Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Suspend MFA on a Remembered Device now in Preview!
Suspend MFA on a Remembered Device now in Preview!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 06 2018 07:32 PM
7,402
Views
Sep 06 2018
07:32 PM
Sep 06 2018
07:32 PM
First published on CloudBlogs on Aug, 20 2014
Howdy folks, Today I have the pleasure of announcing the public preview of our new "Suspend MFA on Remembered Devices" feature. Using this preview administrators can now opt to allow users to suspend the need for additional two factor authentications when using a remembered device. When the admin enables this feature, end-users can choose to have Azure AD remember the device and browser they are signing in from when completing a successful Multi-Factor Authentication. The MFA suspension lasts between 1 to 60 days based on administrator configuration. The feature is available for all flavors of Azure Multi-Factor Authentication including Multi-Factor Authentication for Office 365 and Multi-Factor Authentication for Azure Admins. This is one of our most highly requested features as it simplifies the end-user login experience while maintaining a high level of security assurance. To help you get started with this feature, I've asked Shawn Bishop a PM in our MFA team to walk you through the administrator setup and the user experience. Shawn joined us from PhoneFactor where he played a critical role helping hundreds of customer to successfully deploy the PhoneFactor hybrid MFA solution. We hope you'll find this feature useful and as always, we're looking forward to your suggestions and feedback. (Note: If you look closely you might notice that we've been trying out a new approach to the screen shots we post in the blog to see if we can make them easier to read. Nima Hashemi, one of the PM's on the team has been driving this. Let us know what you think of his new approach) Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of PM Active Directory Team Under the
multi-factor authentication
section, click on the
Manage service settings
link to access the Multi-Factor Authentication service settings.
Under the
multi-factor authentication
section, click on the
Manage service settings
link to access the Multi-Factor Authentication service settings.
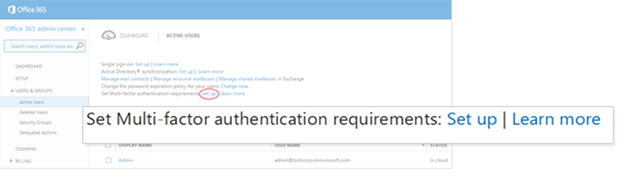
 Alternatively, Office 365 administrators can access the Multi-Factor Authentication service settings page from the Office 365 admin center. From the admin center, go into
Users & Groups
, select
Active Users
in the left navigation and then click the
Set up
link next to the "Set Multi-factor authentication requirements" option.
Alternatively, Office 365 administrators can access the Multi-Factor Authentication service settings page from the Office 365 admin center. From the admin center, go into
Users & Groups
, select
Active Users
in the left navigation and then click the
Set up
link next to the "Set Multi-factor authentication requirements" option.
 Clicking the
Set up
link will take you to the
users
tab of the Multi-Factor Authentication settings pages. Click the
service settings
tab at the top.
Clicking the
Set up
link will take you to the
users
tab of the Multi-Factor Authentication settings pages. Click the
service settings
tab at the top.
 On the Multi-Factor Authentication
service settings
page, you will see the new
manage user devices
section at the bottom of the page.
On the Multi-Factor Authentication
service settings
page, you will see the new
manage user devices
section at the bottom of the page.
 To enable the feature, check the checkbox and configure the number of days the suspension cookie will last until users must re-authenticate using Multi-Factor Authentication. The number of days can range between 1 and 60. Click the
save
button. It will show an "Updates successful" message if the changes are successfully saved.
To enable the feature, check the checkbox and configure the number of days the suspension cookie will last until users must re-authenticate using Multi-Factor Authentication. The number of days can range between 1 and 60. Click the
save
button. It will show an "Updates successful" message if the changes are successfully saved.
 Your organization is all set to benefit by enjoying the security of Multi-Factor Authentication without too much inconvenience for your users. If the feature is later disabled, users once again will be required to perform Multi-Factor Authentication on every sign-in, even if signing in from devices that were previously remembered (i.e. still have an unexpired cookie).
Once the feature is enabled and users have started using it, there may be a situation that requires Multi-Factor Authentication to be restored for a particular user. The administrator can accomplish this by going to the
users
tab in the Multi-Factor Authentication settings pages. The administrator should select the user and click
Manage user settings
in the right column.
Your organization is all set to benefit by enjoying the security of Multi-Factor Authentication without too much inconvenience for your users. If the feature is later disabled, users once again will be required to perform Multi-Factor Authentication on every sign-in, even if signing in from devices that were previously remembered (i.e. still have an unexpired cookie).
Once the feature is enabled and users have started using it, there may be a situation that requires Multi-Factor Authentication to be restored for a particular user. The administrator can accomplish this by going to the
users
tab in the Multi-Factor Authentication settings pages. The administrator should select the user and click
Manage user settings
in the right column.
