- Home
- Security, Compliance, and Identity
- Microsoft Sentinel Blog
- Ingest Office 365 DLP Events into Azure Sentinel
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Having different use cases for SIEM is very interesting, and it is incredible to work with customers and partners on them. In one of my engagements, a customer asked about the possibility of ingesting Office 365 DLP into Azure Sentinel.
Before I dig into details, lets me explain where one can get Office 365 DLP events apart from Azure Sentinel.
- In Security and Compliance Center - link
- Available via PowerShell cmdlets - link
- Office 365 Activity API schema includes DLP events as well - link
This blog post describes a step by step guide on how to ingest Office 365 DLP events into Azure Sentinel, and how to use it.
Preparation
The following tasks describe the needed preparation steps:
- Create Office 365 DLP rules - link. For my use case, I created a default template rule called "U.S. Finance Data".
- For this blog, I assume that an Azure Sentinel instance is available and is used. If not, use this link to onboard Azure Sentinel first.
- One of the advantages of Azure Sentinel is the availability of out of the box Data Connectors for Microsoft services as well as for 3rd Party vendors. Enable two connectors from the Microsoft ecosystem:
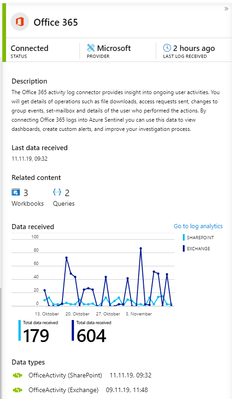
- Make sure that these connectors are healthy and events are ingested, as follow a sample status for the Office 365 data connector.
Simulation and validation
Ones the DLP policies are configured and assigned to the users, and the required connectors are enabled, the simulation can be started to produce events for later usage.
How to search for events
Office 365 DLP has three types of events that are ingested into Log Analytics workspace and are available for search.
- DlpRuleMatch - This indicates a rule was matched. These events exist in both Exchange and SharePoint Online and OneDrive for Business. For Exchange, it includes false positives and overrides information. For SharePoint Online and OneDrive for Business, false positives and overrides generate separate events.
- DlpRuleUndo - These only exist in SharePoint Online and OneDrive for Business. They indicate a previously applied policy action has been "undone" – either because of false-positive/override designation by the user or because the document is no longer subject to policy, due to policy change or change in the document content.
- DlpInfo - These only exist in SharePoint Online and OneDrive for Business and indicate a false positive designation, but no action was "undone."
In my example, I looked for DLP events in SharePoint Online, and the "DLPRuleMatch" type.
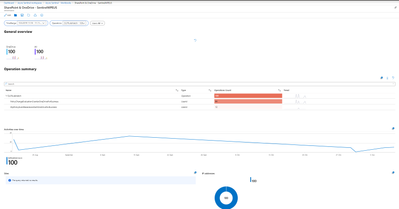
Workbook for interactive reports
Azure Sentinel can use the ingested data with out of the box dashboards as well as for customized dashboards. For my purpose, I used the SharePoint & OneDrive dashboard, which is available as part of the Office 365 data connector. For Office 365, Azure Sentinel has two additional dashboards: "Office 365" and "Exchange Online".
To view the events, just open the SharePoint and OneDrive workbook and search for DLPRuleMatch events.
Summary
Azure Sentinel is limitless and can cover many use cases, for example, the one shown in this blog post.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.