- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Azure Active Directory Activity logs in Azure Log Analytics now available
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
As more and more of you adopt Azure Active Directory (AD)—the service now manages 1.1 BILLION (!!!) identities—we’ve received a ton of requests to make it easier to access and analyze the huge amounts of data the service creates on your behalf. You’ve told us you need access to all this data to do all kinds of analytics for business, operations, and security processes, and to also monitor Azure AD as a critical component of your infrastructure.
Today, I’m excited to announce the availability of one of our top-requested features: the ability to forward your Azure AD logs to Azure Log Analytics! With this integration, Log Analytics gives you the power to query huge amounts of your Azure AD data to find events, analyze trends, and create rich visualizations within minutes.

This integration gives you the richness of data available through Azure AD logs to resolve cross-service scenarios. For example:
- As an IT admin, you can easily troubleshoot key issues in your tenant and monitor them through alerts and notifications. For example, you can identify users or apps that use legacy auth sign-ins or generate an alert to notify you when a high-risk user using legacy auth sign-ins.
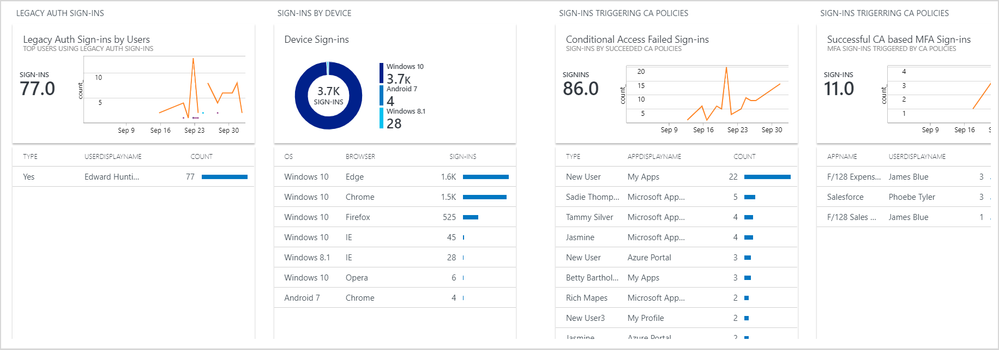
- As a SecOps admin, you can easily correlate sign-in activities of your users or apps in your tenant with any CRUD operations performed to get a complete picture of what’s going onwith your Azure resources.
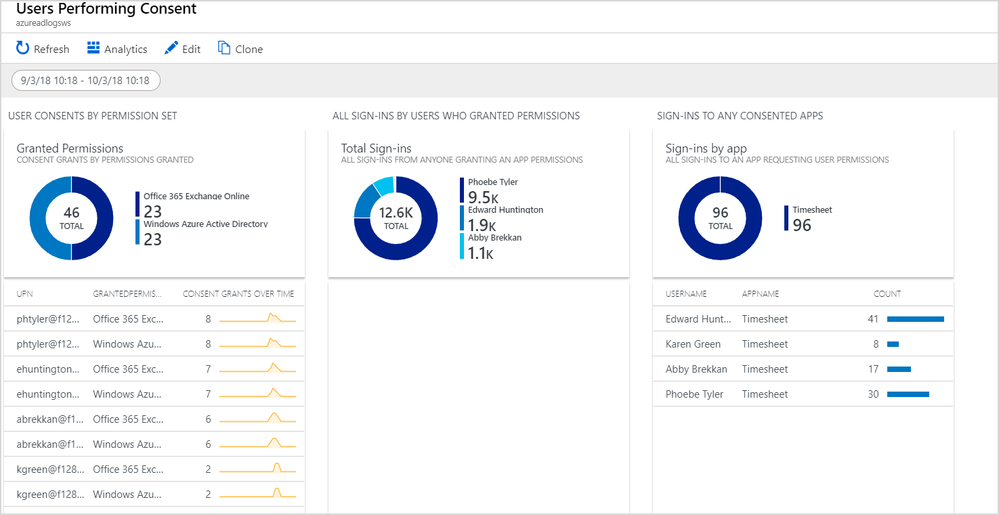
- As an Application owner, you can troubleshoot that nagging performance bottleneck on your app’s sign-in page by correlating application performance data from Azure Application Insights
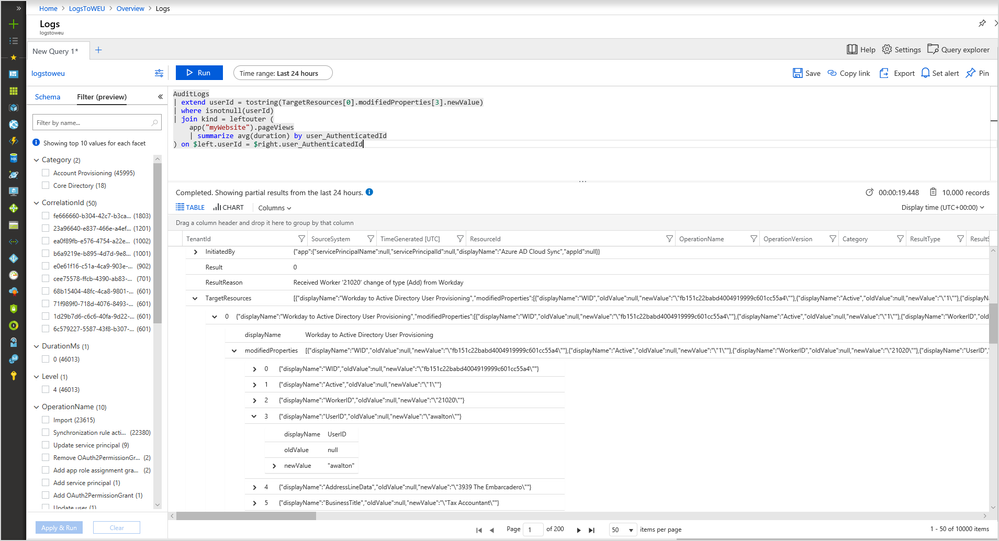
- As a Security admin, you now can use the Azure AD sign-in and audit logs in tandem with security logs published by Azure Security Center to assess the impact and scope of a security breach by analyzing all the user activities performed, thereby, giving answers to questions like: “What did this user access while the breach happened?” and “What resources does the user have access to?”
