- Home
- Security, Compliance, and Identity
- Microsoft Entra Blog
- Announcing the public preview of Azure AD support for FIDO2-based passwordless sign-in
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Howdy folks,
I’m thrilled to let you know that you can now go passwordless with the public preview of FIDO2 security keys support in Azure Active Directory (Azure AD)! Many teams across Microsoft have been involved in this effort, and we’re proud to deliver on our vision of making FIDO2 technologies a reality to provide you with seamless, secure, and passwordless access to all your Azure AD-connected apps and services.
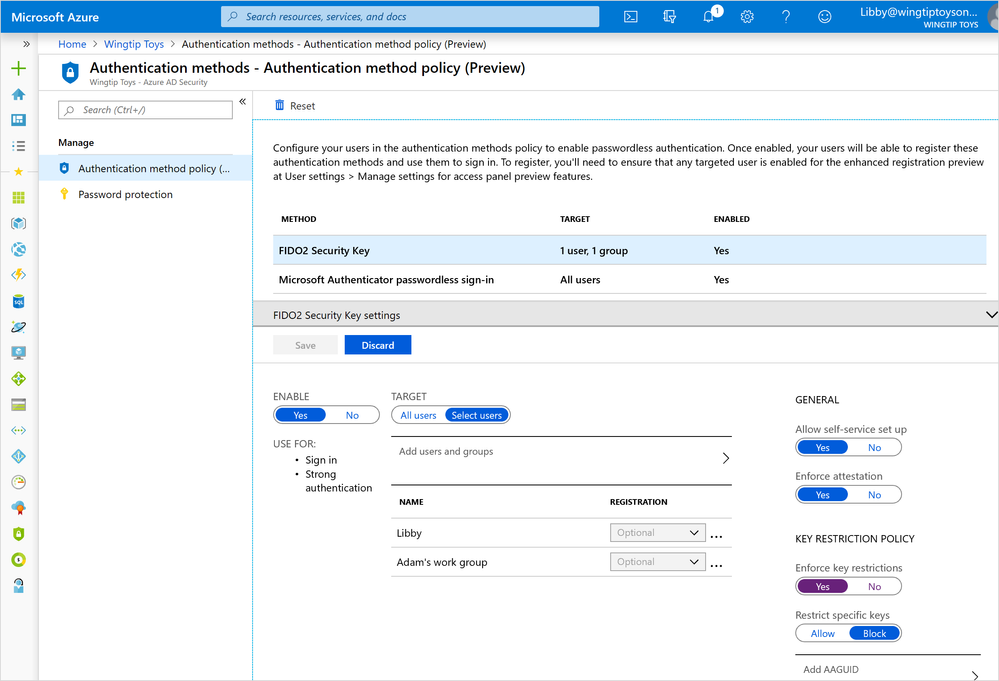
In addition, we turned on a new set of admin capabilities in the Azure AD portal that enable you to manage authentication factors for users and groups in your organization. In this first release, you can use them to manage a staged rollout of passwordless authentication using FIDO2 security keys and/or the Microsoft Authenticator application. Going forward you’ll see us add the ability to manage all our traditional authentication factors (Multi-Factor Authentication (MFA), OATH Tokens, phone number sign in, etc.). Our goal is to enable you to use this one tool to manage all your authentication factors.
Why do we feel so strongly about passwordless?
Every day, more and more of our customers move to cloud services and applications. They need to know that the data and services stored in these services are secure. Unfortunately, passwords are no longer an effective security mechanism. We know from industry analysts that 81 percent of successful cyberattacks begin with a compromised username and password. Additionally, traditional MFA, while very effective, can be hard to use and has a very low adoption rate.
It’s clear we need to provide our customers with authentication options that are secure and easy to use, so they can confidently access information without having to worry about hackers taking over their accounts.
This is where passwordless authentication comes in. We believe it will help to significantly and permanently reduce the risk of account compromise.