 In the
Manage user settings
box that appears, check the checkbox next to "Restore Multi-Factor Authentication on all suspended devices" and click
save
.
In the
Manage user settings
box that appears, check the checkbox next to "Restore Multi-Factor Authentication on all suspended devices" and click
save
.
 When the save completes, the "Updates successful" message will appear.
When the save completes, the "Updates successful" message will appear.
 End-User Experience
Once the Suspend Multi-Factor Authentication on Remembered Devices feature is enabled, users who are required to perform strong authentication will see the "Don't ask again for X days" option after entering their username and password. The number of days displayed is based on what the administrator configured.
End-User Experience
Once the Suspend Multi-Factor Authentication on Remembered Devices feature is enabled, users who are required to perform strong authentication will see the "Don't ask again for X days" option after entering their username and password. The number of days displayed is based on what the administrator configured.
 If the user successfully completes the Multi-Factor Authentication, a cookie is set on their device and they won't be required to perform Multi-Factor Authentication on that device and browser again until the cookie expires. Once the cookie has expired, the user must perform Multi-Factor Authentication again.
Users can restore Multi-Factor Authentication on their remembered devices by going to the additional security verification settings within their user profile. A shortcut to go there directly is at
https://aka.ms/mfasetup
where you can click the
Additional security verification
tile.
If the user successfully completes the Multi-Factor Authentication, a cookie is set on their device and they won't be required to perform Multi-Factor Authentication on that device and browser again until the cookie expires. Once the cookie has expired, the user must perform Multi-Factor Authentication again.
Users can restore Multi-Factor Authentication on their remembered devices by going to the additional security verification settings within their user profile. A shortcut to go there directly is at
https://aka.ms/mfasetup
where you can click the
Additional security verification
tile.
 On the
additional security verification
tab, users can click the
restore
button in the
manage multi-factor authentication for your devices
section.
On the
additional security verification
tab, users can click the
restore
button in the
manage multi-factor authentication for your devices
section.
 After clicking the
restore
button, users will see the "Updates successful" message. Afterwards, users will be required to perform Multi-Factor Authentication again, even if signing in from devices that were previously remembered.
After clicking the
restore
button, users will see the "Updates successful" message. Afterwards, users will be required to perform Multi-Factor Authentication again, even if signing in from devices that were previously remembered.

Howdy folks, Today I have the pleasure of announcing the public preview of our new "Suspend MFA on Remembered Devices" feature. Using this preview administrators can now opt to allow users to suspend the need for additional two factor authentications when using a remembered device. When the admin enables this feature, end-users can choose to have Azure AD remember the device and browser they are signing in from when completing a successful Multi-Factor Authentication. The MFA suspension lasts between 1 to 60 days based on administrator configuration. The feature is available for all flavors of Azure Multi-Factor Authentication including Multi-Factor Authentication for Office 365 and Multi-Factor Authentication for Azure Admins. This is one of our most highly requested features as it simplifies the end-user login experience while maintaining a high level of security assurance. To help you get started with this feature, I've asked Shawn Bishop a PM in our MFA team to walk you through the administrator setup and the user experience. Shawn joined us from PhoneFactor where he played a critical role helping hundreds of customer to successfully deploy the PhoneFactor hybrid MFA solution. We hope you'll find this feature useful and as always, we're looking forward to your suggestions and feedback. (Note: If you look closely you might notice that we've been trying out a new approach to the screen shots we post in the blog to see if we can make them easier to read. Nima Hashemi, one of the PM's on the team has been driving this. Let us know what you think of his new approach) Best Regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of PM Active Directory Team
------------------------
Greetings everyone! I'm Shawn Bishop, one of the PM's on Azure MFA here in the AD team. Today I'd like to walk you through the preview of the administrator and the end-user experience for our new Suspend Multi-Factor Authentication on Remembered Devices feature. Admin Experience To enable the preview, you will need to sign in to the Azure Management Portal as an administrator and select the Active Directory that you'd like to enable the feature for. On the directory you have selected, click the configure tab. Under the
multi-factor authentication
section, click on the
Manage service settings
link to access the Multi-Factor Authentication service settings.
Under the
multi-factor authentication
section, click on the
Manage service settings
link to access the Multi-Factor Authentication service settings.
 Alternatively, Office 365 administrators can access the Multi-Factor Authentication service settings page from the Office 365 admin center. From the admin center, go into
Users & Groups
, select
Active Users
in the left navigation and then click the
Set up
link next to the "Set Multi-factor authentication requirements" option.
Alternatively, Office 365 administrators can access the Multi-Factor Authentication service settings page from the Office 365 admin center. From the admin center, go into
Users & Groups
, select
Active Users
in the left navigation and then click the
Set up
link next to the "Set Multi-factor authentication requirements" option.