- As an IT admin interested in governance, risk management, or compliance, you can get a clear view into how users are getting access. For example, are they being added to groups by admins, or by group owners, or due to changes in the user or group attributes? You can leverage this history of identity and access changes, with the details of the dates, times, and actors for each, to respond to auditor inquiries. And you can set up alerts, so you and your colleagues are notified whenever users are added to highly sensitive groups. With this data you can ensure that the correct identity and access lifecycle processes are being followed to meet the organization’s identity governance policies.
In addition to the above scenarios, customers now can get the Azure AD logs in the same workspace where they have their Azure logs, as well as other logs (like Office 365), to perform a broader analysis and successful monitoring of their infrastructure.
Learn more
To learn more about forwarding Azure AD logs to Azure Log Analytics, check out these resources:
- Configure Log Analytics through Azure Monitor—Find out how to configure Log Analytics for Azure AD logs.
- Sample queries for Azure AD logs—Check out some sample Log Analytics queries on Azure AD data.
- Log Analytics and the KQL query language reference—Query language reference documentation.
- Pre-built dashboards and Views—Check out the cool pre-built views built on key Azure AD scenarios.
- Power of Log Analytics—Build your own dashboards, create alerts, or programmatically access the data and queries on top of it.
Once you try out the integration of Azure AD logs with Log Analytics, give us your valuable feedback on the either the Azure AD Tech Community or Log Analytics Tech Community. You can also let us know what you think in the comments below. As always, we’d love to hear any feedback or suggestions you have.
Best regards,
Alex Simons (@Alex_A_Simons )
Corporate VP of Program Management
Microsoft Identity Division
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.