scanned?
So when you reply to yourself and the link appears to be clickable, is it scanned then?
Have you tried with a proper malicious link?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Aug 06 2018 01:32 AM
Hi Mattias,
it appears the clickable link in the subject line is not scanned or re-directed to *.safelinks.protection.outlook.com at any point.
I have been unable to use a "real" malicious link. Although I suppose linking directly to eicar would be pretty safe.
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Oct 23 2018 07:08 AM
To me it looks like safelink gets bypassed a lot even if the link is in the content of the mail.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 15 2018 05:09 PM
Some domains are automatically bypassed based on Microsoft's own intel, last I checked.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 20 2018 06:41 PM
@Paul Cunningham miss your articles on practical365. Nice to see you responding threads..