- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Move even more apps to Azure AD: Public preview of group claims!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
I’m excited to announce the public preview of group claims in SAML and OIDC/OAuth tokens issued by Azure Active Directory (Azure AD). This feature is designed to allow you to move applications from Active Directory Federation Services (AD FS) or another identity provider to Azure AD.
Some applications expect to receive a user’s group membership information as claims in the token. When using groups from Windows Active Directory Domain Services, these claims typically use the group’s sAMAccountName from the on-premises Active Directory or the group’s on-premises group security identifier (SID). These attributes were used to support applications and clients in previous versions of Windows and are still in use today. By configuring Azure AD to emit the same group details in claims as the application previously received, you can move the application to work directly with Azure AD and take advantage of the identity-based security capabilities that Azure AD offers.
As part of this release, group claim configuration is now part of the Enterprise Applications single sign-on (SSO) configuration in the Azure portal for SAML applications. This allows you to easily configure options for the format of these claims and to customize the SAML attribute names for group data.
To configure an application to receive group claims from on-premises groups:
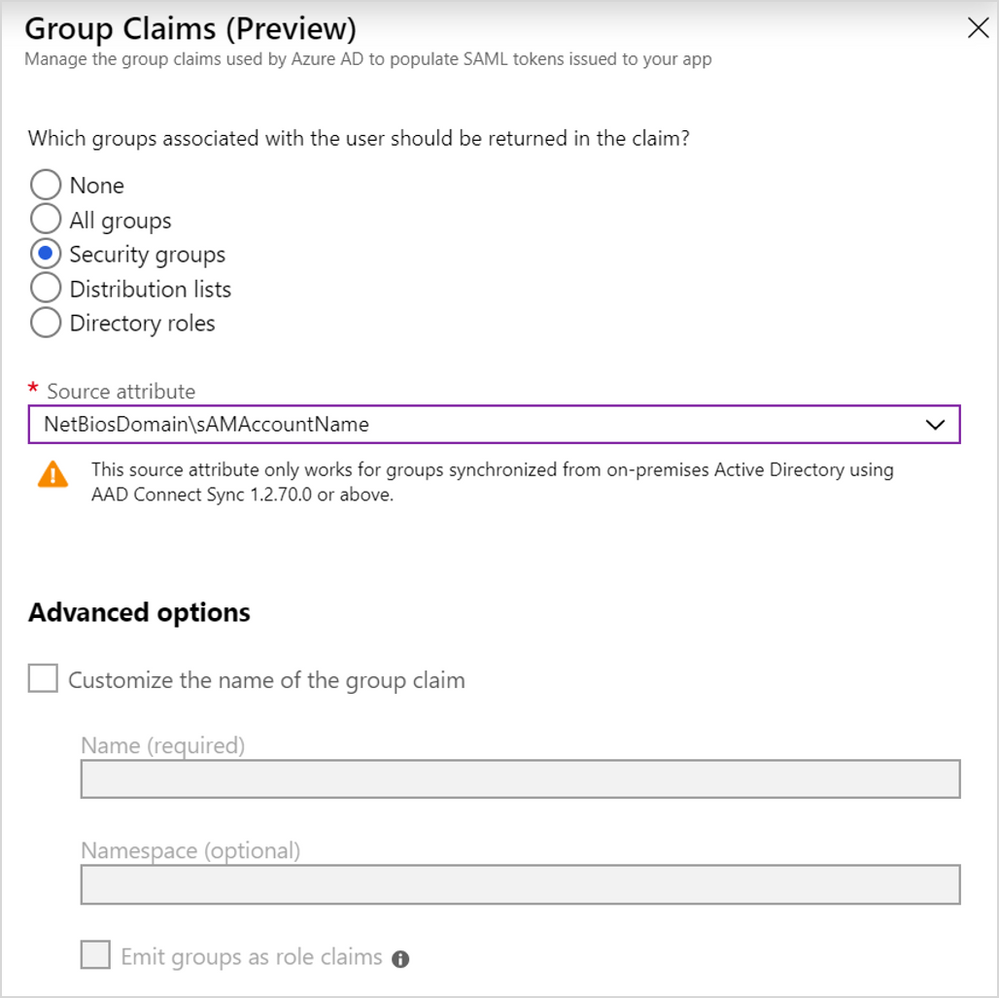
- If you want to use on-premises group names or SIDs, be sure you are running the latest version of AD Connect to synchronize Windows Active Directory with Azure AD. Support for synchronizing the on-premises group attributes required for these claims was added in version 1.2.70 (December 2018).
- In the Azure portal, signed in with a role capable of managing applications, go to the Azure Active Directory > Enterprise applications blade, and then select the application that you wish to configure for group claims.
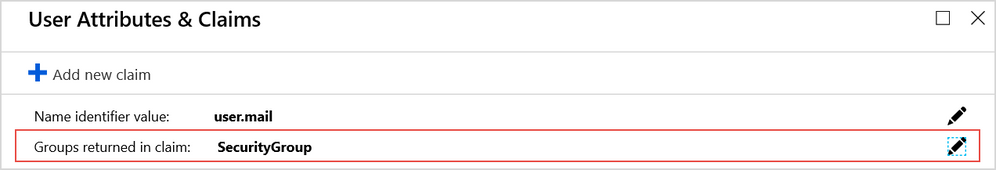
- Click Single sign-on and then User Attributes and Claims.
- Next to Groups returned in token, select the Edit
You can specify the groups that will be included in the token, the format that will be used, and you can customize the SAML attribute name for the group claims.
While OIDC/OAuth applications less commonly use this functionality, it’s also available in the application manifest in the Application Registration.
Our documentation for integrating an application that requires group claims with Azure AD covers both SAML and OIDC/OAuth.
Let us know what you think in the comments below. We’re always keen to hear any feedback or suggestions you have.
Best regards,
Alex Simons (@Alex_A_Simons )
Corporate VP of Program Management
Microsoft Identity Division
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.