Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- #AzureAD Identity Protection, Azure AD Privileged Identity Management and Azure AD Premium P2 will be generally ava...
#AzureAD Identity Protection, Azure AD Privileged Identity Management and Azure AD Premium P2 will be generally available Sept 15th
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Published
Sep 07 2018 08:18 AM
42.5K
Views
Sep 07 2018
08:18 AM
Sep 07 2018
08:18 AM
First published on CloudBlogs on Sep, 07 2016
Howdy folks, Today we’ve got some cool news! Azure AD Identity Protection, Azure AD Privileged Identity Management and Azure AD Premium P2 are going to be Generally Available next Thursday 9/15! I’m incredibly excited about the work the teams are doing here. I hope you will be as well. Azure AD Identity Protection is a one of a kind cloud security service. It uses state of the art machine learning to analyze 10TB of behavioral and contextual data every day to detect and prevent attempts to attack your organizations Azure AD accounts. This level of account protection is pretty unprecedented – you can’t find it in the cloud or on-premises. Azure AD Privileged Identity Management is another first – the world’s first cloud based privileged identity management solution. With just a few clicks, you can dramatically increase the security of your Azure AD administrator accounts and improve your administrative compliance and auditing. Azure AD Premium P2 is a new SKU of Azure AD which includes all the capabilities in Azure AD Premium P1 as well as the new Identity Protection and Privileged Identity Management. It’s an incredible value and over the next 12 months will continue to get richer and richer as we add additional security and governance capabilities. To give you a detailed tour of both of these capabilities, I’ve asked Alex Weinert the Program Manager who leads our Identity Security and Protection team and Joseph Dadzie the Program Manager who leads our Identity Governance and Administration team to write up guest blog posts. You’ll fined them both below. I hope you’ll find these new capabilities valuable in securing your enterprises use of the cloud. And as always, we’d love to receive any feedback or suggestions you have. Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division -------------------- Once you have done that, you can click on the Azure AD Identity Protection tile. You’ll see this dashboard, which provides a consolidated view of risk data for your tenant – Users at risk of credential compromise, risk events which indicate anomalous logins or other indications of a bad login (or attempt), and vulnerabilities in your environment which you can address with configuration changes (like enrolling users for MFA, or reducing the number of admins in the environment), and help you set up risk-based Conditional Access policies to block attacks in realtime:
Once you have done that, you can click on the Azure AD Identity Protection tile. You’ll see this dashboard, which provides a consolidated view of risk data for your tenant – Users at risk of credential compromise, risk events which indicate anomalous logins or other indications of a bad login (or attempt), and vulnerabilities in your environment which you can address with configuration changes (like enrolling users for MFA, or reducing the number of admins in the environment), and help you set up risk-based Conditional Access policies to block attacks in realtime:

 You can see the specific users impacted and learn more about each type of event by drilling in on the specific item:
You can see the specific users impacted and learn more about each type of event by drilling in on the specific item:
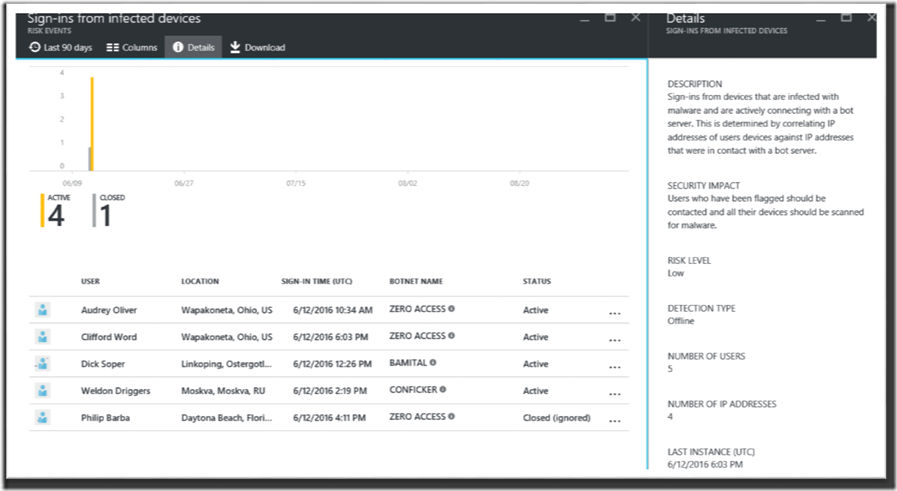 The key to making use these risk signals is to set Conditional Access policies that intercept bad actors with MFA challenges (or block them outright):
The key to making use these risk signals is to set Conditional Access policies that intercept bad actors with MFA challenges (or block them outright):
 In this case, any login from an anomalous location (I did this one using a TOR browser) will result in an MFA challenge, allowing good users but blocking cyber-criminals:
In this case, any login from an anomalous location (I did this one using a TOR browser) will result in an MFA challenge, allowing good users but blocking cyber-criminals:

 If you are looking into a specific user, you can see the Risk events that led to their risk state, enable MFA, or reset their password in line:
If you are looking into a specific user, you can see the Risk events that led to their risk state, enable MFA, or reset their password in line:
 As with Risk events, the best way to use User risk is to set up a risk-based Conditional Access policy to require that compromised credentials are mitigated with an MFA backed password reset or locked until they can be investigated:
As with Risk events, the best way to use User risk is to set up a risk-based Conditional Access policy to require that compromised credentials are mitigated with an MFA backed password reset or locked until they can be investigated:
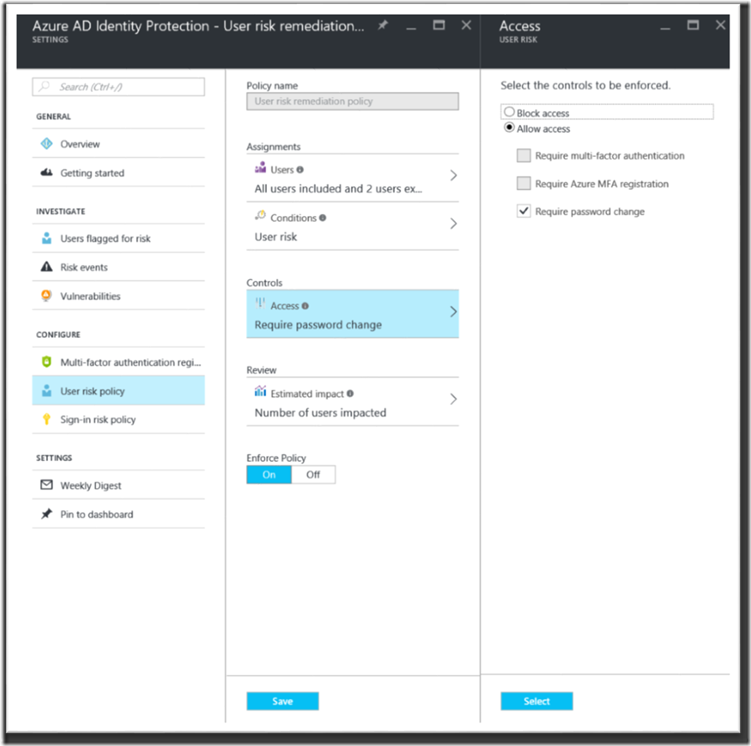 In this case we are requiring users at risk to change their passwords with an MFA challenge on next login – keeps the bad guys out, and lets good users retain control of their accounts!
First the user is told their account is at risk
In this case we are requiring users at risk to change their passwords with an MFA challenge on next login – keeps the bad guys out, and lets good users retain control of their accounts!
First the user is told their account is at risk
 Then they have to pass an Azure MFA challenge:
Then they have to pass an Azure MFA challenge:
 Then they can update their at risk password:
Then they can update their at risk password:


Howdy folks, Today we’ve got some cool news! Azure AD Identity Protection, Azure AD Privileged Identity Management and Azure AD Premium P2 are going to be Generally Available next Thursday 9/15! I’m incredibly excited about the work the teams are doing here. I hope you will be as well. Azure AD Identity Protection is a one of a kind cloud security service. It uses state of the art machine learning to analyze 10TB of behavioral and contextual data every day to detect and prevent attempts to attack your organizations Azure AD accounts. This level of account protection is pretty unprecedented – you can’t find it in the cloud or on-premises. Azure AD Privileged Identity Management is another first – the world’s first cloud based privileged identity management solution. With just a few clicks, you can dramatically increase the security of your Azure AD administrator accounts and improve your administrative compliance and auditing. Azure AD Premium P2 is a new SKU of Azure AD which includes all the capabilities in Azure AD Premium P1 as well as the new Identity Protection and Privileged Identity Management. It’s an incredible value and over the next 12 months will continue to get richer and richer as we add additional security and governance capabilities. To give you a detailed tour of both of these capabilities, I’ve asked Alex Weinert the Program Manager who leads our Identity Security and Protection team and Joseph Dadzie the Program Manager who leads our Identity Governance and Administration team to write up guest blog posts. You’ll fined them both below. I hope you’ll find these new capabilities valuable in securing your enterprises use of the cloud. And as always, we’d love to receive any feedback or suggestions you have. Best regards, Alex Simons (Twitter: @Alex_A_Simons ) Director of Program Management Microsoft Identity Division --------------------
Azure AD Identity Protection
Hey there! My name is Alex Weinert and I am the Group Program Manager for the Microsoft Identity Security and Protection team – here to let you know that Azure Active Directory Identity Protection will be generally available on September 15 th ! This is available in the Azure Active Directory Premium 2 offering in combination with Azure Active Directory Privileged Identity Management , and together offer advanced protection which will help you establish Conditional Access policies which automatically defend against attempted account takeover, and which help you minimize admin attack surface area to ensure you have the best security posture possible. I talk about both of these in a Microsoft Mechanics video on Azure AD Identity Protection and Privileged Identity management. It has been an exciting year in account security – so many accounts credentials leaked (learn more in the Microsoft Security Incident Report ), and some remarkably high profile data leaks to point to as a result (here’s just one example – the Guccifer 2.0 DNC leak ), it is clear that account security and protection is absolutely critical for your enterprise. Azure AD Identity Protection brings together the power of our threat analytics, Conditional Access, and Multi-Factor Authentication to significantly enhance your security posture. We see a lot of threat data! A few notable signal sources:- User behavior data from 14 billion daily authentication events each day
