- Home
- Security, Compliance, and Identity
- Microsoft Defender for Identity
- New preview detection: Data exfiltration over SMB
New preview detection: Data exfiltration over SMB
- Subscribe to RSS Feed
- Mark Discussion as New
- Mark Discussion as Read
- Pin this Discussion for Current User
- Bookmark
- Subscribe
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Jan 16 2019 01:39 AM
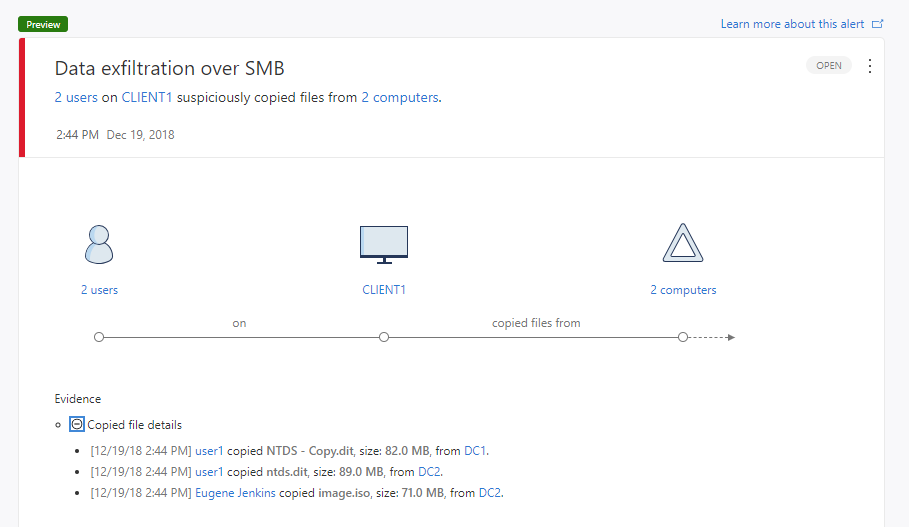
Domain controllers hold the most sensitive organizational data. For most attackers one of their top priorities is to gain access to the domain controllers and steal your most sensitive data. For example exfiltration of the Ntds.dit file, stored on the DC, allows an attacker to forge Kerberos ticket granting tickets(TGT) that provide authorization to any resource, and set the ticket expiration to any arbitrary time. An Azure ATP alert is triggered when suspicious transfers of data over SMB are observed from domain controllers.
Starting from Version 2.61, Azure ATP detects attempts at Data exfiltration over SMB and issue a security alert like the one shown below.
For more information visit https://aka.ms/atasaguide-smbexfiltration
Stay tuned for additional alerts and updates. Your feedback is welcome!