- Home
- Security, Compliance, and Identity
- Microsoft Defender for Cloud Blog
- Azure Security Center & automatic creation of an incident in ServiceNow
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In my previous blogpost I talked about how to create a Logic Apps playbook which creates a ticket in ServiceNow. In this blogpost we will look at how to automatically create a ticket in ServiceNow when a Security Center alert is raised.
Note: Automatic triggers for Logic App with Azure Security Center will be released in the future
Now that you can create a ServiceNow record by selecting and starting the playbook in Azure Security Center, you are going to explore how to automate this end-to-end. The benefit of this approach is that there’s no human action necessary to run the playbook. If Azure Security Center generates an alert, a record will be created automatically. For this to work you are going to leverage the following:
- A classic Azure alert, which is part of Azure Monitor
- An Action Group which serves as what to do if an alert is raised, in this case start the playbook automatically for you
- A second playbook which will be started by the Action Group
To avoid duplicate records being created based on the same Azure Security Center alertID, you are going to add a custom field in ServiceNow which will be populated with the Azure Security Center alertID. Leveraging this field, we can validate if a new record should be created.
Please refer to the ServiceNow documentation for more information about how to add a custom field.
- Open an existing incident in ServiceNow and right click in the top for the form
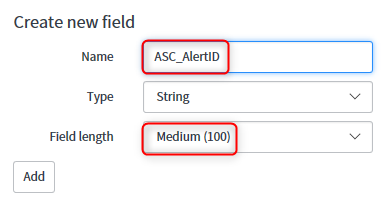
- Select Configure, Form Layout and under Create new field enter ASC_AlertID as the Name and select Medium (100) as the Field length. Click on Add and then Save the new field.
3. Navigate to the Azure Security Center portal and under Automation and Orchestration, select Playbooks
4. Click on Add Playbook
5. Provide a name for your new playbook like “ASC-Automatic-Ticket-To-ServiceNow” and fill in the resource group and location fields. The Log Analytics integration offers capabilities like using search to query the status and history of your playbooks. Click on Create
6. In the Logic Apps Designer select the Blank Logic App template
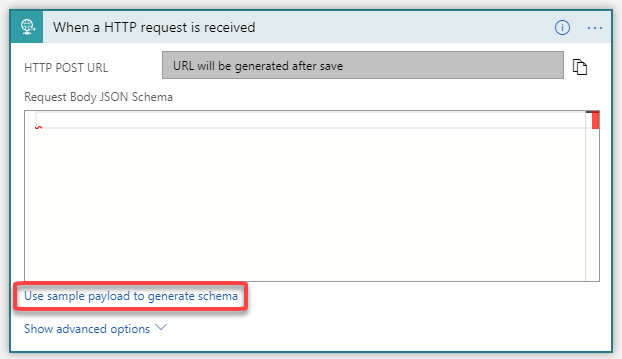
7. Select When a HTTP request is received as the trigger
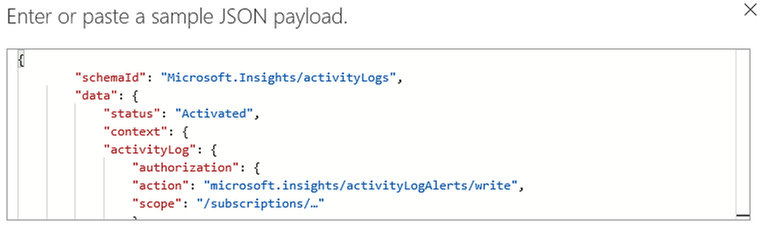
8. In the Request Body JSON Schema box you need to add the Azure Monitor schema which can be found here. Refer to step 8 in the article and copy the Azure Monitor JSON schema
9. Click on the Use sample payload to generate schema link
10. Paste in the JSON schema you just have copied
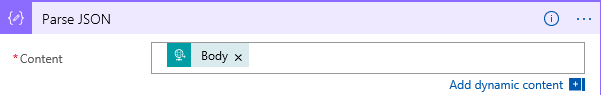
11. Since Azure Monitor provides you with a JSON formatted input, you need to parse it so that you can use it in a more structured way for our purpose. Click on + New Step and search for parse json and select it
