Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Azure
- Azure PaaS Blog
- Azure Storage Role Based Access Control : Revoking Delete Access using RoleDefinition via Powershell
Azure Storage Role Based Access Control : Revoking Delete Access using RoleDefinition via Powershell
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Jul 24 2019 06:39 AM
3,679
Views
Jul 24 2019
06:39 AM
Jul 24 2019
06:39 AM
Scenario :
The end-user should not be able to delete the data but can execute other data operations like create/update etc. in the storage account.
Pre-Requisites :
- The admin must have adequate access under the tenant i.e. privileges to create a custom AD Role. Refer to this article
- The user must be admin/contributor to the said storage account so that he can grant the access.
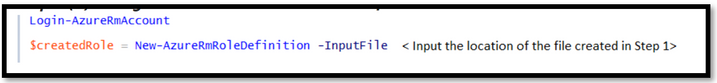
Step 1: Creation of a custom Azure Active Directory Role :
The JSON file of the Azure AD Role is as follows :
Using PowerShell to create a Role Definition
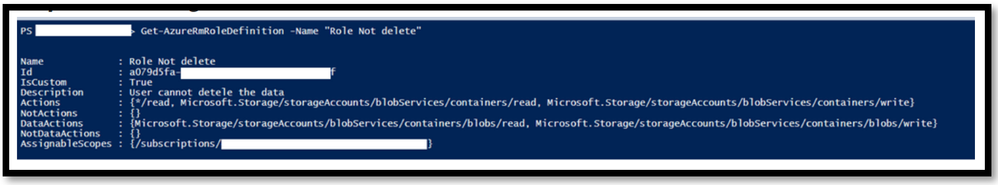
Step 2: Retrieving the created Role :
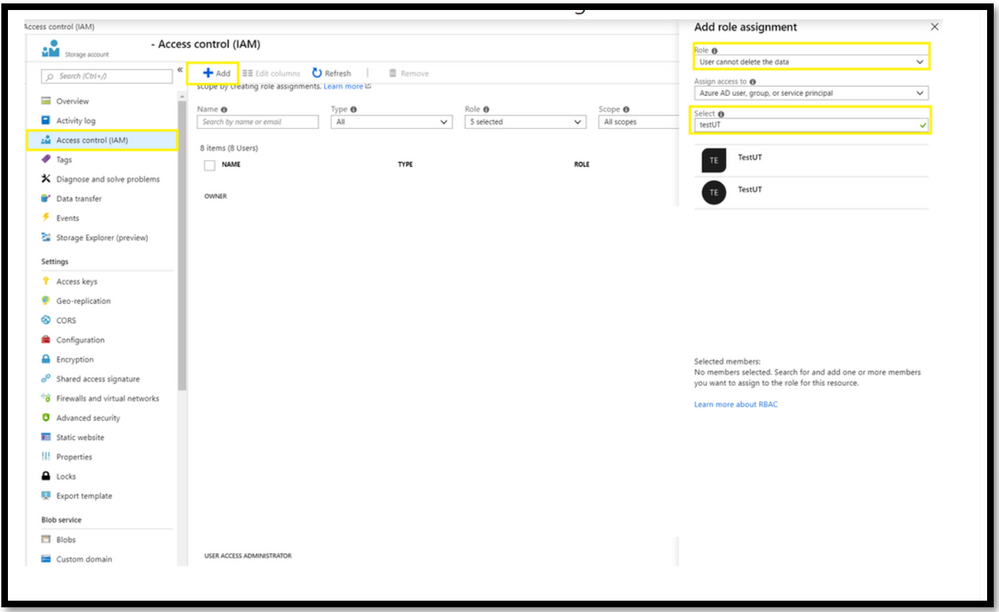
Step 3: Assignment of the Role :
- Log in to the Azure Portal -> The Storage Account -> Access Control (IAM)
- Provide the required type of security principal.
- Search for the user to whom the access should be assigned.
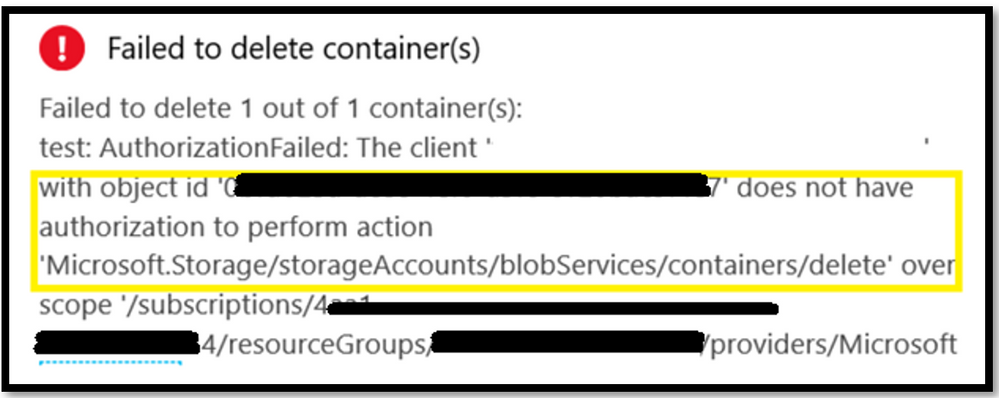
- Now when the said user, tries to execute a delete operation, he will observe an error
Hope this helps.
0
Likes
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
Labels