 Clicking the
Set up
link will take you to the
users
tab of the Multi-Factor Authentication settings pages. Click the
service settings
tab at the top.
Clicking the
Set up
link will take you to the
users
tab of the Multi-Factor Authentication settings pages. Click the
service settings
tab at the top.
 On the Multi-Factor Authentication
service settings
page, you will see the new
manage user devices
section at the bottom of the page.
On the Multi-Factor Authentication
service settings
page, you will see the new
manage user devices
section at the bottom of the page.
 To enable the feature, check the checkbox and configure the number of days the suspension cookie will last until users must re-authenticate using Multi-Factor Authentication. The number of days can range between 1 and 60. Click the
save
button. It will show an "Updates successful" message if the changes are successfully saved.
To enable the feature, check the checkbox and configure the number of days the suspension cookie will last until users must re-authenticate using Multi-Factor Authentication. The number of days can range between 1 and 60. Click the
save
button. It will show an "Updates successful" message if the changes are successfully saved.
 Your organization is all set to benefit by enjoying the security of Multi-Factor Authentication without too much inconvenience for your users. If the feature is later disabled, users once again will be required to perform Multi-Factor Authentication on every sign-in, even if signing in from devices that were previously remembered (i.e. still have an unexpired cookie).
Once the feature is enabled and users have started using it, there may be a situation that requires Multi-Factor Authentication to be restored for a particular user. The administrator can accomplish this by going to the
users
tab in the Multi-Factor Authentication settings pages. The administrator should select the user and click
Manage user settings
in the right column.
Your organization is all set to benefit by enjoying the security of Multi-Factor Authentication without too much inconvenience for your users. If the feature is later disabled, users once again will be required to perform Multi-Factor Authentication on every sign-in, even if signing in from devices that were previously remembered (i.e. still have an unexpired cookie).
Once the feature is enabled and users have started using it, there may be a situation that requires Multi-Factor Authentication to be restored for a particular user. The administrator can accomplish this by going to the
users
tab in the Multi-Factor Authentication settings pages. The administrator should select the user and click
Manage user settings
in the right column.
 In the
Manage user settings
box that appears, check the checkbox next to "Restore Multi-Factor Authentication on all suspended devices" and click
save
.
In the
Manage user settings
box that appears, check the checkbox next to "Restore Multi-Factor Authentication on all suspended devices" and click
save
.
 When the save completes, the "Updates successful" message will appear.
When the save completes, the "Updates successful" message will appear.
 End-User Experience
Once the Suspend Multi-Factor Authentication on Remembered Devices feature is enabled, users who are required to perform strong authentication will see the "Don't ask again for X days" option after entering their username and password. The number of days displayed is based on what the administrator configured.
End-User Experience
Once the Suspend Multi-Factor Authentication on Remembered Devices feature is enabled, users who are required to perform strong authentication will see the "Don't ask again for X days" option after entering their username and password. The number of days displayed is based on what the administrator configured.
 If the user successfully completes the Multi-Factor Authentication, a cookie is set on their device and they won't be required to perform Multi-Factor Authentication on that device and browser again until the cookie expires. Once the cookie has expired, the user must perform Multi-Factor Authentication again.
Users can restore Multi-Factor Authentication on their remembered devices by going to the additional security verification settings within their user profile. A shortcut to go there directly is at
https://aka.ms/mfasetup
where you can click the
Additional security verification
tile.
If the user successfully completes the Multi-Factor Authentication, a cookie is set on their device and they won't be required to perform Multi-Factor Authentication on that device and browser again until the cookie expires. Once the cookie has expired, the user must perform Multi-Factor Authentication again.
Users can restore Multi-Factor Authentication on their remembered devices by going to the additional security verification settings within their user profile. A shortcut to go there directly is at
https://aka.ms/mfasetup
where you can click the
Additional security verification
tile.
 On the
additional security verification
tab, users can click the
restore
button in the
manage multi-factor authentication for your devices
section.
On the
additional security verification
tab, users can click the
restore
button in the
manage multi-factor authentication for your devices
section.
 After clicking the
restore
button, users will see the "Updates successful" message. Afterwards, users will be required to perform Multi-Factor Authentication again, even if signing in from devices that were previously remembered.
After clicking the
restore
button, users will see the "Updates successful" message. Afterwards, users will be required to perform Multi-Factor Authentication again, even if signing in from devices that were previously remembered.

What next?
We hope the ability to suspend Multi-Factor Authentication on remembered devices prompts more organizations to adopt Multi-Factor Authentication to provide a higher level of security without adding a lot of inconvenience to end users. More documentation on this feature for administrators and users can be found on MSDN. If you have any feedback on the Multi-Factor Authentication suspension functionality or have other Multi-Factor Authentication scenarios that you have been wanting to see, tell us about them by posting in our forum on TechNet. Thanks Shawn
4 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.