12. Select the Body as Content
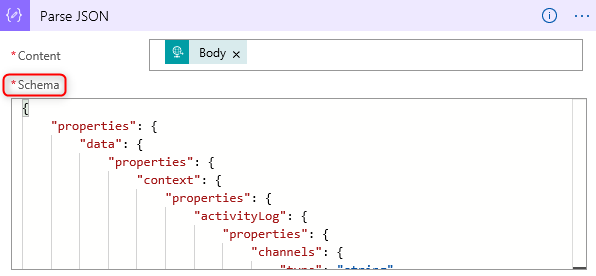
13. For efficiently using the Azure Security Center alert information, you need to provide a schema.
14. Navigate to this link and copy the Azure Security Center alert schema
15. Paste the copied schema into the Schema body
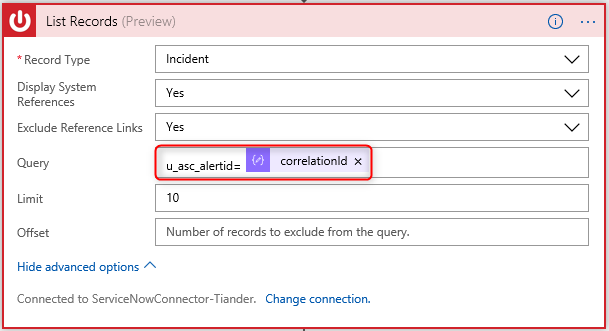
16. Now you are going to add a new step which will check if a record already has been created based on the Azure Security Center alertID. If not, we will create a new record. Click on + New Step, search for ServiceNow and add a List Records step
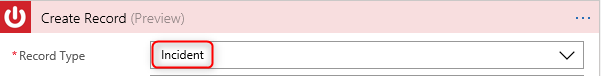
17. Select Incident as the Record Type
18. Under Query add u_asc_alertid= and the correlationId field from the previous step. Fill in the other fields as shown below. Your List Records configuration should look like this:
19. To check the existence of a ServicNow record based on the Azure Security Center alertID, you are going to add a Condition as a new step. Leverage the Expression field to validate if a record has been returned by entering this expression: empty(body('List_Records')['result'])
20. Enter true in the field next to is equal to. Your Condition configuration should look like this:
21. If your statement is “true”, then no records have been found with the same Azure Security Center alertID and we need to create a new record
22. Within the If true block, click on + New Step and search for ServiceNow
23. Select Create Record as the action
Note: Since we have already created a connection previously, we are going to re-use that connection. Logic Apps automatically selects that connection for you
24. Select Incident as your Record Type:
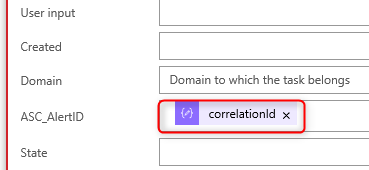
25. Now add the Azure Security Center alertID field by adding correlationId in the ASC_AlertID field of the ServiceNow incident properties. This value comes from the Parse JSON step and should look like this:
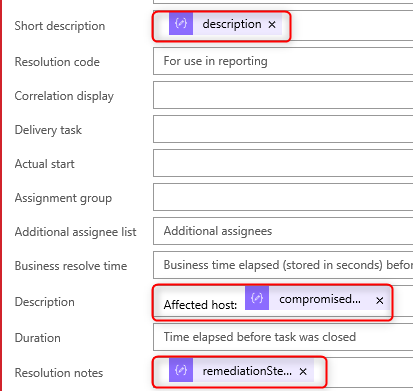
26. Add values to the remaining fields like Short description, Description and Resolution notes:
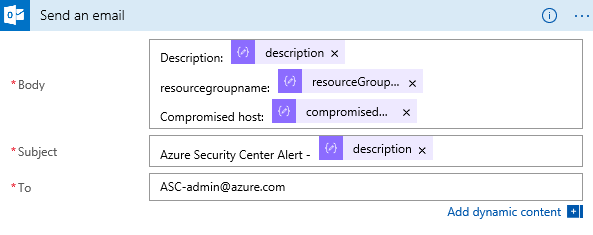
27. Add any additional steps like Send an email:
28. Save the playbook
Creating an Action Group
For invoking a Logic Apps playbook automatically based on an Azure Security Center alert being generated, you are going to leverage Azure Action Groups in Azure Monitor.
- Navigate to the Azure portal and click on Azure Monitor
- Under Settings, click on Action Groups and click on Add action group
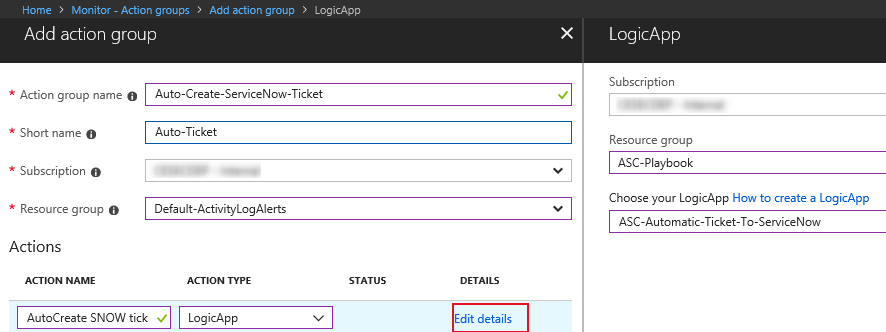
3. Give you new action group a name like “ASC-Alert-ActionGroup” and fill in the remaining required fields
4. Under Actions, provide an Action Name and under Action Type, select your “ASC-Automatic-Ticket-To-ServiceNow” Logic Apps playbook and click on OK to save it
Creating an Azure Classic Alert
- Navigate to Azure Monitor -> Alerts (classic) -> Add activity log alert
- Under Event Category, select Security
- Under Operation name, select Activate Alert (locations/alerts)
- Under Alert via make sure to select the action group we have created earlier:
5. Save the alert
Test driving the playbook
Every Security Operations Center (SOC) wants to ensure that that any automation, specifically creating tickets based on security alerts, works as expected. To test if your playbook automatically starts when an alert is generated, you need an Azure Security Center alert. One option to safely generate an Azure Security Center test alerts is described here.
Verify that you have a new alert in Azure Security Center, like the one below:
Switch over to ServiceNow and you can see that an automatic alert has been generated:

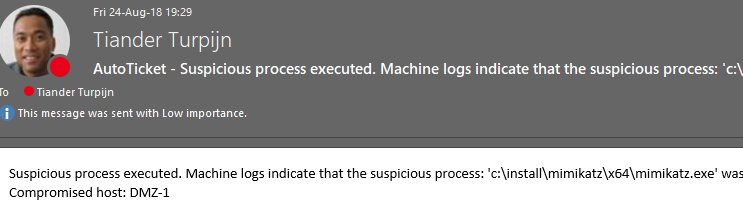
In case you have configured an email notification step, you should receive an email like the example :
Start automating Security Center actions with playbooks and ServiceNow today. For more information on Azure Security Center, playbooks, and ServiceNow, visit our documentation below.
Azure Security Center documentation
Azure Security Center playbooks
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.