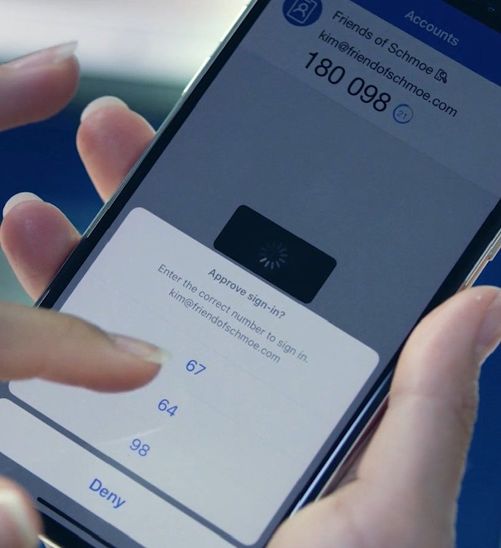
Now, all Azure AD users can sign in password-free using a FIDO2 security key, the Microsoft Authenticator app, or Windows Hello. These strong authentication factors are based off the same world class, public key/private key encryption standards and protocols, which are protected by a biometric factor (fingerprint or facial recognition) or a PIN. Users apply the biometric factor or PIN to unlock the private key stored securely on the device. The key is then used to prove who the user and the device are to the service.
Check out this video where Joy Chik, corporate vice president of Identity, and I talk more about this new standard for signing in. To learn more about why this should be a priority for you and your organization, read our whitepaper.
Let’s get you started!
To help you get started on your own passwordless journey, this week we’re rolling out a bonanza of public preview capabilities. These new features include:
- A new Authentication methods blade in your Azure AD admin portal that allows you to assign passwordless credentials using FIDO2 security keys and passwordless sign-in with Microsoft Authenticator to users and groups.
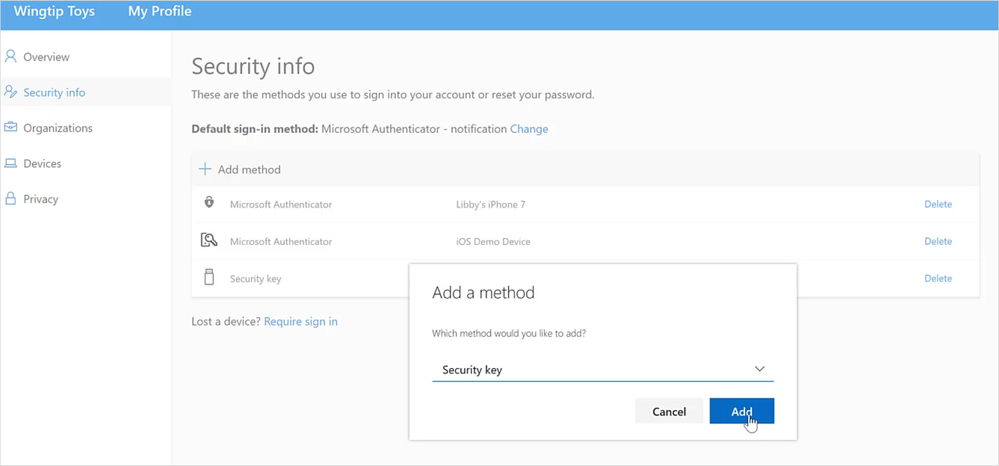
- Updated capabilities in the converged Registration portal for your users to create and manage FIDO2 security keys.