- Attacker behavior data from millions of attacks each day
- Threat data from applications, industry partners, researchers, law enforcement and industry
- Botnet data from Microsoft’s Digital Crimes Unit
- Malware information from the Windows Defender team
Overview
You can enable Azure AD Identity Protection by going to the Azure Marketplace at http://portal.azure.com , and just search for “identity protection”: Once you have done that, you can click on the Azure AD Identity Protection tile. You’ll see this dashboard, which provides a consolidated view of risk data for your tenant – Users at risk of credential compromise, risk events which indicate anomalous logins or other indications of a bad login (or attempt), and vulnerabilities in your environment which you can address with configuration changes (like enrolling users for MFA, or reducing the number of admins in the environment), and help you set up risk-based Conditional Access policies to block attacks in realtime:
Once you have done that, you can click on the Azure AD Identity Protection tile. You’ll see this dashboard, which provides a consolidated view of risk data for your tenant – Users at risk of credential compromise, risk events which indicate anomalous logins or other indications of a bad login (or attempt), and vulnerabilities in your environment which you can address with configuration changes (like enrolling users for MFA, or reducing the number of admins in the environment), and help you set up risk-based Conditional Access policies to block attacks in realtime:

Risk Events
The Risk events view lets you see specific login issues, such as users logging in from anomalous locations, botnet infected devices or anonymizing locations (like TOR networks) associated with account hijacking risk. Additionally, you can see logins where we have found matching credentials for your tenant “in the wild” – for sale on a pastebin site, or attempted against one of our systems in an at-scale attack: You can see the specific users impacted and learn more about each type of event by drilling in on the specific item:
You can see the specific users impacted and learn more about each type of event by drilling in on the specific item:
 The key to making use these risk signals is to set Conditional Access policies that intercept bad actors with MFA challenges (or block them outright):
The key to making use these risk signals is to set Conditional Access policies that intercept bad actors with MFA challenges (or block them outright):
 In this case, any login from an anomalous location (I did this one using a TOR browser) will result in an MFA challenge, allowing good users but blocking cyber-criminals:
In this case, any login from an anomalous location (I did this one using a TOR browser) will result in an MFA challenge, allowing good users but blocking cyber-criminals:

User Risk
The Users view lets you see the state of any user currently at risk, or who had a risk event in the previous 90 days. If you are looking into a specific user, you can see the Risk events that led to their risk state, enable MFA, or reset their password in line:
If you are looking into a specific user, you can see the Risk events that led to their risk state, enable MFA, or reset their password in line:
 As with Risk events, the best way to use User risk is to set up a risk-based Conditional Access policy to require that compromised credentials are mitigated with an MFA backed password reset or locked until they can be investigated:
As with Risk events, the best way to use User risk is to set up a risk-based Conditional Access policy to require that compromised credentials are mitigated with an MFA backed password reset or locked until they can be investigated:
 In this case we are requiring users at risk to change their passwords with an MFA challenge on next login – keeps the bad guys out, and lets good users retain control of their accounts!
First the user is told their account is at risk
In this case we are requiring users at risk to change their passwords with an MFA challenge on next login – keeps the bad guys out, and lets good users retain control of their accounts!
