- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Custom Roles in Azure RBAC is now GA!
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy Folks, Today I'm happy to be able to let you know that Custom Roles in Azure RBAC in now Generally Available! This is a BIG win for us and another big milestone in our efforts to make Azure the best cloud service for enterprises. To help you get up to speed on how you can create and use custom roles, I've asked Dushyant Gill, the PM in our team who owns our RBAC system, to do a detailed step by step blog post which you'll find below. I hope you'll find this new set of capabilities useful. And as always, we'd love to receive any suggestions or feedback you have. Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division -------------------------------
Greetings everyone,
I'm Dushyant Gill, one of the PMs on the identity team. I was here in October announcing the GA of Role-Based Access Control for Azure . Hot on the heels of the GA I'm happy to announce the availability of a new capability: custom roles.
Access control is likely one of the top things you care about as you start onboarding public cloud. With Azure AD you can control access to Azure cloud resources using your on-premises identity system – for example, ensuring that when emplopyees leave your organization they automatically lose access to company resources in Azure. And with Azure RBAC you can grant only the amount of access to users that they need to perform their jobs. To configure separation of authority you will mostly use the roles that come built-in with Azure RBAC. However, based on the way you manage Azure, you might need to grant certain people access to a set of hand-picked operations – like people who can monitor virtual machines and restart them but can't delete or create new ones. To achieve this, you can now create custom roles in Azure RBAC and specify the exact permissions that you wish to grant.
Use the Azure PowerShell tools or Azure Command-Line interface to create custom roles. And then grant least privilege access with your custom roles using the Azure management portal and command-line tools.
Access Management for Azure – Custom Roles (10 minutes)
Let's go through an example! Let's say my dev team has operators that can only monitor and restart virtual machines. To grant only the access that they need, I have created a custom role called Virtual Machine Operator. This role grants read permission to all resources in the Compute resource provider, and allows monitoring, starting, and restarting virtual machines. This role also grants read access to resources associated with virtual machines like Network and Storage.


Let me show you how to create this custom role.
To do this I will follow a best practice where I:
-
Find an existing built-in role whose permissions are closest to the permissions you wish to grant with the custom role.
-
Export its definition and add/remove permissions to arrive at the set desired for the custom role.
-
Create the custom role using the modified definition.
The closest built-in role in this case is Virtual Machine Contributor. So I begin by exporting it into a json role definition file using the Get-AzureRmRoleDefinition command of Azure PowerShell.

The exported json role definition file looks like this.

I'll modify this json file to arrive at the definition of Virtual Machine Operator custom role.
I start by removing the 'Id' and 'IsCustom' properties – they aren't required when creating a custom role. I then specify the display name and description of the new custom role in the 'Name', and 'Description' properties respectively.

Next, I modify the Actions property to grant only the permissions that are required to monitor and restart Virtual Machines, and to view the resources that are associated with Virtual Machines.
I make the following changes to the Actions property:
-
I grant read access to all Compute, Network, and Storage resource types by adding the following actions:
-
Microsoft.Compute/*/read
-
Microsoft.Network/*/read
-
Microsoft.Storage/*/read
-
-
I grant access to Start and Restart actions on Virtual Machines by adding the following actions
-
Microsoft.Compute/vrtualMachines/start/action
-
Microsoft.Compute/vrtualMachines/restart/action
-
-
No other actions from Compute, Network, and Storage resource provider are required – so I remove the following actions
-
Microsoft.Compute/availabilitySets/*
-
Microsoft.Compute/locations/*
-
Microsoft.Compute/virtualMachines/*
-
Microsoft.Compute/virtualMachineScaleSets/*
-
Microsoft.Network/applicationGateways/backendAddressPools/join/action
-
Microsoft.Network/loadBalancers/backendAddressPools/join/action
-
Microsoft.Network/loadBalancers/inboundNatPools/join/action
-
Microsoft.Network/loadBalancers/inboundNatRules/join/action
-
Microsoft.Network/loadBalancers/read
-
Microsoft.Network/locations/*
-
Microsoft.Network/networkInterfaces/*
-
Microsoft.Network/networkSecurityGroups/join/action
-
Microsoft.Network/networkSecurityGroups/read
-
Microsoft.Network/publicIPAddresses/join/action
-
Microsoft.Network/publicIPAddresses/read
-
Microsoft.Network/virtualNetworks/read
-
Microsoft.Network/virtualNetworks/subnets/join/action
-
Microsoft.Storage/storageAccounts/listKeys/action
-
Microsoft.Storage/storageAccounts/read
-
-
Virtual Machine Operators do not need to deploy using ARM templates so I remove the following action:
-
Microsoft.Resources/deployments/*
-
-
Virtual Machine Operators need to view resource groups, so I retain the following action:
-
Microsoft.Resources/subscriptions/resourceGroups/read
-
-
Virtual Machine Operators must be able to monitor virtual machines and create alert rules, so I retain the following action:
-
Microsoft.Insights/alertRules/*
-
-
Virtual Machine Operators must be able to view RBAC roles and role assignments, so I retain the following action:
-
Microsoft.Authorization/*/read
-
-
And finally, Virtual Machine Operators must be able to manage support tickets, so I retain the following action too:
-
Microsoft.Support/*
-