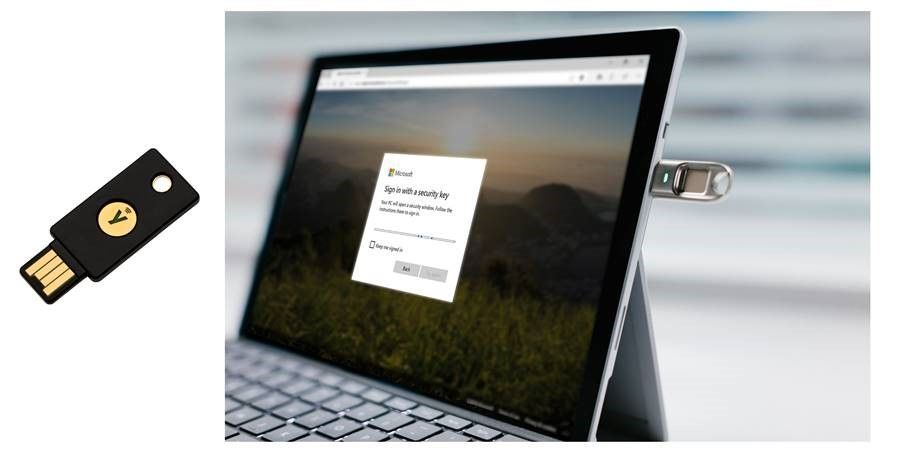
- Ability to use FIDO2 security keys to authenticate across Azure AD-joined Windows 10 devices on the latest versions of Edge and Firefox browsers.
FIDO2 hardware
Microsoft has teamed up with leading hardware partners, Feitian Technologies, HID Global, and Yubico, to make sure we have a range of FIDO2 form factors available at launch, including keys connecting via USB and NFC protocols. Sue Bohn has more details on those partnerships.
Please be sure to verify that any FIDO2 security keys you’re considering for your organization meet the additional options required to be compatible with Microsoft’s implementation.
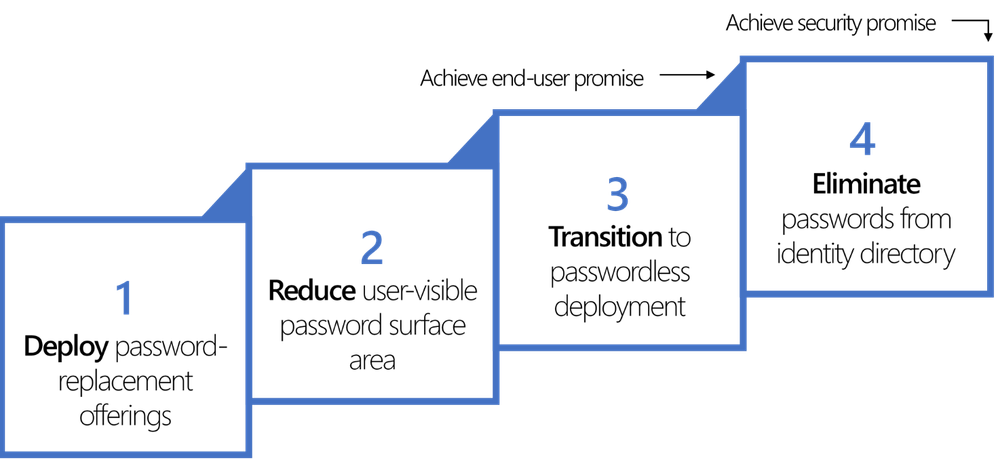
Our passwordless strategy
Our passwordless strategy is a four-step approach where we deploy replacement offerings, reduce the password surface area, transition to passwordless deployment, and finally eliminate passwords:
Today’s product launches are an important milestone for getting to passwordless. In addition, the engineering work we did to provide authentication methods management for administrators and user registration and management, will allow us to move even faster to improve credentials management experiences, as well as bring new capabilities and credentials online more simply. We’re working with our Windows security engineering team to make FIDO2 authentication work for hybrid-joined devices.
Of course, we look forward to feedback from you across all of these features, to help us improve before we make them generally available.
Regards,
Alex (Twitter: @Alex_A_Simons)
Corporate VP of Program Management
Microsoft Identity Division
Additional links
- « Previous
-
- 1
- 2
- Next »
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.