First the user is told their account is at risk
 Then they have to pass an Azure MFA challenge:
Then they have to pass an Azure MFA challenge:
 Then they can update their at risk password:
Then they can update their at risk password:

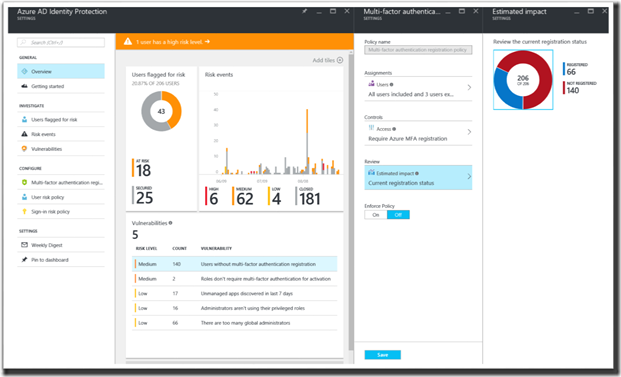
Vulnerabilities
The third major value that Azure AD Identity Protection provides is a consolidated view of configuration issues in your environment. The dashboard provides a consolidated view of configuration and policy issues, and provides recommendations for remediation. This includes data from Azure AD Privileged Identity Management, MFA, and other areas so you can get an “at a glance” view of ways to improve your security posture. One major item is MFA readiness – MFA is a valuable way to improve both your security posture and your user experience (by allowing self-help). In this case, we are showing you the impact analysis available in all policies. These allow you to easily understand how the policy will affect your users.
APIs!
One thing we hear from our customers is that they are excited about the signals we offer, but would like to find ways to integrate them into their existing SIEM or analytics systems. This is all detailed in our blog on Azure AD Identity Protection APIs . There’s some very cool stuff you can do – here’s a screenshot of using the data to do investigations in PowerBI, but with the API, the world is your oyster!
Get Started!
We are really fired up about Azure AD Identity Protection and can’t wait to hear what you think! Learn more here , and feel free to reach out to me on Twitter at @alex_t_weinert – thanks, and stay safe! -------------Azure AD Privileged Identity Management
Hello, My name is Joseph Dadzie and I lead our Identity Governance and Administration PM team in Microsoft’s Identity Division. I'm excited to announce that Azure Active Directory Privileged Identity Management (Azure AD PIM) service will be generally available on September 15th as part of our new offering Azure Active Directory Premium P2! Traditionally, both on-premises and in the cloud, most IT admins have needed to have permanent and unmonitored permissions to high-value resources in order to do their jobs. This is convenient, but it poses major security concerns because their user accounts become high-value targets for security attacks. In many recent high-profile security breaches, a hacker found a way to use side-ways elevation of privileges until they were able to compromise a user account with permanently assigned privileged roles. Then the attacker used that account to access resources across the organization’s network, in many cases going undetected for months. The Azure AD Privileged Identity Management service enables organizations to reduce risks associated with privileged users and their access rights, by helping them:- Discover who the most privileged users in their tenants are, across Azure Active Directory, Office365, Intune and other services, with a dashboard, APIs and notifications of new role assignments
- Reduce the exposure of these privileged users to the risk of attack, converting them from permanent role assignment to being eligible for "Just in time" role activation
- Enable Just-In-Time (JIT) privileged role assignment, for eligible privileged users to request permissions, with policies to require Multi-Factor Authentication (MFA) or trouble ticket numbers, send notifications, and limit the time the user is in the role.
4. Retrieve alerts and audit reports for tracking and monitoring privileged users' assignments and activations
- Conduct access reviews of privileged user accounts by admins or designated reviews to assure the admins continue to require access to privileged roles and access permissions.
Throughout the public preview of Azure AD PIM, we have had many enterprises and partners try out PIM and given us great feedback.
Here’s some real data showing how much one of our large enterprise customers reduced the risk of persistent privileged accounts by using Azure AD Privileged Identity Management:
You can also realize some of the benefits to your organization of Privileged Identity Management by enabling PIM on your tenant. You can do so through the administrative UI in the Azure Portal, through APIs in the Microsoft Graph or PowerShell cmdlets . To try out Azure AD PIM today follow the instructions here to enable it on your tenant. For more information about PIM and how it can help you secure your organization, read more here . You can also learn more about the features in each edition of Azure AD at Azure Active Directory pricing . Thank you and I’m looking forward to your feedback and suggestions! Joseph Dadzie Lead PM Identity Governance and Administration
0
Likes
4 Comments
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.