To figure out the actions strings for the start and restart operations of virtual machines, I use the Get-AzureRmProviderOperation command. This command provides a reference to all operations of all resource types across all resource providers of Azure.
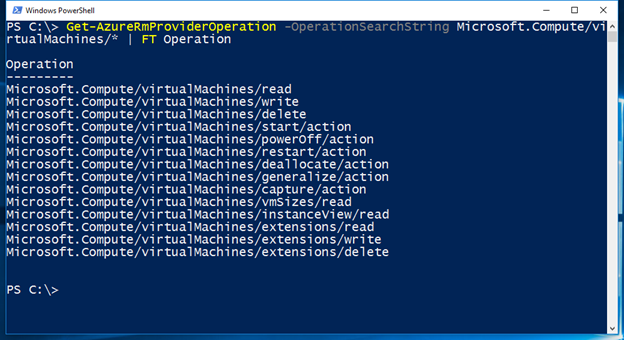
Finally, in the AssignableScopes property, I specify the Azure subscriptions in which I wish to manage access using this custom role. This capability lets me restrict where a custom role can be used. This custom role won't even appear in the list of assignable roles in subscriptions and resource groups that aren't specified here.

I use the Get-AzureRmSubscription command to determine the identifiers of my subscriptions.

My json role definition file for Virtual Machine Operator custom role is now ready.

I use the New-AzureRmRoleDefinition command to create the custom role.

That's how simple it is to create a custom role in Azure RBAC.
I use the new custom role to manage access to my Azure resources the same way I use the in-built roles of Azure RBAC. I select the access icon on the essentials pane of the subscription or resource group blade to bring up the Users blade. Then, I select the Add action to grant access.

I simply select the newly created custom role from the list.

Next, I select the user or group or application to which I wish to assign the custom role.

And that's how simple it is to grant access using custom roles!

Another neat feature we have added is the role-permissions view. This view makes it simple to understand the exact permissions that make up RBAC roles. I select the Roles action in the Users blade to bring up the list of RBAC roles and select the Permissions action of the role.

I see that the newly created custom role 'Virtual Machine Operator' grants partial access to 6 resource providers of Azure and full access to one.

I select the Microsoft Compute resource provider to see that the role grants read access to all its resource types and access to other actions on the Virtual Machine resource type. I select the Virtual Machine resource type to see that the role grants access to only the start and restart actions.

Finally, I see that the Stop and Delete action buttons of the virtual machine blade are hidden for users assigned to the Virtual Machine Operator role.

---
We hope that these updates make it simpler for you to secure your Azure cloud.
Learn more about custom roles at https://aka.ms/azurerbac#custom-roles-in-azure-rbac . Learn more about creating, modifying and deleting custom roles using Azure PowerShell and Azure Command-Line Interface tools.
As always, we would love to hear from you about your experience. Reach us on the Azure User Voice site – please prefix your suggestion with "Azure RBAC".
Dushyant Gill (@dushyantgill)
Program Manager, Azure Active Directory
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.