- Home
- Microsoft Intune and Configuration Manager
- Microsoft Intune Blog
- Microsoft Intune announces support for macOS FileVault disk encryption management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
(This post is co-authored with Anya Novicheva, Program Manager, Microsoft 365)
Microsoft Intune is excited to announce support for FileVault full-disk encryption configuration on macOS devices. FileVault full-disk encryption (also known as FileVault 2) helps prevent unauthorized access to the information on macOS startup disks. With support for FileVault, Intune administrators can ensure startup disks are unreadable without the password on company managed devices, and they can recover personal keys on behalf of users on corporate devices from the Intune console. Device users can also securely recover their personal key at any time using Intune.
This release includes:
- Personal recovery key rotation to help protect against unauthorized access using compromised keys. Intune administrators can rotate the personal recovery keys for company-managed encrypted Macs, and they may also configure how often to rotate the personal key.
- Personal key escrow, providing a secure location for both end users and administrators to access the personal recovery key for company-managed encrypted Macs.
Get started
To set up FileVault on a managed macOS device that is not yet encrypted, the admin configures the FileVault settings located under the Endpoint Protection profile type within Device Configuration navigation of the Microsoft Intune administration console.
On the same settings page, the admin may enter a message to help the end user in case they forget their password and need to locate the recovery key. For example, they may provide information such as the location of the personal recovery key. This message is shown to end users on the login screen where they enter the personal recovery key instead of a password.
Key recovery
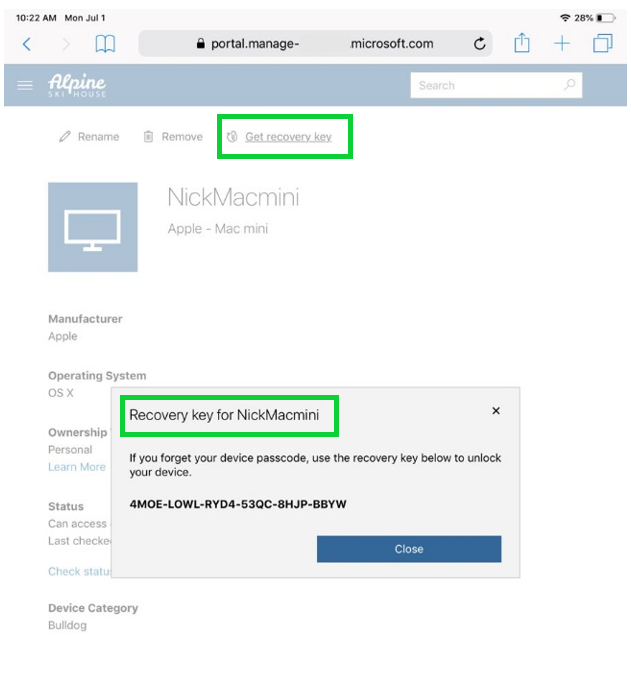
The end user may use the Microsoft Intune Company Portal website on any device to access their personal recovery key. Once they login to the web Company Portal, they can select their FileVault enabled macOS device from the device thumbnails, and click on Get recovery key. If the macOS device isn’t encrypted or it was encrypted prior to enrollment, they will not see a personal recovery key.
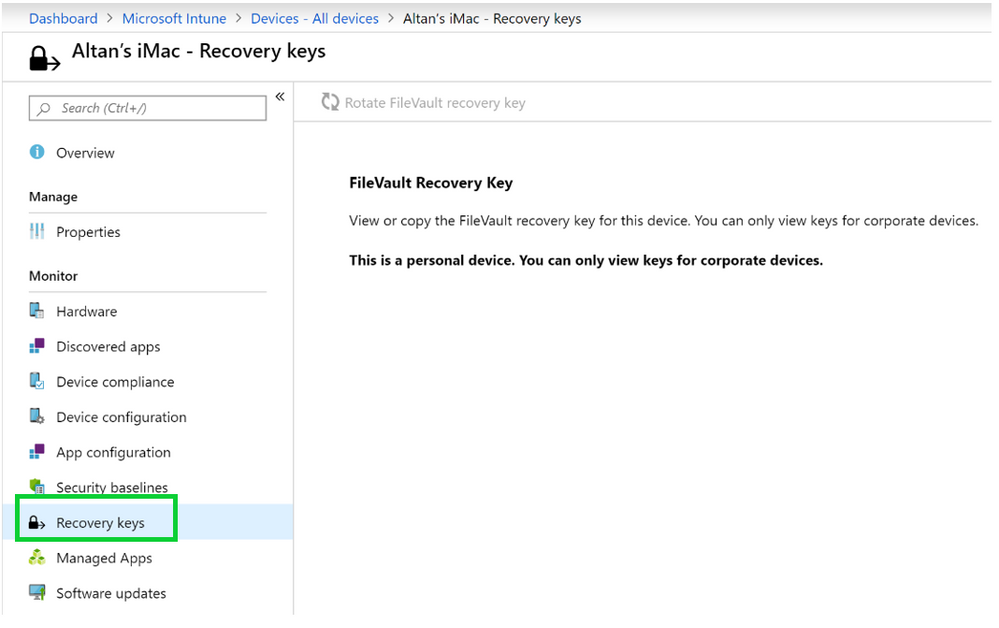
To help protect a device that might have had its key compromised or to prevent other types of security incidents, the Intune admin may perform a remote device action to rotate the personal recovery key on a corporate macOS device. This is as simple as selecting the macOS device in the Intune console, and going to Recovery Keys > and then choosing to rotate the device’s personal recovery key.
If the device is not enrolled or not encrypted, Intune doesn’t have a key for that device and the action is grayed out (as in the screenshot below).
Reporting
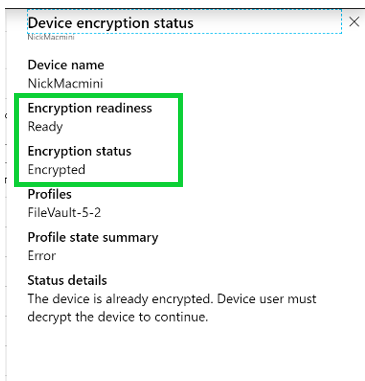
Encryption Reporting is a powerful tool for security management across all devices in the modern workplace. The Intune admin can see reporting for all of their macOS devices from Devices > all devices > macOS device > Encryption Reporting. This report shows whether devices are ready to be encrypted or not, whether they were encrypted prior to being enrolled, and whether there are any errors during the encryption process. Intune admins can report on the disk encryption for Windows BitLocker and macOS FileVault from a single dashboard. Admins may also export the entire report to an Excel file where they can filter by OS type, encryption readiness, or status.
Next steps
This feature is the latest in a series of innovations to simplify macOS management with Intune. This is a journey and we expect to add significant enhancements in future, based on your feedback and customer priorities. Administrators using Microsoft Intune can secure their entire workplace from a single place – not only Apple FileVault encryption but also mobile device encryption and Windows BitLocker.
Microsoft offers a variety of resources and support tools to help you in this journey. Plan your macOS management and deployment with online guides and tools from FastTrack, a service that’s included in your eligible Microsoft subscription at no additional cost. FastTrack provides customized guidance for onboarding and adoption, including access to Microsoft engineering expertise, best practices, tools, and resources so you can leverage existing resources instead of creating new ones.
More info and feedback
Learn how to get started with Microsoft Intune with our detailed technical documentation. Don’t have Microsoft Intune? Start a free trial or buy a subscription today!
As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our Tech Community page.
Follow @MSIntune on Twitter
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.